
A Formal Approach for Complex Attacks Generation based on Mutation
of 5G Network Traffic
Zujany Salazar
1 a
, Fatiha Zaidi
2 b
, Wissam Mallouli
1 c
, Ana Rosa Cavalli
1 d
,
Huu Nghia Nguyen
1 e
and Edgardo Montes De Oca
1 f
1
Montimage EURL, Paris, France
2
Université Paris-Saclay, CNRS, ENS Paris-Saclay, Laboratoire Méthodes Formelles, 91190, Gif-sur-Yvette, France
Keywords:
Formal Approach, Mutation Technique, Network Traffic, 5G Networks, Fuzzing Techniques.
Abstract:
We present a formal approach based on mutation techniques for the modelling of cybersecurity attacks and
its application to 5G networks. We introduce formal definitions of the main concepts of network protocols,
mutation operators, flow of network packets and network traffic. We design a formal approach based on
different mutation operators that allows to design models that can be assimilated with known and unknown
attacks. This approach has been implemented in our open source 5G network traffic fuzzer, 5Greplay, and has
been applied to two use cases that are representative of attacks against 5G networks.
1 INTRODUCTION
Different techniques have been developed in order to
detect and execute attacks in 5G networks. One of
the techniques used is fuzz testing, which is a soft-
ware testing technique that relies on the injection of
random, invalid or unexpected data to cause the mal-
functioning or a crash of the system.
The work described in this paper extends the re-
search and open-source solution 5Greplay, presented
by the authors in (Salazar et al., 2021). Notably, in
this paper, we present a formal approach based on
mutation techniques for the modelling of cybersecu-
rity attacks and its application to 5G networks, that
we demonstrate by means of our 5G network traffic
fuzzer, 5Greplay.
The idea is to develop a formal approach based
on different mutation operators that will allow to de-
sign models that can be assimilated with known at-
tacks and with 0-day attacks. Attacks can be simple
attacks consisting of simple actions, or more complex
attacks based on the composition of different actions.
This approach will facilitate the description and exe-
cution of attacks in order to check the robustness of
a
https://orcid.org/0000-0002-8655-0585
b
https://orcid.org/0000-0003-3414-8815
c
https://orcid.org/0000-0003-2548-6628
d
https://orcid.org/0000-0003-2586-9071
e
https://orcid.org/0000-0002-5778-0752
f
https://orcid.org/0000-0001-6771-0689
5G networks and their components. It will also facili-
tate the automated detection and design of mitigation
techniques to resist attacks.
The main contribution of this paper is the design
of a formal approach for mutation techniques by in-
troducing a formal definition of the concepts of net-
work protocol, mutation operators, network packet,
flow of network packets, network traffic, as well
as, the notion of independence of network protocols
fields, packets and flows.
The paper is organized as follows: Section 2 in-
troduces related work; Section 3 presents the 5G net-
work fuzzer; Section 4 presents the formalization of
the network mutation functions, and Section 5 the ex-
perimentation to illustrate our approach. Finally, Sec-
tion 6 provides the conclusion and perspectives.
2 RELATED WORK AND
BACKGROUND
In this Section we present the research works that deal
different topics of this paper, and the gaps we could
identify in the literature.
2.1 5G Core Network
5G networks divide the LTE core and implement net-
work functions separately, so that they can run inde-
pendently from each other. Moreover, 5G network
234
Salazar, Z., Zaidi, F., Mallouli, W., Cavalli, A., Nguyen, H. and Montes De Oca, E.
A Formal Approach for Complex Attacks Generation based on Mutation of 5G Network Traffic.
DOI: 10.5220/0011319000003266
In Proceedings of the 17th International Conference on Software Technologies (ICSOFT 2022), pages 234-241
ISBN: 978-989-758-588-3; ISSN: 2184-2833
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved

functions are virtualized, therefore they do not need
dedicated hardware. 5G core Service-Based Archi-
tecture proposed by the 3GPP
1
is composed of the
following major components (Brown, 2017):
1. The Access and Mobility Management Function
(AMF) is as a single-entry point for the UE con-
nection. Based on the service demanded by
the UE, the AMF selects a Session Management
Function (SMF) for handling the user session.
