
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
Gregor Langner
1 a
, Florian Skopik
1 b
, Steven Furnell
2 c
and Gerald Quirchmayr
3
1
Austrian Institute of Technology, Austria
2
School of Computer Science, University of Nottingham, U.K.
3
Faculty of Computer Science, Research Group Multimedia Information Systems, University of Vienna, Austria
Keywords:
Computer Science Education, Cyber Security, Cyber Security Education, Cyber Range, Teaching Model.
Abstract:
The threats posed by the digital space are a challenge for businesses, organisations and people that can no
longer be met with pure knowledge. For this reason, all individuals have to demonstrate not only knowledge
but also skills and competences in the field of cyber security. However, this presents an enormous challenge
to higher education institutions (HEI) in terms of how to teach these competencies and skills to their students.
In this paper, we present a new teaching method for cyber security (CS). It is based on the requirements and
needs of educators and learners and integrates existing methodological approaches. This teaching method is
complemented by the use of a cyber range as a central teaching tool to make the education more realistic. The
method is not only applicable to technical programmes, it is applicable to all programmes and the focus is on
cross-disciplinary training. This ensures that the teaching not only meets today’s requirements but also those
of the future in the field of education.
1 INTRODUCTION
Industry and society are facing major challenges in
the context of digitalisation. Cyber threats are be-
coming more target-oriented and sophisticated, re-
sulting in them being identified at a late stage. (On-
wubiko, 2017) This is reinforced by the fact that many
businesses require qualified IT employees who are
equipped with the necessary skills and competencies.
Furthermore, there are not enough graduates with this
kind of profile in higher education.
Cybersecurity is no longer only a problem of the
IT-department, it affects the whole enterprise. This re-
sults in drastic consequences: for example, the identi-
fication and response to ransom demands and similar
software can take an average delay from 90 minutes
to 6 days (ENISA, 2019). This period increases by
a multiple in the case of Advanced Persistent Threat
(APTs), because of their specific nature and the meth-
ods used; it takes an average of 90 to 180 days for
them to be recognised (ENISA, 2019). This situa-
tion is made significantly worse by the near absence
of digital investigation knowledge. With regard to CS
training, in particular problem-based teaching, there
a
https://orcid.org/0000-0002-3271-5073
b
https://orcid.org/0000-0002-1922-7892
c
https://orcid.org/0000-0003-0984-7542
is currently inadequate capacity in most HEI, as well
in private CS training programmes. (Crumpler, 2019)
Existing training programmes also do not suffi-
ciently address the problems and needs of businesses.
More specifically, the existing programmes are de-
signed in a way that the education is primarily theory-
based, with limited or no practical elements. Also,
the number of specialised graduates is too small to
meet the growing demand for CS in terms of aware-
ness, threat prevention and response. In practice, this
leads to a further aggravation of the shortage of spe-
cialists and a lack of expertise in CS. For this reason,
future training programmes must be designed in an in-
terdisciplinary way with a Cyber Range (Leitner and
Frank, 2020) to prepare non-technical students, and
the higher education sector must offer content and ex-
ercises that address current and future problems, as
well as needs. In order to achieve this, education must
change fundamentally, away from a lecture-oriented
approach to a more experience-oriented and collabo-
rative environment.
The majority of knowledge transfer in adult edu-
cation at HEI, educational establishments and insti-
tutions either use traditional or purely digital teach-
ing methods. For both methods typically teaching
lectures, case and literature analyses are used. The
advantage for the lecturers is that they only create
Langner, G., Skopik, F., Furnell, S. and Quirchmayr, G.
A Tailored Model for Cyber Security Education Utilizing a Cyber Range.
DOI: 10.5220/0010834000003120
In Proceedings of the 8th International Conference on Information Systems Security and Privacy (ICISSP 2022), pages 365-377
ISBN: 978-989-758-553-1; ISSN: 2184-4356
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
365
course materials once and the preparation time can
be reduced to a necessary minimum. Subsequently,
the materials created in this way are mostly used over
a relatively long period of time without or with only
minor adjustments. (Kebritchi, 2017)
However, there are a series of shortcomings with
these teaching approaches in the context of conveying
CS competencies to a wider audience: The knowl-
edge imparted does not correspond to the current sit-
uation in practice, leaving a gap in terms of future-
proof competences and qualifications that can achieve
immediate practical impact in the industry. (Millis,
1997) The method of education is centred on the lec-
turer, and thus the needs and abilities of the learners
cannot be considered in the lessons to the necessary
degree. Practical exercises or realistic exercises are
only rarely integrated into the training and if they are,
only a relatively small part of the content is covered.
The acquired knowledge is based on theory with min-
imal or no relation to actual conditions. Digital meth-
ods are mostly used as teaching support. They range
from the distribution to permanent storage of mate-
rials or as an easy way to submit assignments in a
centralised way. Collaborative problem solutions are
only partially possible. (Yijun, 2011)
It requires a high level of self-organisation and
know-how from the learners, since tools that would
make it possible are in most cases not offered. Hy-
brid approaches would be a solution for teaching in
response to current and future needs. This requires
not only the adaptation of lessons and materials, but
also the adjustment of didactic methods regarding
new conditions and the provision of necessary infras-
tructure. Digital and traditional teaching methods can
then be used in a complementary way, provided that
teachers and learners are coached according to their
needs. Educational concepts, must be structurally re-
designed to integrate both target groups and to achieve
a more holistic approach. (Vasiliev, 1996)
The work presented in this paper aims to over-
come the gaps between theory and practice in CS ed-
ucation in higher education. For this purpose, a teach-
ing concept for CS with a cyber range as a central edu-
cational element is introduced. The different require-
ments and needs from educators and learners were in-
corporated and embedded into the design. In this way,
it is ensured that a holistic picture of CS can be con-
veyed. To reduce the complexity and narrow the fo-
cus on the concept and its application, the other actors
involved in education, such as HEI or national regu-
lators, but also international regulators, were not in-
cluded in the assessment. The concept proposed here
is primarily intended to be used in higher education,
but with adaptations it can also be used in adult, edu-
cation and training.
The paper is structured as follows: In section 2 we
present the general requirements for a teaching con-
cept in the field of CS. Based on the results and the
surveys, the developed teaching model is presented
in the chapter 3. We show the characteristics of the
model and the advantages which can be achieved with
the model. The performance and evaluation of the
model can be found in section 4. In section 5 the dis-
cussion of the results is presented and section 6 pro-
vides a summary of the proposed concept and an out-
look on future work.
