
A TOUCH IS WORTH A THOUSAND CLICKS
Zoe Antoniou
Nokia Research Centre Cambridge, 3 Cambridge Centre, Cambridge, MA, 02142, USA
Keywords: Intuitive user interaction, middleware, pervasive computing, RFID, NFC, UPnP.
Abstract: The fusion of interaction and discovery technologies can facilitate easy, intuitive and impromptu access to
networked entities by users without the need for significant administrative overhead. Due to mobility,
complex connectivity and small user interfaces, traditional service discovery methods fail to meet the
demands placed by such environments. This paper presents work-in-progress on how NFC-enhanced
mobile devices can enable intuitive service discovery by non-expert users in smart environments through
simple gestures such as touch. With this new paradigm, physical space becomes an extension of the
traditional GUI. An extensible RFID tag record is presented that can be utilised in a variety of scenarios.
The proposed approach is further illustrated through a technical realisation based on the UPnP framework.
An example use case is selected and the step-by-step process of service discovery and user interaction is
described.
1 INTRODUCTION
The increasing penetration of short-range wireless
access mobile devices and the introduction of
networked environments are giving rise to new user
interaction and service models. These models
emerge as homes and workplace environments are
gradually being transformed into smart spaces
populated with a diverse set of devices and
applications all waiting to be accessed and used. The
trend for such spaces is to provide intelligent, I-
centric service architectures. I-centric
communication considers the human behaviour as a
starting point to adapt the activities of
communication systems to it rather than being
unaware of user needs and situations. Discovery and
interaction technologies can be combined to create a
consistent user experience that significantly reduces
the administrative and configuration overhead.
Meeting these requirements poses a number of
logistical and technical challenges. Due to mobility,
more complex connectivity, small user interfaces
(UIs) and limited text input, issues such as mobile
service configuration, discovery and activation will
have to take a different path to success than the
desktop devices. In this setting, object tagging is a
powerful concept for grounding immaterial mobile
services in the real world. Radio Frequency
Identification (RFID) has received tremendous
attention lately as a promising technology for smart
space object tagging and an important enabler in the
mobile terminal business. RFID tags based on the
Near Field Communication (NFC) technology have
a modifiable state and a short operating range. These
tags can be interpreted by middleware and relevant
applications running on the mobile device itself.
This is different from Electronic Product Code
(EPC) technology. EPC tags are typically simple
object IDs with a reading range of the order of
meters, and EPC readers need to access a backbone
infrastructure in order to interpret them
semantically.
This paper proposes a method that extends the
concept of user-to-device interaction beyond the
limitations of the traditional GUI interface and
provides easy service discovery and launching. In
the new interaction paradigm, user input can be
received through touch in the same way as it is
received through mouse clicks and menu selections.
As a result, physical space becomes an extension to
the mobile device GUI and physical objects can be
mapped to virtual objects. Discovery does not
require detailed knowledge of local network
configuration or service initiation processes. An
object may be selected, clicked upon or dropped on
different application icons depending on the user’s
250
Antoniou Z. (2006).
A TOUCH IS WORTH A THOUSAND CLICKS.
In Proceedings of the International Conference on Wireless Information Networks and Systems, pages 250-257
Copyright
c
SciTePress

intentions and different actions are invoked. For
instance, if a user selects a picture on mobile phone
X and then touches mobile phone Y, it is interpreted
as the user’s intent to share the image. If a user
selects a picture on a mobile phone and then touches
a printer, it is interpreted as the user’s intent to print
it.
The successful deployment of such pervasive
computing environments will rely on the promptness
of the self-configuring procedures and the ease of
use of the discovery process for the average user.
Many technologies were originally developed for
zero-configuration networks in controlled and
familiar environments (e.g. home, office). Recent
research has focused on the use of these
technologies in mobile computing scenarios. Some
well-known service discovery protocols are Service
Location Protocol (SLP, by IETF), Jini (a Java-
based approach by Sun), Universal Plug and Play
(UPnP, by Microsoft) and Bluetooth Service
Discovery Protocol (SDP). Currently, these
technologies lack the ability to ensure independence
from the networking layer, interoperability between
devices of different manufacturers, and cannot
provide a complete solution for the easy, secure and
intuitive interaction between non-expert users and
services:
• They require manual intervention and are
typically deployed in traditional network
topologies where trained users work through
powerful hosts (Heidermann, 1998), (Misra,
2001).
• Discovering services often implies performing
multicast searches over wireless interfaces.
Potentially, this can result in long lists of
available services and devices.
• Even in cases where the user has identified the
type or friendly name for a service, a search
may still be necessary in order to launch it.
• The user is required to setup suitable network
access in order to reach the desired service.