2. The User Plane Function (UPF) transports the IP
data traffic (user plane) between the User Equip-
ment (UE) and the external networks.
3. Further functions like the Session Management
Function (SMF), the Policy Control Function
(PCF), the Application Function (AF) and the
Unified Data Management (UDM) function man-
age the policy control framework, applying policy
decisions and accessing subscription information,
to control the network behavior.
2.2 Network-enabled and 5G Protocol
Fuzzers
Dedicated fuzzers for protocols commonly used in
telecommunications have been proposed. T-Fuzz
(Johansson et al., 2014) follows a generation-based
fuzzing approach, relying on message models with
full protocol specifications to test the 3GPP Non-
Access Stratum (NAS) protocol, used in LTE and
5G networks. For the Resource Control layer (RCC)
protocol that operates between the UE and gNB, a
fuzzer based on the ASN.1 description language has
been proposed (Potnuru and Nakarmi, 2021). The
fuzzer extracts information about ongoing RRC mes-
sages by means of protocol description files of RRC
from 3GPP, and uses it to mutate RRC messages.
The adaptive fuzzer recognizes individual fields, sub-
messages, and custom data types according to spec-
ifications when fuzzing the content of existing mes-
sages.
The Next Generation Application Protocol
(NGAP) that operates between the UE and the
AMF, has been also tested with fuzzing techniques.
Mutation algorithms based on partition weight have
shown to be able to reduce fuzzing time by generating
samples that are more likely to produce anomalies in
the 5G core (Hu et al., 2022). The main limitation
of this approach is that the number of samples
that are required to test and calculate the weights
of each protocol field during the tuning phase of
1
https://www.enisa.europa.eu/publications/sdn-threat-
landscape
the algorithm, must be adequate to get an accurate
calculation of field weights, and this process could
take a considerable amount of time.
2.3 Complex Attack Definition and
Generation
In the context of this paper, we define the following
complex attacks:
• Multi-layers attacks: these attacks that are com-
posed of two events happening on at least two lay-
ers (for instance, transport layer and application
layer). At the network level, this can impact at
least 2 different protocols.
• Collaborative attacks: these attacks have differ-
ent sources of packets and needs coordination be-
tween them to succeed the attack. A typical at-
tack of this kind is a Distributed Denial of Service
(DDoS) attacks.
• Multi-target attacks: these attacks targets at least
two different nodes (or virtual functions) in the
network following thus two different paths or in-
terfaces.
• Distributed attacks: these attacks combines the
two last types of attacks where we can have multi-
source and/or multi-target flows.
2.4 Mutation-based Fuzzing Testing
Formalization
Various formal bases to improve this critical fuzzing
approaches has been proposed in the literature. On
the software testing field, research (Salls et al., 2020)
has characterized the input evaluation and selection
components of fuzzing, based on static analysis con-
cepts. In their model, they define the notions of in-
put, concrete and abstract states, and how the inputs
are mapped from a concrete state trace to an abstract
state by an abstraction function. Moreover, authors
have defined some of the software fuzzing technique
using their model concepts in order to demonstrate its
generality. Their results proved that the choice and
combination of abstraction functions are significant
and can modify the effectiveness of fuzzing.
Fuzzing testing has been also represented using
mutation trees, in particular (Dong et al., 2018) ap-
plied it to an industrial control systems, in order to
improve the efficiency of the mutation process and the
insufficient amount of tests in the old fuzzing technol-
ogy for industrial control systems (ICS).
In conclusion, nowadays fuzzing testing is com-
mon practice for searching vulnerabilities. Neverthe-
less, to the best of our knowledge there is an absence
A Formal Approach for Complex Attacks Generation based on Mutation of 5G Network Traffic
235

of an unified formalism for describing network traffic
mutation. Some works have approached this problem,
but mainly in the software engineering domain. We
believe that such a formalism would improve network
security by allowing automation of test case creation,
and facilitating the creation of complex test cases sce-
narios.