2 TEACHING CONCEPT
REQUIREMENTS & RELATED
WORK
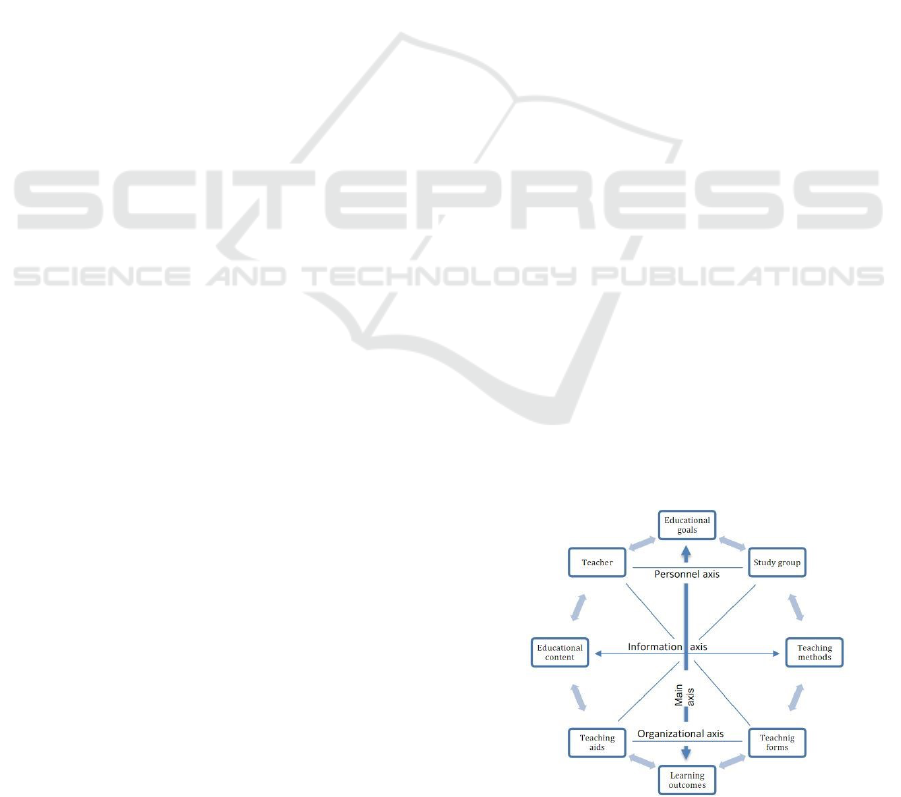
An educational concept must be able to react dynami-
cally to different input parameters in order to identify
all the needs of learners and teachers and be able to
meet these needs later more effectively. For this pur-
pose, the authors in (Flechsig, 1996; Meyer, 2005)
show the three dimensions (personal, informational,
organisational) that hold a central role in education
and learning. These are connected with a central Axis,
which ends with the learning objectives and the learn-
ing success (Figure 1).
The following requirements for a teaching concept
in CS are aligned with the challenges of CS. For ex-
ample, learners and teachers must be able to develop
skills and competences on the social, technical, and
multidisciplinary levels and to build up and maintain
a holistic understanding of CS. These three areas are
linked to the dimensions of the didactic octagon in
order to include the external and internal influencing
factors.
Social Requirements: Social learning is a pro-
cess that requires interpersonal skills such as commu-
Figure 1: Didactic octagon (Andres, 2020).
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
366

nication and people-to-people interaction. Therefore,
it is necessary to foster an environment, which stim-
ulates individuals to interact. The teaching concept
must allow learners to exchange and work collabo-
ratively on problems on a formal and informal basis,
whereas the teaching concept has to provide a men-
tal model to achieve this. It is important that learn-
ers are never given the impression of having to deal
with a problem on their own. Teachers need resources
they can use to ensure an adequate learner-teacher re-
lationship. Education is not only about transferring
knowledge, but also about fostering soft skills and
competences.(Motschnig-Pitrik, 2002) These are rep-
resented by two dimensions (personal, information)
of the didactic octagon.
Technical Requirements: All learners across all
disciplines have to be empowered with a range of
technical capabilities and competences. They also
need guidance to gain these competences and capabil-
ities. The educational approach must allow learners
to explore new solutions in a cyber range and allow
them to learn from mistakes. The technical resources
should support learning off and online to meet the var-
ious types of learners. Learners are from all social and
cultural backgrounds, therefore it is important to en-
able all to have equal access to the same technical re-
sources and to have equal chances to learn in general.
Educators not only have to provide exercises on the
technical aspect, they have to provide technical sup-
port when necessary and should maximise the oppor-
tunities offered by the digital space. They also have
requirements on the teaching concept on the technical
side, as the equipment needs to support the lessons
and carry out trivial tasks given by them.
Multidisciplinary Requirements: Addressing
the full scope of CS requires the education to pro-
vide learners with technical and non-technical con-
tent across all levels and empowering them to apply
those. (Sobiesk, 2015) For this reason learners need
to be taught the basics through disciplinary and in-
terdisciplinary courses. As a minimum, learners has
to develop knowledge and competences in the areas
of policy, finance, computer science, and law. Ed-
ucators are required to provide and deliver abstrac-
tions tailored to the target group. Learners must be
offered the opportunity to specialise in individual do-
mains through electives, but these programmes may
not be pursued as a sub-subject and must be care-
fully considered during curriculum design. As uni-
versity educators are in most cases only able to cover
their own discipline, cooperation between institutes is
necessary. Educators must work together and be able
to exchange current and future educational resources.
(Sobiesk, 2015) This is represented in the didactic oc-
tagon in the information dimension and, as outlined
above, there is a link to the social dimension.
3 TEACHING CONCEPT
Teaching in the field of CS includes a wide range of
topics across different disciplines. In order to be able
to establish a complete teaching concept, different re-
quirements and factors from educators and learners
have to be kept in mind together with the individual
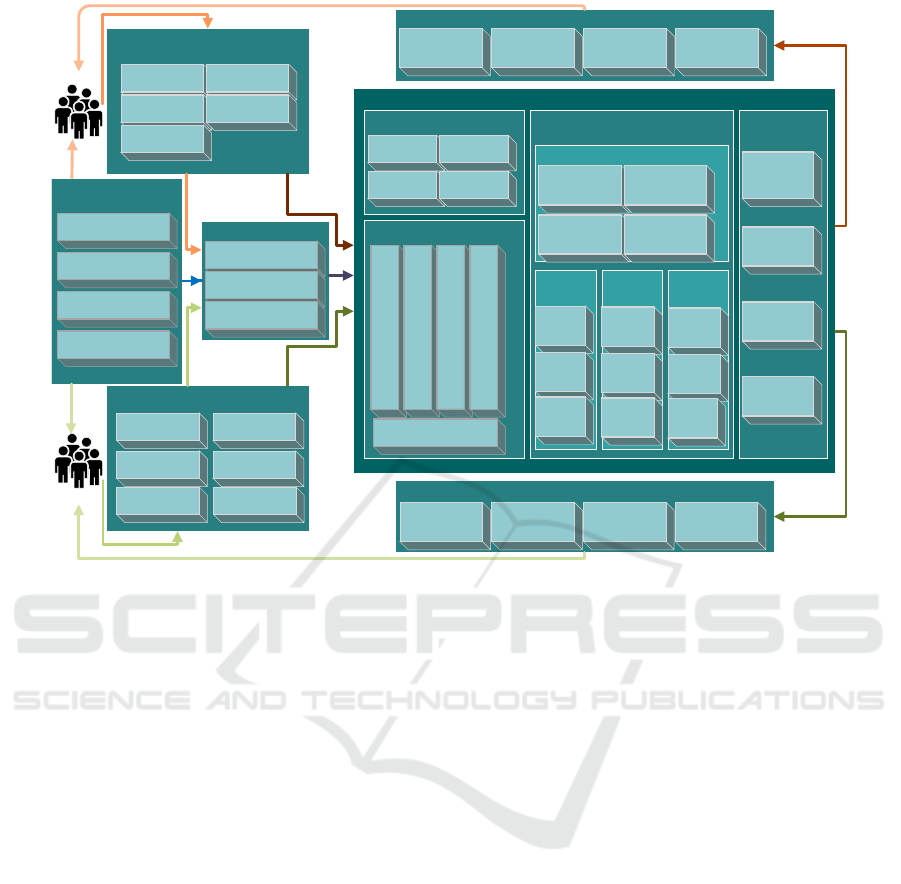
subjects and disciplines reference. Figure 2 illustrates
the complete teaching concept developed and the var-
ious input factors and parameters as well as the differ-
ent outcomes that will be achieved.