The proposed approach enables a non-expert user to
discover and use the desired service through a one-
step process by touching dedicated service access
points, thus, eliminating the need for multiple
manual steps and multicast searches.
The paper is organised as follows. Section 2
gives a brief overview of the NFC technology.
Section 3 summarises prior literature. Section 4
introduces an interaction model based on the touch
paradigm and discusses its role as a powerful
enabler in mobile terminal services. Section 5
presents the service discovery approach, the NFC
tag record structure and the technical realization
through the UPnP framework. Finally, section 6
concludes the paper.
2 WHY NFC TECHNOLOGY?
Though RFID technology has, traditionally, been
used in industrial and logistics-related applications,
it is well suited for automatic service discovery and
configuration. User applications have been limited,
focusing on payments at points-of-sale and
contactless public transport tickets. Nokia, Philips
and Sony recently established the Near Field
Communication (NFC) Forum to promote the use of
contact-less short-range technologies in a variety of
consumer applications (NFC Forum). Bringing two
NFC devices together should engage the wireless
devices’ interfaces so that they can (a) exchange
data purely over NFC or (b) exchange configuration
parameters in order to link in a peer-to-peer network
over another wireless medium. A proximity RFID
technology operating at the unregulated band of
13.56 MHz with an operating distance of 0-10cm
has been chosen. Reasons for this include
compatibility with existing payment and ticketing
solutions, maturity and availability of technology
and parameters, such as size and power
consumption. Due to the very short operating range
the usage paradigm of such NFC systems resembles
a touch gesture. Technology miniaturization makes
it feasible to integrate NFC functionality into
consumer products and mobile devices and it is well
positioned to revolutionise the user experience.
3 RELATED WORK
This section summarises selected publications in the
area of RFID-enhanced service discovery. One
approach has been to explore the integration of
RFID technology with Web services. In (Kerer) the
authors present a presence-aware infrastructure in
order to implement a committee meeting scenario.
RFID tags are attached to the devices of the meeting
attendees and they are detected when they enter the
meeting room. The information on the tags is used
as input to the presence manager, the authentication
and personalization services and the persistent
repository, all of which create a collaborative
A TOUCH IS WORTH A THOUSAND CLICKS
251

environment. In (Romer, 2003) the authors analyse
example use cases such as Smart Tool Box, Smart
Medicine Cabinet, Smart Agenda, RFID Chef and
Smart Playing Cards in order to extract generic
design concepts. They present two prototype
frameworks based on Jini and Web services. Tags
are attached to physical objects which hold pointers
to their virtual counterparts. The prototype
architecture uses RFID interfaces to periodically
scan the surroundings for tagged objects. When a
tagged object is detected, it is registered, mapped to
its virtual counterpart, its activity is logged and
associated executables are run based on the
application. Though there are several similarities,
both (Kerer) and (Romer, 2003) focus on a very
different usage model than the one proposed in this
paper, which is driven by explicit user actions.
The proposed approach in this paper is closely
aligned with (but independently explored from)
Elope as described in (Pering, 2005). Both
architectures investigate how RFID-enhanced
physical objects can be discovered and their
associated services launched through RFID-
enhanced mobile devices. One distinct difference is
that Elope focuses on a web-based service discovery
framework, whereas this paper integrates RFID
technology with the UPnP framework. Again, the
details of the data representation on the tag are not
discussed in (Pering, 2005).
In (Bettstetter, 2000) mobile devices act as the
mediator between the user and RFID-augmented
physical objects. The tags contain data that trigger
context events in the system (referred to as
CAPNET-based middleware). The primary focus of
(Bettstetter, 2000) is on usability tests, the users’
perception of visually marked RFID tags, the social
acceptance of a touch-based interaction model, and
the users’ feedback on security concerns and the
user interface. This paper places a stronger emphasis
on the design of the middleware architecture, the
technical realization through the UPnP technology
and the details of the data representation on the tag
for network connectivity and service discovery (an
aspect not addressed in (Bettstetter, 2000)).
Passive RFID tags and Bluetooth nodes are used
in (Siegemund, 2003) to augment everyday products
and objects. Bluetooth nodes are attached to RFID
scanners and they are used as mobile access points
allowing data stored on a passive tag (e.g. product
codes) to access the background infrastructure in
order to be semantically interpreted. The focus of
(Siegemund, 2003) is on logistics-driven use cases
such as Smart Product Monitoring, Smart Medicine
Cabinet and Remote Interaction with Smart Objects
and Locations. In contrast, this paper focuses on
consumer-driven services such network access,
printing, faxing, teleconferencing and so on.