The formalism we described in Section 4 differs
from the state of the art because it was specially de-
signed to mutate network protocols and also allows
the design of complex attacks. Network-enabled mu-
tation has the peculiarity that there may be depen-
dency between network packets or between packet
flows. Therefore, when mutating a packet, our for-
malism also considers the packets that depend on it,
in addition to other characteristics of its context that
we will discuss later in this article. Finally, the opera-
tors that we defined in our formalism can be combined
to create complex protocol-based attacks.
3 5G NETWORK FUZZER:
5Greplay
5Greplay
2
is an open-source solution entirely devel-
oped by the authors that generates mutants of the net-
work traffic by using mutant operators, in order to
perform specified security and functional tests on a
system, as well as, fuzzing testing. In (Salazar et al.,
2021) we presented 5Greplay mutant operators, and
rule syntax. 5Greplay needs the following elements
as an input to operate:
A filtering set of rules, that explicitly indicating
which packets must be considered and ignored, to
perform 5Greplay actions
A configuration file, that specify the default actions
to be applied on the packets that are not managed
by the rules, i.e., if they should be forwarded or
not
Network traffic, online or offline, i.e. a pcap file
When defining a 5Greplay rule, users must indi-
cate the following three elements in the rule: (i) which
packet will be processed, (ii) which action will be ap-
plied, and in the case where the actions is a modifica-
tion (iii) how to modify the packet.
Today, 5Greplay can operate over NAS-5G and
NGAP protocols. However, the tool incorporates a
plugin architecture for the addition of new protocols.
In order to perform different mutations on the incom-
ing 5G traffic, 5GReplay defined a set of mutation op-
erator that can be applied either on the packet or on
2
http://5greplay.org
the flow levels. The list of these operators are pro-
vided in the Table 1.
4 NETWORK MUTATION
FUNCTIONS FORMALIZATION
We propose a formalism to handle combinations of
mutation operators applied to network traffic. The
proposed approach relies on syntactic and behavioral
changes.
Indeed, we consider that network protocols can be
studied from several perspectives. Every protocol has
a syntax that defines sequencing of data elements or
bits that are considered to be valid, and determines
how to read the data in the form of fields
a semantic that refers to the interpretation or mean-
ing that computers give to each field, and
a behavior that considers the data in its context, this
is when the data should be sent, and how fast for
non-functionnal behavioral aspects.
To illustrate our formalism, let us consider as a
running example, a small part of Non-Access-Stratum
(NAS) protocol for 5G System (5GS)
3
. NAS-5G pro-
tocol operates between user equipment (UE) and
AMF, through 5G N1 interface. Its main function
is to support of mobility of the UE, together with
procedures such as authentication, identification, and
generic UE configuration update and security control
mode procedures.
The NAS-5G syntax is the group of rules that de-
fines, for example, that during the UE registration
procedure for mobility and periodic registration up-
date a NAS REGISTRATION REQUEST message is
composed by pieces of information of a determined
length, that must be interpreted as different fields. The
semantics of the protocol gives to the first field in the
header the meaning of the Extended protocol discrim-
inator, followed Security header type, etc. Finally,
the functional behavior determines that for instance
a NAS REGISTRATION ACCEPT message must ar-
rive after a NAS REGISTRATION REQUEST mes-
sage.
In a mutation-based fuzzing testing strategy, the
idea is to generate new test cases, called also mutants,
by making syntactic operations changes in already ex-
isting test cases, to therefore inject them into the sys-
tem under test. Ideally, the mutants must be syntacti-
cally correct in order to discard test cases that the sys-
tems under test cannot interpret. Syntactic operators
3
https://itectec.com/archive/3gpp-specification-ts-24-
501/
ICSOFT 2022 - 17th International Conference on Software Technologies
236

Table 1: 5Greplay mutantion operators.