The objective is to enable learners to unleash their
full potential and to provide a practical and integrated
theoretical education through a variety of methods to
meet the challenges of CS. Educators will be able
to use proven approaches and enlarge its own edu-
cational conception as also acquire skills and compe-
tences that are not possible with current methods.
Furthermore, the use of this method offers edu-
cators the advantage that the teaching resources and
materials can be simply adapted and new assignments
generated for each semester. For adaptation, the out-
comes will be used, only on the organisational level,
as the student groups will never be the same due to
external factors.
3.1 Environmental Conditions
External factors or environmental conditions refer to
all parameters that influence education beyond the
scope of a educational approach and are highly sensi-
tive to the educators and learners. In this model, four
areas have been identified. Three are considered in-
dependent and one is formed by the others. These can
be found in the first section of the model and are ex-
plained in more detail below. For the sake of brevity,
only the essential ones are included in this example
but there are many factors that need to be taken into
account or that have an impact on teaching in general.
3.1.1 External Drivers
External drivers are the factors that do not come from
the educators and learners but may influence them in
their decisions and activities. They are generally es-
tablished or enacted by external stakeholders such as
HEI, legislators, employers and society and have a
strong influence on education or on the target groups.
The following points have been elaborated as external
drivers:
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
367
Educators outcome
Cyber security teaching model
Students
Lecturer
Teaching session
Collaborave exercise
Applicaon scenario
Learning
Env
Key factors affecng the success of
training
Cognive skills
Social skills &
compromise skills
Movaon &
Expectaon
Skills & non-
cognive skills
Learning strategies
Teaching concepts
Problem-oriented
lesson
Origins-oriented
lessons
Time-oriented
lessons
Communicaon-
oriented lessons
Mul-perspecve
lessons
Theorecal exercises
Collaborave hands-on examples
Interacve learning of the content
Summarising the key points
Teaching environment
factors
Locaon/ Experience/
Resources
Content/Group
External drivers
Lecture with the
fundamentals
Managme
nt Env
Technical
Env
Learner outcome
Addional
teaching materials
Experience, skills,
capabilies and
competences
Legal requirements
Teaching delivery Approach
Evaluaon and
Feedback
Scenario-based
lessons
Flipped
classroom
Work based
learning
Blended
learning
Student-led
learning
New trends in technology
Changed demands within
the labour market
Finances/Economics
Technical
cybersecuity
scenario
Non-technical
cybersecurity
scenario
Interdisciplinary
cybersecurity
scenario
Skills, capabilies
and competences
Awareness raising
for CyberSecurity
topics
Interdisciplinary
cooperaon
Integrated training
of young
educators
Interdisciplinary
knowledge and
perspecves
Pracce-oriented
training
Teaching objecve/
Outcomes
Qualitave
feedback from
educators and
learners
Intermediate
evaluaons
Performences
and soluon
approach
Lessions
learned
Strategic
decisions
Resource
planning
Leadership
Self-Guided
learning
Experimental
approaches
to problem
solving
(Meta)
Cognive
Equipment
Cyber Range
(Virtual
Cooperave
Learning
Environments)
Collaborave
learning
spaces
Online
classrooms
….
Figure 2: Overview of the teaching model.
Legal Requirements: These are defined by the
legislator (European and national acts) and have dif-
ferent effects on the education. They have a direct
impact on the teaching content through their require-
ments; the knowledge must be acquired by learners to
be able to assess the full implications of actions and
measures and to ensure compliance with the law. On
the other hand, they can trigger training and further
education to prepare learners who are already embed-
ded in the world of work for the new conditions.
New Trends and Technologies: CS exists in a
changing environment and is strongly influenced by
new technologies and trends. This also has a strong
impact on the target groups and the teaching environ-
ment. Learners are expected to be able to learn and
apply the basics, including new technologies. For this
reason, they also expect education to provide them
with the knowledge they need. For the educators, it
means that they have to continuously educate them-
selves to enable them to apply the new technologies
to their students. An integration of these new trends
has to be done continuously as the labour market ex-
pects it.
Labour Market Requirements: The labour mar-
ket is always shifting and evolving in the context of
technology. As a result, employers require new em-
ployees to have a set of skills, competences and capa-
bilities and expect HEI to provide these to the learner.
Employers want to keep education and training costs
as low as possible for economic reasons. Learners
are under strong external pressure as they fear that if
they do not meet these requirements, their opportuni-
ties will be harmed. The educators and HEIs, on the
other hand are divided. On the one hand, they have
to provide learners a general education with the ba-
sics so the more advanced topics can be addressed,
and on the other hand, not providing this education
and training may lead to a reduction in the number of
students enrolled and therefore a lack of financial re-
sources for adaptation. The teaching method must be
able to accommodate the changing requirements and
provide them in full.
Finance/Economics: Here the different circum-
stances of the two target groups are addressed, but
also the higher education institution as a whole, which
has a direct influence on the teaching method. For
learners, this factor decides whether they study full-
time and focus on their degree or have to work to sup-
port themselves. In principle, there is nothing rep-
rehensible about working alongside a degree if the
learner is also active in the same field. In this way
they can generate additional output that supports them
in their degree programme. Another aspect is that
learners need to purchase additional materials or tech-
nology to fully comprehend and complete the course
content. This is a limiting factor for educators, as they
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
368

have to manage teaching on a technological and hu-
man level with the resources available to them. The
teaching method can only integrate new technologies
or materials if the resources are available. Conse-
quently, the teaching environment has to take this into
account.
3.1.2 Key Factors of Training
The learning process depends on factors that can be
directly or indirectly influenced by the educators and
the learners themselves. These learning factors also
influence the teaching methods applied during the
learning process as well as during the preparation
phase. For this work, the following key factors for
successful learning were identified:
Cognitive Skills: This refers to skills that al-
low the acquisition of knowledge and information
processing as well as being responsible for logical
thinking. (Anderson, 2013) These are essential skills
which not only steer learning but are also crucial
in solving problems. Consequently, these skills are
responsible for perception, memorisation, learning,
decision-making and attentiveness. These skills are
fundamental to the concept of teaching and to CS.
They enable different aspects of the disciplines to be
absorbed and incorporated into the assessment. This
skill is important not only for CS but also for all areas
of learning.
Skills & Non Cognitive Skills: These are the soft
skills related to communication and cooperation but
also responsible for commitment, self-efficacy and
conscientiousness. (Coneus, 2009) They are often as-
sociated with the other soft skills and social skills; al-
though for some areas this is accurate, for others they
are distinct. Developing these skills will enable fu-
ture leaders, but also others, to deal with situations of
great stress. The teaching method itself is to foster
and stimulate the development of these skills.
Social Skills & Compromise Skills: Describes
the learners’ ability to interact and compromise on a
social level. It includes social intelligence, interper-
sonal characteristics, verbal and nonverbal elements
and social self-regulation. (Kelly, 1982) Learning
these skills is essential for achieving objectives in
understanding complex topics and finding solutions.
The acquisition of these skills is a major challenge in
education. To enable this and to further develop ex-
isting skills, the teaching method provides the collab-
orative area which can be adapted to suit at any time.