In (Ravendy) the authors present a middleware
platform, referred to as MSDA, that manages the
dynamic composition of networks, integrates
existing middleware protocols (e.g. Jini, UPnP), and
provides a generic service to clients for performing
service discovery. MSDA-aware clients can connect
with services in different discovery domains through
ad-hoc networks, hotspots or Internet/Cellular
networks. The intended user interaction model is
different from the proposed method in this paper. In
(Ravendy) users can discover a new service by
reading an RFID tag but additional manual steps are
necessary. The user needs to initiate a search for an
available service in the network that can interpret
and process the description read from the RFID tag.
The type of RFID technology used and the tag data
representation are not discussed.
An RFID-enhanced framework for intelligent
products is presented in (Bajic). The key
technologies utilised are RFID and UPnP as in this
paper. The focus, though, is on logistics and
production processes and the RFID technology is
based on EPC standards. Objects are enhanced with
UPnP functionality. RFID sensing or direct UPnP
message exchange invokes the service discovery
process by providing the object ID. The example
case study is a warehouse management system.
In (Want, 1999) RFID tags of very small
capacity (a few bytes) are affixed to physical objects
containing a simple ID. The tag reader scans the
object ID, determines the current application context
and provides the appropriated feedback. The use
cases focus on how RFID-enhanced objects can be
used to present information on a wireless handheld
device. However, this approach does not enable
services to access data stored in mobile devices.
4 THE TOUCH PARADIGM
Users do not want to employ technology but rather
to interact with their environment. Even though
mobile phones have become a commodity, a major
part of mobile applications and services is hardly
used by today’s consumers. For example, basic
functions such as calling or text messaging are easy
WINSYS 2006 - INTERNATIONAL CONFERENCE ON WIRELESS INFORMATION NETWORKS AND SYSTEMS
252

to use and have been widely adopted. In contrast,
browsing or file sharing require complex
configurations and setup procedures and are less
popular at present. In this work:
The touch paradigm creates an intuitive user
interaction model. It allows for fast, convenient and
intuitive user interaction with smart objects, devices,
services and other users.
Service discovery provides a unique
opportunity to boost the adoption of mobile services,
in particular wireless proximity services. Rather than
require new models of behaviour, social interaction
in proximity can build on familiar human activities
such as giving, sharing, greeting, self-expression,
acknowledgement and so on.
4.1 Context Awareness
User activities in proximity can exploit the benefits
of context information relevant to service discovery.
Context information enables the right services to be
delivered to the right user at the right time. Objects
pertaining to a certain context can be active or
passive at given moments in time depending on the
situation of the user. Proximity-based services can
be categorised in four context-aware categories:
a) People in places: social interaction,
communication and collaboration in close physical
range. Example applications are face-to-face content
sharing, ad-hoc collaboration and group formation.
b) Me and my stuff: creation, management
and storage of personal and 3
rd
party content with
particular focus on the home environment. For
example, personal mobile devices (e.g. phones,
PDAs) can access and control services and content
on networked home devices (e.g. laptop, audio
system, home appliances).
c) Smart spaces: accessing local content and
services relevant to a particular location. Location-
based services can find application both in the
workplace and in the consumer market. For the
former, an example is personal mobile devices
discovering and interacting with other devices in a
specific room or building (e.g. printers, projectors).
Examples for the latter are service activation at
point-of-sale locations and content download (e.g.
download a movie preview from a poster).
d) Safe consumption: research and purchase
of goods, content and services with perceived
security and trust. All transactions have security and
privacy requirements but special attention is needed
when purchases and monetary transactions are
involved such as ticketing and electronic wallet
applications.
Location is an important element of context
information that can be exploited. NFC technology
can provide a convenient way to access location-
aware, mobile services and content through hot
spots, e.g. NFC-equipped devices could easily read
tags at point-of-sale locations. This can serve to
compliment cellular coverage and provide the
illusion of full mobility, thus, making it less
necessary to assure real-time full mobility for all
applications. Yet, commercial success of this
business model is dependent on whether users are
willing to wait to connect, pricing and sufficient
coverage with clearly marked hot spots.
4.2 UI Interaction
Enabled by NFC technology, service discovery has a
direct impact on the design of smart and intuitive
user interfaces (UIs) for pervasive computing.
Currently, similar point-and-click interfaces are not
flexible. Most RFID readers, bar code scanners and
IR remote controls are single purpose devices. In
some cases, IR can be used for multiple purposes,
but the interface can hardly be characterized as
intuitive, or point-and-click.
Traditional graphical user interface displays
receive input through mouse clicks and menu
selections. With the NFC-touch paradigm the
physical space (e.g. a room) becomes an extension
to the GUI of a mobile device, where physical
objects (i.e. NFC-enabled objects and devices) can
be touched upon in order to activate associated
services and applications in the same manner as
clicking on an icon on a conventional display. An
object may be selected, clicked upon or dropped on
different applications, which invokes different
actions. Three key modes of interaction are shown in
Table 1.