Level Atomic operator Description
Packet, Flow
DROP Delete a packet/flow of packets
DUPLICATE Duplicate packet/flow of packets
PERMUTE Exchange the order of two consecutive packets/flow of packets
MODIFY Change a specific attribute on the header of a network packet/flow of packets
generate new network packets by making operations
in a recorded packet. The syntactically incorrect and
repeated packets must be discarded.
Moreover, mutants can be also generated by mod-
ifying the inputs from a behavioral’ perspective. This
is the packet in its context. Furthermore, these op-
erators consider the time between two packets, and
the order of the packets. Behavioral operators oper-
ate in a group of network packets, that later we will
define as network packet flows to generate a new flow
of packets with different time delay between them, re-
peated packets, or different order. Analogous to syn-
tactic operators, syntactically incorrect and repeated
sequences of packets must be discarded.
Considering the NAS-5G protocol, supposing that
the system under test is an AMF, and a test case is a
group of NAS-5G packets, that semantically consti-
tute the UE authentication procedure. A syntactical
mutant would be a NAS-5G packet with the field Ex-
tended protocol discriminator modified. A behavioral
mutant of the test case can be the same message ex-
change but with a NAS REGISTRATION ACCEPT
message before the UE sends the NAS REGISTRA-
TION REQUEST message. The AMF authentication
response would be syntactically and semantically cor-
rect, but it would violate the behavior of the protocol.
In our methodology, mutant operators can only
make changes of the syntax, and behavior of an ob-
ject. Semantic changes are not possible as the ulti-
mate objective of this formalization is to represent a
testing process, and modifying the interpretation or
meaning of a message would imply to modify the sys-
tem under test.
4.1 Basic Definitions
In the following subsection we present some defini-
tions that will be used throughout our mutation for-
malism:
Let Pr denote a network protocol formed
by i number of fields, which are or-
dered pairs of field names FD =
{ f d1, f d2, ..., f di} with input domain
D f d = {D f d1, D f d2, ..., D f di}, and field values
V = {value1, value2, ..., valuei}, such that Pr =
{( f d1, value1), ( f d2, value2), ..., ( f di, valuei)},
where valuei ∈ D f di
Let P denote a network packet formed by n number
of network protocols with input domain Dp, such
that P = {pr1, pr2, ..., prn}, where prn ∈ Dp
Let F denote a flow of network packets formed by
x number of network packets with input domain
D f , such that F = {P1, P2, ..., Px}, where Px ∈
D f
Let NT denote a network traffic formed by y num-
ber of flow of network packets with input do-
main Dnt, such that NT = {F1, F2, ..., Fy}, where
Fy ∈ Dnt
4.2 Notions of Independence
In the following subsection we define the indepen-
dence notions applied to the 4 basic concepts we de-
fined in the Section above.
Two fields are independents, if a change on the field
value of one does not affect the field value of the
other. This notion applies for fields in the same
and in different protocols in the same packet, or
for fields in different packets. We represent this
as: f di ⊥⊥ f d j
Two protocols are independent if all their fields are
independent. pri ⊥⊥ pr j
Two packets are independent if all their protocols
are independent. Pi ⊥⊥ P j
Two flow of packets are independent if all their
packets are independent. Fi ⊥⊥ F j
4.3 Mutants
Let P
′
, F
′
, NT
′
be a syntactically correct network
packet, flow of network packets, and network traffic
respectively, obtained by making a syntactic, or be-
havioral changes of P, F, NT . P
′
, F
′
, NT
′
are known
as mutants of P, F, NT .
4.4 Mutant Operators
Let R be a rule according to which P, F, or NT are
changed. R is known as a mutant operator, and it
is composed by a context γ and an action σ such that
R = {γ, σ}.