Learning Strategies: These are action patterns to
regulate the learner’s own learning. These are either
conscious or unconscious and vary according to the
requirements and the situation. (O’Neil, 2014) The
learning strategies used by learners can be classified
as follows, according to (Shi, 2017):
• Cognitive strategies: The development, structuring and
use of knowledge.
• Repetitive learning strategy: A strategy of reviewing in-
formation and knowledge in order to transfer it into the
long-term memories of the learners.
• Development strategies: Combining existing knowl-
edge with prior knowledge to abstract complex prob-
lems to familiar problems.
• Organsational strategies: Establish a relationship be-
tween acquired knowledge in order to develop a con-
sistent picture.
The teaching method allows each learner to apply
their own strategy to achieve an optimal learning goal.
The intention is also to enable learners to expand their
horizons and apply new strategies in order to achieve
the objective more effectively.
Motivation & Expectation: Learners have dif-
ferent motivations and expectations in a subject area.
Learners may be highly interested in a subject area,
and the wrong methods can reduce their motivation.
Learner expectations can be difficult to meet in most
cases. For this reason, it is important that courses
are described explicitly so as not to disappoint mo-
tivated learners. Motivated learners are supported by
the teaching method through self-directed methods of
the learner and other learners can develop their own
interest through the method.
3.1.3 Selection of the Teaching Concept
The following teaching methods have been selected
to ensure a deep understanding of CS. This is based
on the problem-based approach, which allows teach-
ers to create exercises that enable learners to develop
solutions and work collaboratively. The purpose, ac-
cording to (Hu et al., 2018) and (Lehmann, 2008), of
problem-based learning is achieved when the follow-
ing points are met:
• In the first phase (identification), learners need to un-
derstand the problem in all details. They need to ob-
serve the problem from all perspectives and compre-
hend the nature of the problem before moving on to the
next phase.
• The second phase (analysis and collaboration) requires
the learner to analyse the problem in order to solve it.
They have to examine the problem in comparison with
the current situation and the initial situation and com-
pare them with similar problems. They can receive as-
sistance from the teacher in order to design a solution
through cooperation with other learners.
• In the penultimate phase (evaluation and reflection),
learners have to review and evaluate the knowledge ac-
quired in the context of the problem once it has been
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
369

solved. To do this, they reflect and expand the problem-
solving process to other domains with equivalent chal-
lenges.
• The last phase (knowledge enhancement) consists of
developing new possibilities for solving complex prob-
lems based on achieved results and considering the ad-
vantages and disadvantages of the identified solution in-
cluding alternative methods.
This central approach is extended with the approaches
listed in Table 1
Table 1: Teaching Approaches.
Communication
oriented
Through this, the fundamentals will be communicated along
with the theory. It also avoids misunderstandings in under-
standing the content and the task. Learners must further be
able to state the problem at any time through communication.
Origin-oriented
approach
Are integrated in order to be able to meet the requirements
of all learners. This requires that the educators analyse and
incorporate these requirements in a short time frame. Both
have to react to the situation, however all needs cannot be
met in this way.
Experiential and
fact/ knowledge-
based approach
Applied to facilitate and optimise the transfer of knowledge.
This enables the learner to associate the individual parts to-
gether. To achieve this, a strong interaction between learner
and educator, but also between learners, must be established.
This is supported by collaborative exercises in the teaching
method.
Multi perspective
approach
The method ensures flexibility while supporting a variety of
topics. It allows learners to explore solutions to problems
from different perspectives of different disciplines.
Time-based
approach
Exercises and theoretical teaching sessions are conducted in
close time to each other in order to increase the learning out-
put and therefore anchor the knowledge more deeply. The
exercises are designed in a way that they can be finished dur-
ing a short period of time. The short intervals between in-
dividual exercises make it possible to reduce the complexity
and define the intermediate objectives in order to be able to
carry out an evaluation at all levels.
Scenario-based
approach
Specific content (theoretical and practical) is designed to tell
a continuous narrative. This allows learners to relate complex
content to each other, but also to link it to other disciplines.
3.1.4 Teaching Environment Factors
The last external factor that affects the teaching con-
cept is influenced by the other three factors and cor-
relates between the three domains. It addresses all
edges of the didactic octagon and allows the teaching
method to react to all impacts and factors. For this
purpose it is necessary to consider the individual ar-
eas and axes that are related to the teaching unit as
described in the chapter Requirements. The personal
Axis is represented by the educators and the learners
and both groups incorporate their requirements and
factors into the teaching method. The Information
Axis links the educational approaches that are pre-
sented with the content of the unit. The content is only
partially filled by the external factors, while the other
part is fulfilled by the teaching method which has to
be coordinated in order to ensure harmonisation. The
Organisational Axis is influenced by the available ex-
ternal resources, but the majority is affected by the
teaching method. In order to connect these individual
axes, the main Axis becomes operational. Here the
objectives and the outcome are linked. Objectives are
in part determined by external factors and in part by
the teaching method. The Outcome is influenced in
the same way, but can be influenced by the educator.
All the inputs are weighted equally in the teaching
methodology and are handled in the same way. Ne-
glecting or unequally weighting them leads to a dis-
balance and consequently to a less than optimal out-
come. This is why a feedback loop was integrated into
the teaching method, which allows an additional eval-
uation and adjustments after a run with the outcome.
This is a possibility for the educators and learners, but
also for the institutions, to quickly and efficiently ad-
dress any shortcomings.
3.2 Cybersecurity Teaching Model
The teaching model for CS covers the theory lessons
as well as the exercises. The model also includes the
performance evaluation of both parts and the eval-
uation process regarding the skills, capabilities and
competences used and built by the learners. For that
reason, the model is divided into three parts, which
are defined as follows:
1) Didactic Principles: These are represented by the teach-
ing approach to teaching and the teaching session.
2) Exercise Principles: In the method, exercises are ba-
sically designed as collaborative activities, which is
why this approach represents the meta-level. Within
this meta-level are the application scenarios and the
management, learning and technical environment con-
ditions.
3) Evaluation Principles: They are presented in the teach-
ing model with the coresponding area of evaluation and
feedback in order to lead to an optimal outcome.
3.2.1 Didactic Principles
The didactic principles made available to educators
by the teaching model are derived from the gen-
eral principles of comprehensiveness, clarity, target-
orientation, self-activity and topicality. (Marius-
Costel, 2010) And are included in the two areas. The
first area contains the methodology and approaches of
how the teaching content is delivered to the learner,
see Table 2. The teaching delivery approaches for the
model are defined as follows:
The second section describes the various options
for designing a session. The basis is a lecture with the
fundamental knowledge necessary for the learners.
The foundations of the teaching sessions can be
extended with the following approaches to increase
the efficiency of learning, see Table 3
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
370
Table 2: Methodology and Approaches.
Flipped Class-
room
Lessons are designed to improve the quality of teaching
through a learner-centred approach. It requires learners to
independently prepare for the lesson and work on a problem
within the sessions. (Ozdamli and Asiksoy, 2016)
Blended Learn-
ing
A combination of offline and online resources are used. It al-
lows learners to control the time, place and pace of learning.
This also requires that educators and learners are in physical
contact with each other however face-to-face practices are
enhanced by digital based activities in terms of content and
delivery. (Graham, 2006)
Work based
learning
Is a strategy that allows learners to have real-life experiences.