A TOUCH IS WORTH A THOUSAND CLICKS
253
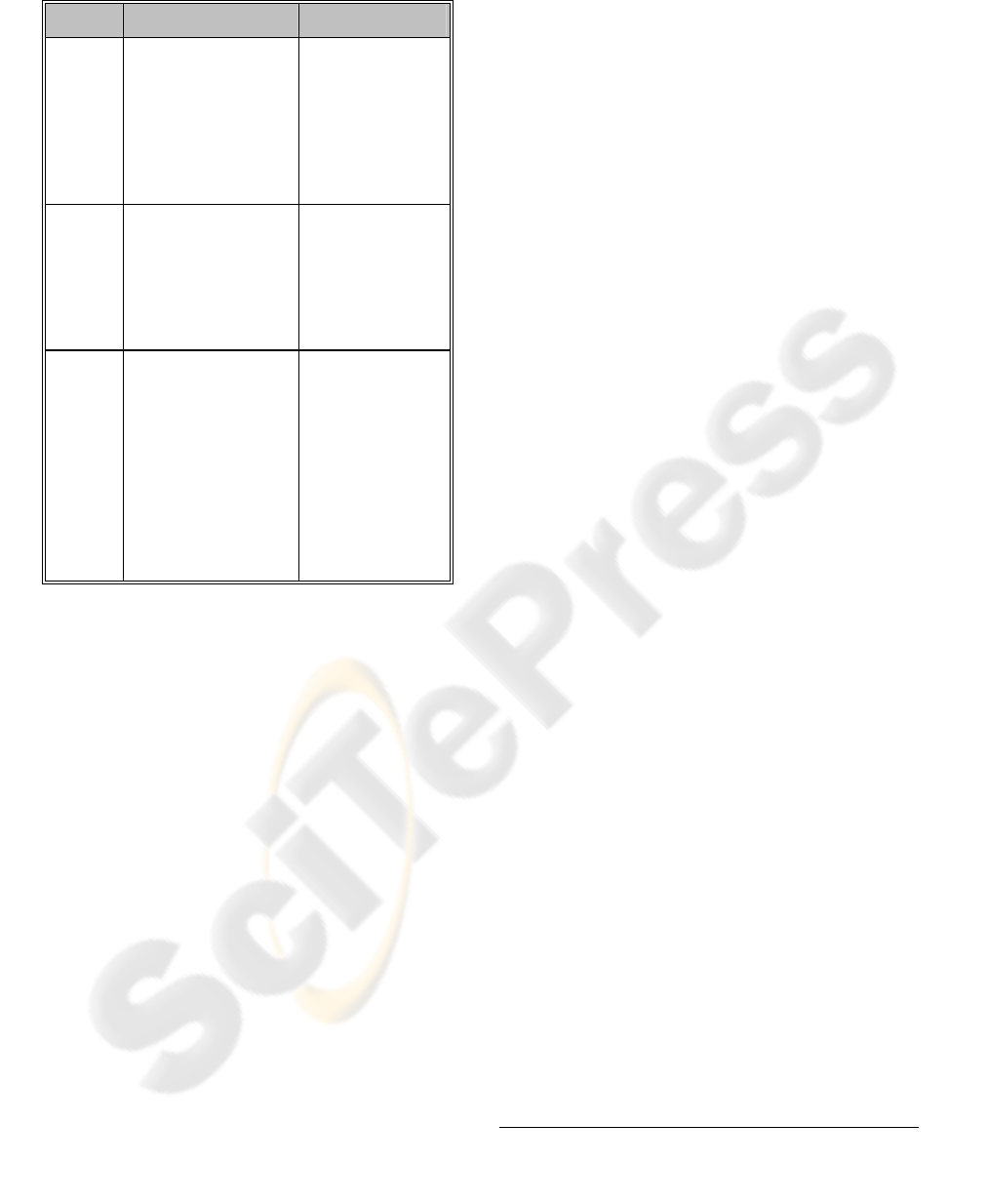
Table 1: Key interaction modes.
MODE DESCRIPTION EXAMPLE
Select selection is H/W
independent via the
traditional GUI (e.g.
mouse click, menu list)
or NFC touch.
Selected objects can be
interrogated or trigger
associated applications
user selects a
printer that he/she
visually discovers
in a room to check
its properties (e.g.
‘network access’,
‘is it a colour
printer?’).
Select-
and-
launch
select an object &
launch application.
Associate metadata to
physical objects by
various means (e.g. bar
codes, tags, service
description).
user touches the tag
on a movie DVD
and the browser is
launched with the
movie URL as an
input.
Select-
drag-and-
drop
select object A, drag it
to resource B, drop it
on B & resource B
launches associated
application. This event
pattern associates an
object with an
application that it is
not normally
associated with.
use a mobile phone
to transfer a file
from a laptop to a
local printer. The
phone-laptop touch
gesture represents
the file select-and-
drag. The phone-
printer touch
gesture represents
the drop.