A Formal Approach for Complex Attacks Generation based on Mutation of 5G Network Traffic
237
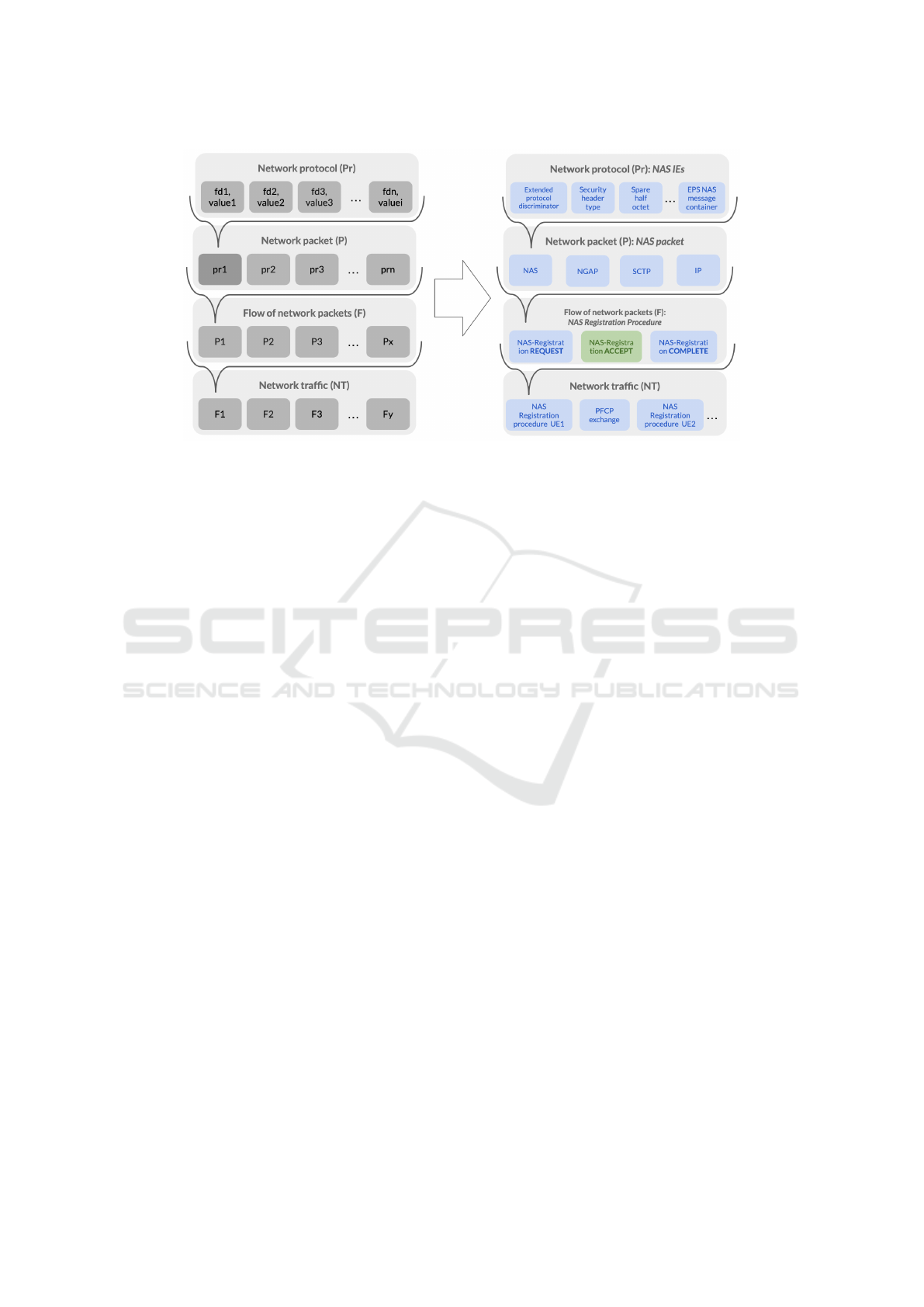
Figure 1: Summary of the basic definitions of our formalism (left), and instantiation using 5G protocols (right). Messages
sent by the UE are in blue, and messages sent by the AMF are in green.