It is a combination of theoretical and technical skills and is
usually linked to business practices. (Boud and Solomon,
2001) It is not possible at the higher education level - here the
cyber-range environment is applied. This provides learners
the opportunity to work on real systems and to develop topics
that are otherwise only available in business.
Student-led
learning
The responsibility for the teaching experience rests with the
learner. Knowledge acquisition is facilitated as learners in-
teract with a peer-to-peer process. (Marvell, 2013) In the
model, this approach is fundamentally used in exercises to
provide learners with all the opportunities and in order to
strengthen skills.
Table 3: Type of Sessions.
Theoretical exer-
cise
During the lessons, exercises can be performed where theo-
retical topics are elaborated. This means that learners have
to deal with the content of the lessons. This is similar to the
lessons that children receive to learn mathematics.
Collaborative
hands-on exam-
ples
Learners have to work together on abstract and real exam-
ples in the sessions. This allows for immediate assistance in
case of problems and enables timely preparation of results
for all learners. The complexity of the exercises is variable
and always depends on the level of knowledge and skills of
the learners.
Interactive learn-
ing of the content
Use of specific tasks and questions to encourage learners to
participate in the lesson without communicating directly with
the lecturer. This should reduce the barriers and lead to a new
teaching experience.
3.2.2 Exercise Principles
The exercises represent an extension of the theoretical
lessons and should serve to consolidate the content.
The exercises are therefore important as they are not
isolated and follow the same narrative. Therefore, the
principles of the exercise follow the didactical guide-
lines. During the exercises, the learners work collab-
oratively together, so it is on the meta level.
An application scenario represents the first part
of the exercise that needs to be prepared. The exer-
cise topic and the individual focus points will be de-
termined and different storylines will be generated.
A storyline deals with a specific CS challenge, e.g.
ransomware, APT, etc., or a storyline pushes the sce-
nario ahead to guide the learner to the desired objec-
tive. Storylines can also be incorporated to increase
the difficulty of the scenario and produce background
noise in order to disguise the attacker’s actions. For
this reason, the Table 4 contains scenarios that sup-
port this model and can be built upon. There are three
dimensions in the concept to adapt the exercise to the
different conditions of the environment, enabling all
teaching concepts to be addressed. To do this, edu-
cators have to address the three dimensions of man-
agement, learning and technology. The first dimen-
Table 4: Application scenarios.
Technical cyber-
security scenario
This kind of exercise involves a strong technological com-
ponent. In order to design this type of exercise, an infras-
tructure (Cyber Range) has to be integrated into the training
where learners will be able to work with the scenario and
repeat the scenario if necessary in case the chosen solution
does not lead to the desired result.
Non-technical
cybersecurity
scenario
Represents the logical opposite of the technical scenarios. In
this type of scenario, technology can and will be used, but
the aim is not that learners develop a solution that focuses
on the technical level. The aim here is rather to focus on the
non-technical areas such as risk management etc. that can
be developed without the use of technical resources. Purely
non-technical exercises are the preliminary stage of the in-
terdisciplinary exercises and are designed to evaluate learner
procedures and processes.
Interdisciplinary
cybersecurity
scenario
The storyline approach can be a combination of technical and
non-technical exercises with the integration of different dis-
ciplines or a pure exercise where learners from different dis-
ciplines work on the same challenge. Storylines must there-
fore be planned in a way that all learners can contribute their
strengths and pass on their knowledge to other learners by
working together.
Other scenario This teaching method also allows other types of scenarios for
integration. The educators have to make sure that all parame-
ters can be implemented and that the learning objectives and
the expected outcome are properly defined.
Table 5: First dimension.
Strategic deci-
sions
Learners have to make decisions in order to succeed in the ex-
ercise and therefore in the scenario. The decisions will change
as the information content evolves. It is very important that the
decisions are documented and on which basis they were taken.
It prepares learners for future leadership roles.
Resource plan-
ning
Learners need to consider resources that are supposed to be
lacking in the exercise, like money, human resources etc. It
prepares learners for future leadership roles.
Leadership It is essential for future decision-makers to build up compe-
tences and skills in this sector. This is often neglected in edu-
cation and training programmes or reduced to the transmission
of soft skills.
Other Additional management duties can be added to the exercise,
depending on the scenario.
sion is the management environment, while the role
assignment belongs to the learners. The characteris-
tics of the dimension are shown in the Table 5.
The second integrated environment that is sup-
ported and embedded by the model deals with the
topic area of Learning with Application. In this field,
competences and skills are addressed that are used
and acquired. The following strategies of this dimen-
sion are listed in the Table 6.
Table 6: Second dimension.
Self-Guided
learning
Combines learning organisation, learning goal identification,
learning control and learning outcome monitoring. Learners
are stimulated to learn by their own and educators provide the
environment. (Kraft, 1999)
Experimental ap-
proaches to prob-
lem solving
Enables learners to independently develop solutions based on
experience and acquired knowledge. In the exercise, these so-
lutions are evaluated and in case of a failure, the learners are
forced to reconsider the solution and develop a new approach
to the problem.
(Meta) Cognitive
Equipment
Firmly anchored in the teaching method in order to guarantee
the processing of information on the different dimensions and
to enable learners to acquire new knowledge and is linked to
the logical thinking.
The last environmental dimension which is inte-
grated into the teaching concept as a fixed element is
the technical dimension, see Table 7. The exercise
methodology is provided and carried out with tech-
nical resources. The different exercises in the sub-
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
371
Table 7: Third dimension.
Cyber Range Is a virtual infrastructure that can be adapted according to the
requirements of the challenge. Physical components such as
operational technologies (OT) and Internet of Things (IoT)
can be integrated, to bring the experience more into the real
world.
Collaborative
learning spaces
Software module that allows learners to collect information
and share it in a centralized way and refer to it as a ticket
system when new information is available. In the European
project ROUTE-TO-PA (Palmieri, 2021) an open source and
publicly available tool was developed that fulfills these re-
quirements.
ject areas also require a variation of technical exercise
techniques and methods.
3.2.3 Evaluation Principles
The evaluation of the theoretical and practical part
of the training is important for the assessment, but
also for the development of skills. The assessments,
however, also support the trainers on the organisa-
tional level. They receive feedback and can adapt ex-
ercises and teaching to improve quality or to better
meet learners’ needs. Learners can be motivated by
high-quality feedback at every stage and work more
intensively on the content. For this reason, differ-
ent approaches have been integrated into the teaching
method to support teachers, and they follow the fol-
lowing principles in Table 8.
Table 8: Integrated methods of evaluation.
Quantitative
feedback from
educators and
learners
In this variant, it is possible for learners to receive feedback
from educators, learners but also experts. This allows learn-
ers to understand which errors they have made during the ses-
sion and which competences and skills they need to further
improve. In this way it is also possible to ensure assessment
with points.
Intermediate
evaluations
Exercises take place in a constantly changing environment.
This makes it difficult for teachers to understand the deci-
sions and the solution. Evaluation of tasks at regular inter-
vals is therefore essential. This makes it possible to guide
and intervene in case of problems.
Performances
and solution
approach
The assessment of individual learning must be carried out
by deriving the overall solution, thus ensuring that learners
receive the assessment that corresponds to their performance.
This is made possible by using this approach. In an exercise,
the technology allows the individual learner’s performance
to be tracked and assessed.
Lessons learned It is a repetition of the learning objectives in connection with
the knowledge and skills that have been obtained. The pur-
pose of this is to show the learner how the steps relate to each
other and to support the learner to use this knowledge in sim-
ilar cases in the future or to integrate it into new approaches.