5 PROOF-OF-CONCEPT
ARCHITECTURE
This paper introduces a method for enabling easy
service discovery in smart spaces by NFC-equipped
mobile devices. There are two critical players:
a) The smart space devices: these are NFC-
enabled devices, either physically accessible by the
user (e.g. a projector), or accessible through service
access points (e.g. touch here to send a fax). Their
service discovery parameters (also referred to as
service discovery record) are stored in an NFC tag
that a user device can read when it is within the
scanning range. A tag format is designed for this
service discovery record. The tag design is
compatible with the guidelines provided by the NFC
Forum. Additional backbone network devices such
as network access points (NAPs), configuration
servers (DNS, DHCP), AAA servers and so on may
provide other necessary functionality. The task of
setting up and configuring smart space environments
is out of the scope of this paper and it is addressed in
(Antoniou, Krishnamurthi & Reynolds, 2006).
b) The user devices: they are NFC-enabled
mobile devices with one or more wireless network
interfaces (e.g. WLAN, Bluetooth,
GPRS/WCDMA).
The rest of this section presents the architectural
design for the proof-of-concept prototype currently
under development (Antoniou & Varadan, 2006). Its
technical realization features the integration of NFC
technology with the UPnP framework. The security
aspects of this work are addressed separately in
Shakhshir & Kalofonos, 2006), (Antoniou &
Kalofonos, 2006).
5.1 The User Experience
Anna is at the departure’s lounge awaiting her flight.
She wants to print a copy of a report she has stored
on her mobile phone to read in the plane. She locates
a smart printer. She selects the report file (e.g. by
highlighting it) and touches her phone to the printer
hotspot (tag). Instantly, the printer is added to her
list of available services and a connection is
established between the two devices. By having
selected the report file first and then touching the
printer, the phone deduces the intention of the user,
which is to send the file to this printer. Without any
further action by the user, the printer control
application is launched on the mobile phone and the
report is printed. Through the printer control
application UI, Anna can check the printer
properties and the status of the printing job.
It should be noted that the proposed method can
potentially facilitate remote access to previously
discovered devices as well. Assume that Anna has
already discovered a fax service at the airport in the
same manner as she discovered the printer. She can
launch the fax service multiple times by clicking on
the fax icon that appears in her mobile phone UI.
5.2 The Tag Record
The NFC tag record design is a flexible and
extensible structure (Figure 1) that can be used to
store discovery parameters of smart network
devices, services and NAPs for a variety of use
cases
1
. The information exchanged is the Payload.
The Payload contains a Header and a record list with
1
NFC standardization is ongoing, hence naming
conventions and record formats are still evolving.
2
An industry consortium created by Microsoft.
WINSYS 2006 - INTERNATIONAL CONFERENCE ON WIRELESS INFORMATION NETWORKS AND SYSTEMS
254

one or more records. The Header contains the length
of the Payload and it is used to determine how much
data must be read from a tag. Each record is a
sequence of three elements, a triplet of (Type,
Content-Length, Content). The record Type
identifies the structure and semantics of the record
by providing the Type name. For the case of service
discovery, a suitable choice would be the discovery
protocol name and version number. The Content-
Length identifies the length of the record Content.
The record Content contains the actual data. The
example tag record of Figure 1 is further explained
in the rest of this section.
Header
Re c o r d
Typ e
Re c o r d
Length
Re c o r d
Content
Re c o r d
Length
Re c o r d
Typ e
Re c o r d
Content
SSI D
Public
Ke y
NTS
Cache
Control
USN Se r v e r NT Locat i o n
NAP access record UPnP device record
WLAN
SSDP / 1 . 0
Header
Re c o r d
Typ e
Re c o r d
Length
Re c o r d
Content
Re c o r d
Length
Re c o r d
Typ e
Re c o r d
Content
SSI D
Public
Ke y
SSI D
Public
Ke y
NTS
Cache
Control
USN Se r v e r NT Locat i o nNTS
Cache
Control
USN Se r v e r NT Locat i o n
NAP access record UPnP device record
WLAN
SSDP / 1 . 0
Figure 1: Tag record: UPnP service discovery via a
WLAN.
5.3 UPnP Overview
Universal Plug and Play (UPnP) is a set of protocols
including the Simple Service Discovery Protocol
(SSDP), the Simple Object Access Protocol (SOAP)
and the General Event Notification Architecture
(GENA) originally developed by Microsoft
Corporation and currently under development by the
Universal Plug and Play Forum
2
. UPnP standardizes
the protocols spoken between clients (called control
points) and services. It leverages existing standards
such as TCP/IP, HTTP and XML.