The components and individual approaches pre-
sented in this model are designed to support teachers
in their educational activities. For learners, the model
provides a practical education with the integration of
disciplines that are not part of their studies. The im-
plementation of the model is a process that needs to be
carried out over a longer period of time. However, it
is important that both target groups find their require-
ments and needs reflected in the teaching method.
3.3 Outcomes Addressing the Target
Groups
The focus of teaching is always on transferring
knowledge, skills, competences and reaching objec-
tives. That is also the case in the developed model
for CS education. In this model, not only learn-
ers reach objectives and outcomes but also educa-
tors gain knowledge and competences. Consequently,
this model can also be seen as a method of life-long
learning. This means that through each iteration of
the model, the educator’s development is enhanced
and can be better tailored to the requirements of the
learner. The results of both target groups are pre-
sented below.
3.3.1 Learner Outcome after a Session
The methodology focuses on the holistic understand-
ing of CS as well as on the personal and methodologi-
cal development of the learners. The following points
describe only a part of the outcomes that the learners
achieve, but these are crucial.
Skills capabilities and competences: Through the
exercises and the various theoretical teaching options,
the model offers learners the creation and further im-
provement of skills, competences and capabilities in
the field of CS, but also in associated subject areas.
The application also strengthens the learners’ confi-
dence on their own capabilities and leads to higher
quality results in more in-depth training programmes.
Therefore, learners are constantly challenged to apply
these skills.
Awareness raising for CS topics: For future em-
ployment it is essential that all learners, not only
computer scientists, are aware about CS topics. The
model actively supports this by focusing on interdisci-
plinary approaches and by providing a framework for
the development of a CS awareness among all learn-
ers. Guiding learners to the topics and involving them
more in the teaching leads to a lower threshold and
awareness raising and therefore to an overall increase.
Interdisciplinary knowledge and perspectives:
The integration from disciplines which are not related
to computer science and the integration of learners
from this discipline in the exercises ensures that both
sides acquire knowledge from the corresponding dis-
cipline. This is supported by the joint elaboration of
solutions and the integration of the individual special-
ist knowledge into the solution.
Practice-oriented training: A fundamental compo-
nent of the model is the practical exercise and elabo-
ration to solve problems. The harmonisation of the-
oretical lessons with the scenario-based approach en-
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
372

ables the use of various exercises. In this way, the
proportion of practice sessions can be increased and
current topics can be integrated into the programme.
These practical exercises foster the development of
skills and capabilities and increase the understanding.
There are other outcomes that can be achieved in
the area of learning, these have not included in the list
because of the prioritisation process.
3.3.2 Educators Outcome after a Session
The model provides educators various opportunities.
It is essential that educators embrace the process and
overcome barriers in order to collaborate more and
obtain outcomes.
Additional teaching materials: Teaching materials
have to be constantly reworked in order to be up to
date. New materials also regularly need to be gener-
ated as a result of the changes in the programmes. The
model supports the educators in this process. Through
the experiences they make, the educators receive indi-
cations of where improvements are necessary. Learn-
ers contribute to this process with their solutions. This
gives educators the opportunity to incorporate solu-
tions to show examples to other learners. On the other
hand, learners contribute by producing documents.
These can serve as a basis for new exercises.
Experience, skills, capabillities and competences:
Teachers build experience and develop new ideas
through each iteration. By designing exercises, they
develop and sharpen skills, capabilities and compe-
tences as they engage with known and new subject
areas and develop a new perspective. The model sup-
ports the teacher in reaching the results by requiring
the teacher to actively engage in the construction of
the learner’s skills and competences, expanding their
own as well. On the other hand, they are supported by
the multiple possibilities that the model offers them.
Interdisciplinary cooperation: In the exercises, ed-
ucators have the opportunity to teach across disci-
plines. This may lead to new collaborations, and also
to cooperation with other teachers in other countries.
This will also broaden their perspectives and there-
fore lead to an increase in personal skills. The model
supports this in the sense that they are always con-
fronted with interdisciplinary challenges and have to
strategise to integrate these challenges. Educators can
initiate and build up the collaborations.
Integrated training of young educators: The train-
ing of young educators confronts HEIs with specific
challenges. Resources for training young educators
are limited most of the time. The model provides as-
sistance to educators and higher HEIs in this process
by integrating young educators into the exercise and
allowing them to develop their skills. In addition, the
young educators can develop individual approaches
and provide new perspectives. This leads to a situa-
tion where gaps in training can be bridged and young
educators are not overwhelmed when they are first de-
ployed.
4 EVALUATION
To evaluate the effectiveness of the teaching model for
CS, an interactive lecture and an exercise was carried
out concerning the topic of forensics and examined
with a test. Three groups of participants were selected
to be part of the evaluation. The first consists mostly
professionals from the field of CS, hereafter referred
to as A, who have been working or researching in the
field at least for 5 years. They carried out the exer-
cise and established a threshold. It was not expected
that the other groups of participants would reach this
threshold. The second group of participants, hereafter
referred to as B, consists of young professionals in CS
or young researchers who have just completed their
studies. This represents the reference value for the
third group of participants, the learners. They have re-
ceived all the necessary documentation and have been
supervised throughout the process. The last group of
participants is made up of learners, hereafter referred
to as C, from the field of computer science in the un-
dergraduate (Bachelor’s) or postgraduate (Master’s)
stage. Learners are selected only if they have not had
any explicit lessons related to the topic in their stud-
ies. This should ensure that all learners participate in
the test with the same prerequisites.
Participants from groups A (3 participants) and B
(5 participants) carried out the exercise under labo-
ratory conditions. They were observed throughout
the experiment and all actions and conversations were
recorded and documented with their consent. Group
A carried out the exercise in 15 minutes using their
knowledge and acquired skills. They proceeded me-
thodically and goal-oriented and were thus able to
work out the task quickly and answer all questions.
Group B first had to familiarise themselves with the
setting. They completed the exercise in 45 minutes
on average. They spent a lot of time analysing indi-
vidual files and had to understand the relationships.
When they identified the vulnerability and researched
about it, they were able to answer all the questions
and complete the exercise positively.
For group C (72 participants), the interactive
lecture and exercise was divided into two different
modes. The participants in the first mode took part
in the interactive lecture and then had to complete a
test with 10 questions within 24 hours. They had 30
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
373
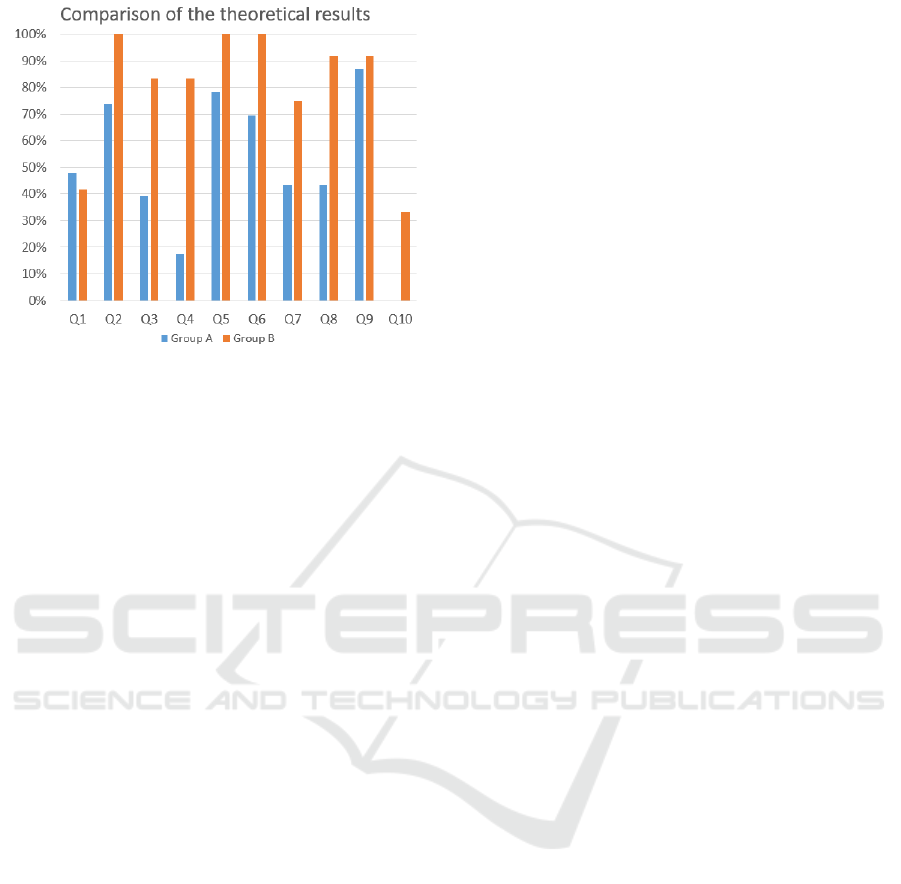
Figure 3: Test results.
minutes to answer the questions and could attend in
the technical exercise after that. The participants in
the second mode also attended the interactive lecture
and performed the technical exercise two weeks later.
After completing the exercise, the group had to an-
swer the test with the same questions.
Results of the Knowledge Assessment: The re-
sults of the knowledge assessment are shown in Fig-
ure 3. The results of the group that performed the test
after the interactive lecture are shown in blue, while
the results of the group that performed the test after
the exercise are shown in orange. It was possible to
answer the questions correctly, incorrectly or partially
correctly. Partially correct answers were marked as
incorrect in the binary evaluation.
The second group performed better in 9 out of
10 questions. About 38% of the participants in this
group answered the last question correctly, whereas
none of the participants in the first group did so. The
first question was the most outstanding; here the first
group performed better. This question is directly con-
nected to the contents of the lecture and does not oc-
cur on the exercise in this form. About 50% of the
learners in the first group had passed the knowledge
assessment and about 80% in the second group. An
improvement of 30% appears in a practical exercise
within a cyber range that also has a strong connection
to the theoretical topics..
Performance in the Exercise Compared to All
Participant Groups: For the practical exercise, the
learners (36 participants) of group C formed teams
of three individuals. This enabled the model and the
participants to reach their full potential. They had 60
minutes to solve the task assigned to them. The chal-
lenge was an implementation of the CVE-2019-11043
vulnerability and the learners had to find out how the
attackers got into the system, what activities they per-
formed and which evidence they left in the system.
From the 12 teams that participated, 3 teams were
not able to solve the task in time. They attempted
to apply the methods and strategies they had learned,
but according to their own statements, their techni-
cal knowledge was not so advanced that they could
have handled it better. The remaining 9 groups com-
pleted the task in time. 4 groups completed the task
in 35-40 minutes. This means that they have largely
undercut the reference value. The remaining groups
in the exercise came close to the reference value, with
an average time of 48 minutes.
5 DISCUSSION OF RESULTS
The objective of this work is to enhance CS educa-
tion and training with a newly developed model that
utilises a cyber-range environment as a central edu-
cational tool. For this purpose, the requirements and
needs of educators and learners are collected through
surveys, interviews and workshops and incorporated
into the model. Educators and learners are clearly not
the only actors involved in CS education which have
requirements to the design of the educational pro-
gramme. Therefore, also the external conditions are
included in the analysis as in the model. In a second
step, the teaching concept was examined in a practi-
cal setting. The objective with this step is to ensure
that the model significantly improves the educational
situation and that knowledge, competences and skills
can be acquired. For this purpose, the learners had to
work on a topic which is not part of their degree pro-
gramme. A comparison between experts and learners
was therefore possible and the improvement could be
defined on a quantitative level.
Our evaluation of the interactive lecture has
yielded the following results. The learners are much
more active and engaged than in the classical lecture.
It was possible to immediately verify understanding
based on the learners’ answers and thus to react and
adjust before the learners acquired inaccurate knowl-
edge. An important aspect for the achievement of the
programme’s objectives. Feedback from learners af-
ter the event was also positive. The results of the
Q&A show that a purely interactive lecture is not suf-
ficient to convey complex topics. The results can only
be significantly improved by applying learning in a
coordinated exercise after the lecture. With a purely
interactive lecture, the percentage of correct answers
in the experiment at 50%, see Figure 3 and Table 9.
The combination of the exercise and the interactive
lecture increases the percentage of correct answers in
the experiment to 80%. Thus, a 30% increase in per-
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
374
Table 9: Performance of the participant groups ”Lecture”.
Type Average of correct
answers
Improvement
Interactive lecture 50 % /
Interactive lecture with exercise 80 % 30 %
formance could be achieved in the experiment by ap-
plying the model.
A learner-centred approach including interactive
components is a reasonable extension of current
teaching methods. Learners are more involved and the
transfer of theoretical knowledge will be improved.
Educators have to invest more effort in the develop-
ment of the materials. The amount of material they
have to prepare is in the dual mode restricted in vol-
ume, they have to include less illustrative examples to
convey the content. As educators are guiding learn-
ers in the elaboration of the content, learners have to
engage more intensively with the content. Auditing
and maintenance of the teaching materials is simpli-
fied due to the limited scope.
A new approach to the exercises is developed and
tested during the work. The methodology for the ex-
ercise is based on existing approaches and methods.
For this purpose, several approaches are evaluated.
The aim here is to integrate the advantages of all ap-
proaches to overcome or mitigate the disadvantages
in order to design a concept that enables all learners
to learn CS. The key feature is a cyber-range environ-
ment which facilitates the construction of scenario-
based content and provides realistic hands-on train-
ing with the virtualised infrastructure. The exercise is
conducted in the same way as the lecture with learners
and additionally with two reference groups consist-
ing of experts and researchers from the field of CS.
All groups performed the exercise in the same way,
whereby the scenario was designed in such a way that
theory and exercise complement each other.
The Table 10 shows the performance of the partic-
ipant groups in terms of minimum, maximum and av-
erage processing time. Furthermore, the table shows
the percentage improvement compared to the average
reference time. The learners’ results were divided into
two parts. The first group of learners is below the ref-
erence time with their average processing time. The
learners in this group achieved an approx. 15% bet-
ter average time by completing all tasks. The second
group is about 8% above the reference time. This ap-
proximation was the expected result from the model.
The experts’ results were within the expected
scope and provide a reference value for the other
groups. The group of young researchers from the
field of CS elaborated the exercise within the given
parameters of the exercise. They chose and carried
out a methodical approach. To do this, they used their
Table 10: Performance of the participant groups ”Exercise”.