Devices, services and control points are the basic
abstractions of the UPnP device architecture. The
device model is hierarchical. In a compound device,
the root device and any embedded devices are
discoverable. Clients can address a root or an
embedded device independently. Soap servers in the
device act as entry points for interacting and
controlling it. Each service has a set of methods or
actions with a set of optional input/output
parameters and return values. The control point is
the client and the device is the server. Control points
can invoke actions on services. All UPnP devices
that conform to UPnP Forum specifications follow
the same basic pattern of operation: addressing,
description, discovery, control, eventing and
presentation. SSDP is used for the service discovery
process to (a) announce a device’s presence to
others and (b) search for devices and services. A
device sends a multicast message to either advertise
its presence to control points or to search for
services in a UPnP network. Devices that hear this
message respond with a unicast response message.
UPnP uses XML to describe device features and
capabilities. For instance, the aforementioned
advertisement message contains a URL that points
to an XML file in the network describing the UPnP
device’s capability. By retrieving this XML file,
other devices can learn about the advertised device’s
features, control it and interact with it.
5.4 SSDP Announcement for the
Smart Device
An example SSDP presence announcement for a
printer is shown in Table 2. A brief explanation of
the various fields is given next. For a detailed
description the reader is referred to (UPnP),
(Printer). The value of the NTS field identifies this
SSDP message as a presence announcement of a
new device or service. The Cache-Control field
specifies the duration that the presence
announcement is valid. The control point (user)
device caches the complete service discovery record
for the time frame defined by Cache-Control. The
USN field provides the device Universally Unique
ID (UUID). It may contain other information about
the device type (e.g. root device, device type,
service type). Server field provides information on
the operating system of the device, the product name
and version. The NT field has a potential search
target description, i.e. how the control point can
search for the discovered device or service. Finally,
the Location field contains the URL from which the
UPnP device description document can be retrieved.
This presence announcement is included in the
printer tag record as shown in Figure 1. The printer
record is of Type ‘SSDP/1.0’, i.e. the service
discovery protocol used. Its Content field consists of
the six sub-records, namely NTS, Cache-Control,
USN, Server, NT and Location URL.
A TOUCH IS WORTH A THOUSAND CLICKS
255
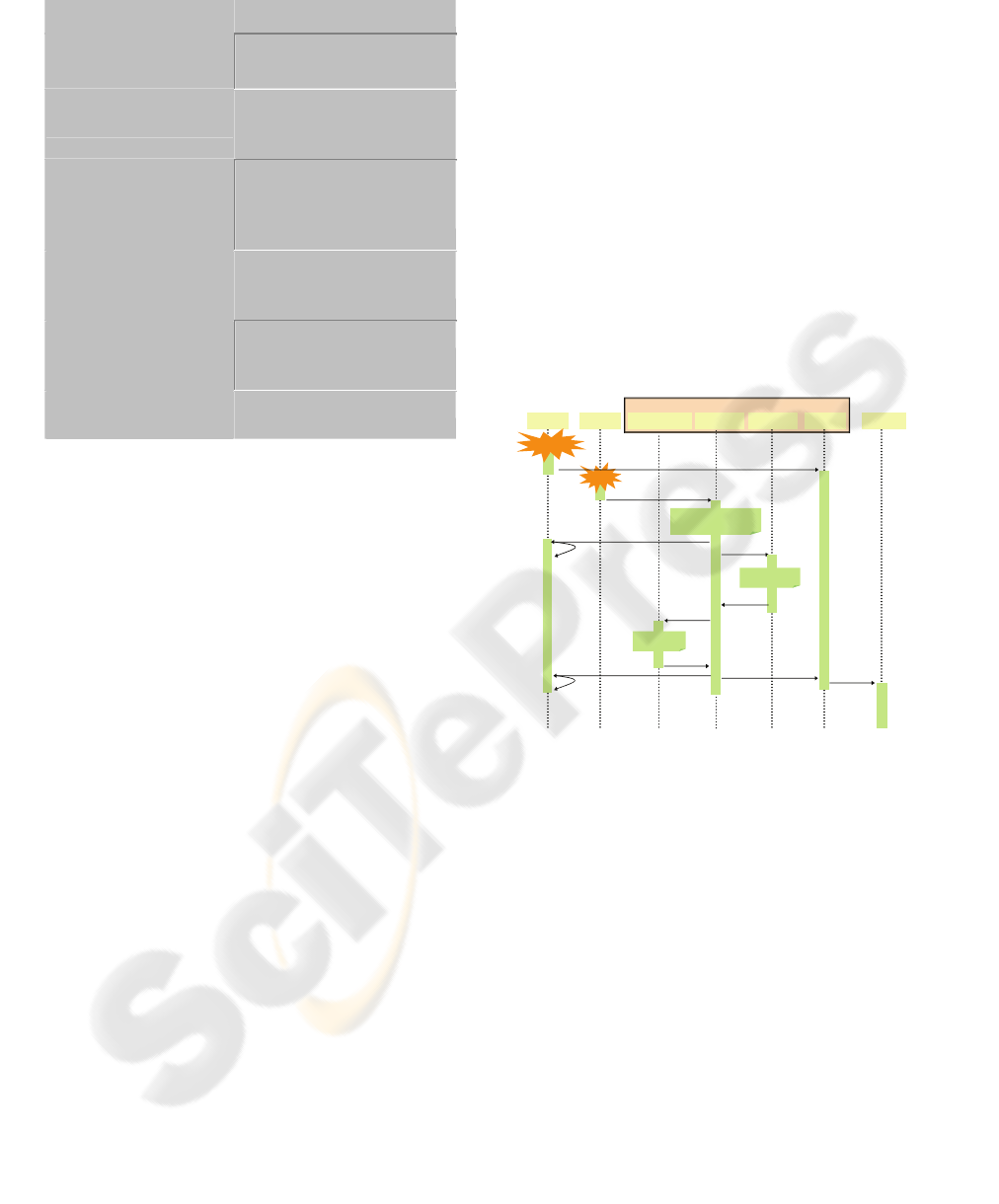
Table 2: SSDP presence announcement.
Field Example Data
NT: Specifies the search
target value
"urn:schemas-upnp-
org:device:Printer:1"
USN: Concatenation of
device ID and NT value
"uuid:0e2fc7b3-4c09-4665-
b4aef6f90448ba99::urn:schem
as-upnp-org:device:Printer:1"
Server: Concatenation of
OS name & version,
UPnP/1.0, product name
& version
Microsoft-Windows-NT/5.1
UPnP/1.0 UPnP-Device-
Host/1.0
Location: URL of root
device description
document
"http://192.168.64.11:53911/u
pnp/device/Printer.xml"
Cache-Control: Number
of seconds the
announcement is valid
1800 seconds
NTS: ‘alive’ or ‘bye-
bye’
ssdp:alive
5.5 SSDP Announcement for the
NAP
For this example implementation, it is assumed that
the printer device is connected to the network
through a WLAN NAP. In this case, the WLAN
record is of type ‘WLAN’ and its Content field
contains the SSID and (optionally) a Public Key. If
more than one NAP with the same SSID value are
available, the user device can connect to the access
point with the best signal strength. In cases where no
connectivity parameters are specified, it can be
assumed that the advertised device is accessible
through the public internet. The setup and
configuration process between the printer and the
NAP are addressed in more detail (Antoniou,
Krishnamurthi & Reynolds, 2006).
5.6 NFC-based UPnP Service
Discovery
Anna’s select-and-touch action triggers a series of
steps (Figure 2). Anna selects the report she wants to
print. This event selection is stored in the Activation
module. Next, she touches the printer tag with the
NFC interface on her mobile device. The printer tag
is read and passed to the Direct Access module in
the middleware layer. The tag is parsed and the two
records are extracted. These records are then
processed in sequence. First, the ‘WLAN’ NAP
record is passed to the Connectivity module to setup
the network connection. Secondly, the Service
Discovery SSDP/1.0’ record is passed to the Service
Discovery module which triggers the UPnP
discovery process. This process is equivalent to the
UPnP engine receiving a presence announcement
through a multicast message. When completed a
‘Discovery Complete’ message is sent to the
Activation module.
If the user device were in the default UI
application when the printer tag was touched, the
printer would be discovered and its icon would be
added to the available devices. In this case, a
selection event has taken place prior to touching the
printer tag. As a result, the Activation module
launches the printer control point application with
the selected object (report) as input for printing.
Mi d dl ew ar e
RFI D i n t e r f ac e
Se r v i c e Di sc o v e r y
module
Direct Access
module
Connectivity
module
UI
Act i vat io n
module
Application
Se l e c t i o n
Pr i nt er ’s RFID t ag d at a
Device discovery in progress
Connectivity
parameters
Discovery complete
Dev ice Ref ere nce
Touch
printer
Connection established
Service Discovery announcement
Discove ry co m pl et ed &
Device Reference
Sh o w s t a t us
m essag e
Decode pri nter’s tag data in to Connectivit y
record &
Service Discovery record
Establish short range
connection t o be used
susequent ly
Co m p l e t e Se r v i c e
Discov ery
Show status
message
Se l e c t
report
Launch printer application
with selected report
Printing application comes
to t he UI foreground
Figure 2: The service discovery process.
6 CONCLUSIONS
Technology miniaturization has made it feasible to
integrate NFC functionality into consumer mobile
device and has given birth to the Touch paradigm.