Group Max
time
Min time Avg time Percentage
comparison
Expert 16:21
Minutes
14:10
Minutes
15:15
Minutes
34.2312 %
Young professionals 47:52
Minutes
39:14
Minutes
44:33
Minutes
100 %
Leaner ”Below the
reference value”
40:03
Minutes
35:28
Minutes
37:45
Minutes
84.7362 %
Leaner ”Over refer-
ence value”
58:53
Minutes
45:46
Minutes
48:24
Minutes
108.6419 %
acquired knowledge and competences and related the
task to similar problems and worked out a solution
approach and procedure. The learners’ results range
across the spectrum. However, it is impossible to ex-
pect that all learners will complete a course positively,
despite the best teaching method. Each person is dif-
ferent, depending on the knowledge they have. The
majority of learners completed the exercise success-
fully and were able to achieve the objectives of the
exercise. Their developed solutions is based on both
the knowledge gained and the knowledge learned in
the interactive lecture. Some learners exceeded the
results of the reference group, the majority completed
the exercise in the expected range with good results.
Teachers need to restructure their course to apply
the model and thus spend resources to design teach-
ing materials, exercises and scenarios. They also have
to go through several cycles to find an optimal mode
between theory and practice. The central teaching
tool in the model is the cyber range, so it is important
to develop an EDU range which includes the limited
technical resources as well as the short preparation
time of the educators. The applicability of the Cyber
Range must also be given to learners from technical
and non-technical studies.
6 CONCLUSION AND FUTURE
WORK
The digitisation process in all areas of daily life makes
it increasingly important for all individuals in soci-
ety to develop a general awareness of CS issues and
therefore to receive training and education in CS. As a
result, HEIs and Training Institutions are challenged
to develop a programme that enables individuals to
be trained in CS. They need to develop a programme
which enables them to carry out the training. These
programmes should not limit their focus on the qual-
ification of technical staff but also include service
teaching of other disciplines.
The model for CS education with a cyber range
environment as a knowledge transfer method pro-
vided in this work aims to improve education as well
as the transfer of skills, abilities, and competencies.
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
375

In this regard, this model puts the emphasis on in-
tegrating the requirements and needs of the educa-
tors, learners, and external factors. For this purpose,
this work has evaluated different teaching approaches,
the current CS environment and the requirements and
needs of educators and learners, and has analysed po-
tential cascading effects.
The survey results are used to conceptualise and
implement the model, resulting in a theoretical and
practical lesson. They serve to evaluate the model as
well as the integrated approaches. The evaluation fol-
lowed a two-stage procedure. In the first stage the
acquisition of knowledge with an interactive lecture
session was evaluated. In the second stage, a tailored
practical teaching session with a cyber range envi-
ronment was carried out in addition to the interac-
tive session. This showed that the results regarding
the learners with the exercise were significantly better
than without. In order to compare the results from the
learners, the exercise was additionally conducted with
experts and young researchers from the field of CS.
The learners achieved the similar results as the young
researchers in the field of CS by using the model, and
in some cases they even performed better than them.
This work provides a basis for delivering CS edu-
cation to everyone. However, more broadly based sur-
veys are still needed across all disciplines to ensure
that all learners’ and educators’ needs and require-
ments are integrated. This needs to include learners
of all disciplines - and the same needs to be done
with educators. The assessment must include non-
technical concerns as well. This will ensure that exer-
cises and theoretical lessons do not miss the require-
ments and needs of the target group. Another impor-
tant aspect is that the requirements of the labour mar-
ket are also included. Then the developed model will
be able to cover the relevant areas and provide train-
ing in the field of CS for everybody.
REFERENCES
Anderson, J. R. (2013). Cognitive skills and their acquisi-
tion. Psychology Press.
Andres, P. e. a. (2020). Undergraduate educational system
of technical teacher education in the czech republic.
R&E-SOURCE.
Boud, D. and Solomon, N. (2001). Work-based learning:
a new higher education? McGraw-Hill Education
(UK).
Coneus, K. e. a. (2009). Noncognitive skills, school
achievements and educational dropout.
Crumpler, W. e. a. (2019). The cybersecurity workforce gap.
JSTOR.
ENISA (2019). ENISA threat landscape report 2018: 15
top cyber threats and trends. Publications Office.
Flechsig, K.-H. (1996). Kleines Handbuch didaktischer
Modelle. Neuland-Verlag f
¨
ur lebendiges Lernen.
Graham, C. R. (2006). Blended learning systems. The hand-
book of blended learning: Global perspectives, local
designs, 1:3–21.
Hu, Y.-H., Xing, J., and Tu, L.-P. (2018). The effect
of a problem-oriented teaching method on university
mathematics learning. EURASIA, 14(5):1695–1703.
Kebritchi, M. e. a. (2017). Issues and challenges for teach-
ing successful online courses in higher education: A
literature review. Journal of Educational Technology
Systems, 46(1):4–29.
Kelly, J. A. (1982). Social-skills training. Springer New
York.
Kraft, S. (1999). Selbstgesteuertes lernen. problembere-
iche in theorie und praxis. Zeitschrift f
¨
ur P
¨
adagogik,
45(6):833–845.
Lehmann, M. e. a. (2008). Problem-oriented and project-
based learning (popbl) as an innovative learning strat-
egy for sustainable development in engineering edu-
cation. European journal of engineering education,
33(3):283–295.
Leitner, M. and Frank, M. e. a. (2020). Ait cyber range:
flexible cyber security environment for exercises,
training and research. In Proceedings of the European
Interdisciplinary Cybersecurity Conference, pages 1–
6.
Marius-Costel, E. (2010). The didactic principles and their
applications in the didactic activity. 7(9):24–34.
Marvell, A. e. a. (2013). Students as scholars: evalu-
ating student-led learning and teaching during field-
work. Journal of Geography in Higher Education,
37(4):547–566.
Meyer, M. A. (2005). Die bildungsgangforschung als rah-
men f
¨
ur die weiterentwicklung der allgemeinen didak-
tik. pages 17–46. Springer.
Millis, B. e. a. (1997). Cooperative Learning for Higher Ed-
ucation Faculty. Series on Higher Education. ERIC.
Motschnig-Pitrik, R. e. a. (2002). Student-centered teach-
ing meets new media: Concept and case study. Edu-
cational Technology & Society, 5(4):160–172.
O’Neil, H. F. (2014). Learning strategies. Academic Press.
Onwubiko, C. (2017). Security operations centre: Situa-
tion awareness, threat intelligence and cybercrime. In
2017 International Conference On Cyber Situational
Awareness, pages 1–6. IEEE.
Ozdamli, F. and Asiksoy, G. (2016). Flipped classroom
approach. Educational Technology: Current Issues,
8(2):98–105.
Palmieri, P. (2021). SPOD Laboratory.
Shi, H. (2017). Learning strategies and classification in edu-
cation. Institute for Learning Styles Journal, 1(1):24–
36.
Sobiesk, E. e. a. (2015). Cyber education: a multi-level,
multi-discipline approach. In 16th annual conference
on information technology education, pages 43–47.
ICISSP 2022 - 8th International Conference on Information Systems Security and Privacy
376

Vasiliev, V. e. a. (1996). Interdisciplinary engineering edu-
cation: a problem-oriented approach. In Technology-
Based Re-Engineering Engineering Education Pro-
ceedings of Frontiers in Education, volume 2, pages
954–957.
Yijun, W. (2011). Research on adult and continuing edu-
cation based on distance education. In Symposium on
IT in Medicine and Education, volume 2, pages 486–
489.
A Tailored Model for Cyber Security Education Utilizing a Cyber Range
377