User input is received through straightforward
gestures such as touching or pointing and clicking as
part of everyday activities. An efficient UI design
can potentially replace sequences of multiple button
clicks and menu selections by a simple touch or
point-and-click action in order to complete a task.
By exploiting the benefits of this paradigm, it is
possible to enhance existing service discovery
protocols in order to create smart space
architectures.
WINSYS 2006 - INTERNATIONAL CONFERENCE ON WIRELESS INFORMATION NETWORKS AND SYSTEMS
256

This paper presents work-in-progress on how
service discovery and interaction can be simplified
through the use of NFC technology. An extensible
tag record is proposed with application in a variety
of service discovery scenarios and protocols. NFC-
enhanced middleware is designed to (a) retrieve tag
information over the NFC interface (b) perform
service discovery and connection establishment and
(c) launch associated applications for further
interaction with the discovered devices. The
proposed architecture integrates NFC technology
with the UPnP framework and does not require
detailed knowledge of network configuration or
service initiation processes.
Figure 3: Prototype HW Setup.
The proof-of-concept implementation is
currently in progress and will be presented in a
follow-up paper. It is developed for a Nokia 9500
Communicator handset in Symbian OS. The NFC
interface is provided through an internally
developed prototype, which is connected to the
phone through a USB cable (
Figure 3). The NFC
interface allows reading from and writing to Mifare
Ultralight (48 bytes) and Mifare Standard tags
(1Kbytes/ 4Kbytes). Future research directions will
explore other service discovery frameworks, as well
as, content sharing.
REFERENCES
Heidermann J, Govindan R. and Estrin D., 1998.
“Configuration Challenges for Smart Spaces”,
University of Southern California, USC Technical
Report.
Misra A, Das S. and MacAuley A., 2001.
“Autoconfiguration, Registration and Mobility
Management for Pervasive Computing”, IEEE
Personal Communications.
UPnP forum, www.upnp.org
NFC Forum, www.nfc-forum.org.
“Printer:1” Device Template Version 1.0, Approved
Standard, UPnP Version 1.0, 2002.
Bettstetter C. and Renner C. 2000. “A Comparison of
Service Discovery Protocols and Implementation of
the Service Location Protocol”, Proceedings Sixth
EUNICE Open European Summer School.
Antoniou Z, Krishnamurthi G. and Reynolds F., 2006.
Intuitive service discovery in RFID-enhanced
networks, Proc. of IEEE COMSWARE Conference,
India.
Riekki J., Salminen T. and Alakarppa I., 2006.
”Requesting Pervasive Services by Touching RFID
Tags”, Pervasive Computing Magazine.
Pering T., Ballagas R. and Want R., 2005. “Spontaneous
Marriages of Mobile Devices and Interactive Spaces”,
Communications of the ACM, Vol. 48, No. 9.
Raverdy P-G et. al. “The MSDA Multi-Protocol Approach
to Service Discovery and Access in Pervasive
Environments”, WSProceedings,
http://middleware05.objectweb.org/WSProceedings/de
mos/d10_Raverdy.pdf
Bajic E.. “Ambient Services Modeling Framework for
Intelligent Products”, Research Centre for Automatic
Control, University Henri Poincare, Nancy, Technical
Report, CRAN – CNRS UMR 7039,
Want R. et. al., 1999. “Bridging Physical and Virtual
Worlds with Electronic Tags”, Proceedings of CHI’99,
ACM Press.
Kerer C. at al. “Presence-Aware Infrastructure using Web
Service and RFID technologies”, Technical Paper,
Vienna University of Technology,
http://www.infosys.tuwien.ac.at/staff/sd/papers/Presen
ceAwareInfrastructure.pdf
Siegemund F. and. Florkemeier C., 2003. “Interaction in
Pervasive Computing Settings using Bluetooth-
enabled Active Tags and Passive RFID Technology
together with Mobile Phones”, Proc. of the First IEEE
International Conference on Pervasive Computing and
Communications (PerCom’03).
Romer K. at al, 2003. “Smart Identification Frameworks
for Ubiquitous Computing Applications”, Proceedings
of the First IEEE International Conference on
Pervasive Computing and Communications
(PerCom’03).
Antoniou Z. and Varadan S., 2006. iTouch: RFID
middleware for boosting connectivity and intuitive
user interaction in smart spaces, Nokia Research
Center Technical Report (NRC-TR-2006-002).
Shakhshir S. and Kalofonos D., 2006. IntuiSec: a
framework for intuitive user interaction with smart
home security, Nokia Research Center Technical
Report (NRC-TR-2006-003).
Antoniou Z. and Kalofonos D., 2006. “NFC-Based Moble
Middleware for Intuitive User Interaction with
Security in Smart Homes”, submitted for review.
A TOUCH IS WORTH A THOUSAND CLICKS
257