The context determine if the operation will be per-
formed in a single packet, a flow of packets, or the
whole network traffic. It is a filter function γ of NT
with image egal to
1. A single network packet: γ : NT → P or
2. A flow of network packets: γ : NT → F or
3. The whole network traffic: γ : NT → NT
For describing the context, we use the following
notation:
γ(NT ) = [Level(P or F)].[protocol].[ f ield].[value]
Where level, indicates if the results of the filter-
ing will be individual packets (P), or a flow of net-
work packets (F). Protocol, field, and value refer to
the name of network protocol, its respective field, and
the field value according to which the filtering will be
done. For example:
1. γ(NT ) = P.NAS_5G.message_type is a function
that filters all the network packets of NAS_5G
protocol, with and specific message_type value
2. γ(NT ) = F.IP.ip_source is a function that filters
all the network flows with a specific IP source ad-
dress.
And, the action is a function σ of P, F, or NT . We
define the different actions applicable to P, F, or NT
in Sections 4.5, 4.6, and 4.7.
4.5 Mutation of a Single Packet
Let R be a mutant operator, with context γ ap-
plied to a network traffic NT , such that, the im-
age of γ(NT ) is equal to a single network packet
Pi = {pr1, pr2, ..., pri, ..., prh, ..., prn}, where Fx =
{P1, P2, ..., Pi, P j, ..., Px} ⊆ NT , there are the follow-
ing list of mutation operators applicable to Pi:
1. Drop: Drop a packet.
σ = P_DROP(Pi)
⇒ Fx = {P1, P2, ..., P j, ..., Px}
2. Duplicate: Duplicate a packet or a group of pack-
ets.
σ = P_DUPLICAT E(Pi)
⇒ Fx = {P1, P2, ..., Pi, Pi, P j, ..., Px}
3. Permute: Swap the position of Qx with Pi.
σ = P_PERMUT E(Qx, Pi)
(a) Permute Two Single Packets: Qx is a single
packet Px.
⇒ Fx = {P1, P2, ..., Px, P j, ..., Pi}
(b) Permute a group of packets: Qx is a group of
packets {Pi, P j}.
⇒ Fx = {P1, P2, ..., Px, ..., Pi, P j}
4. Modify Field Value: Change the value of field
f di, in the protocol pri, of the packet Pi, for the
value valuei
′
. As a result we get a mutation of Pi,
that we call Pi
′
.
σ = P_MODIFY(Pi, pri, f di, valuei
′
)
(a) Independent Fields: If the field f di of the
protocol pri is independent from all the other
fields on the same protocol, which is indepen-
dent from all the other protocols in the packet
Pi, then
⇒ Fx = {P1, P2, ..., Pi
′
, P j, ..., Px}, where
Pi
′
= {pr1, pr2, ..., pri
′
, ..., pn}, with pri
′
=
{( f d1, value1), ( f d2, value2), ..., ( f di, valuei
′
)}
(b) Dependent Fields in the Single Protocol: If
the field f di of the protocol pri is dependent on
ICSOFT 2022 - 17th International Conference on Software Technologies
238

a another field f dh in the same protocol, which
is independent from all the other protocols in
the packet Pi, then
⇒ Fx = {P1, P2, ..., Pi
′
, P j, ..., Px}, where
Pi
′
= {pr1, pr2, ..., pri
′
, ..., prn}, with pri
′
=
( f d1, value1), ( f d2, value2), ..., ( f dh, valueh
′
),
( f di, valuei
′
)}
(c) Dependent Fields in Several Protocols: If the
field f di of a network protocol pri is dependent
on one field f dh in another protocol prh of the
same packet Pi, which is independent from all
the other packets in its flow Fx, then
⇒ Fx = {P1, P2, ..., Pi
′
, P j, ..., Px}, where
Pi
′
= {pr1, pr2, ..., prh
′
, pri
′
, ..., prn}
(d) Dependent Packets: If the field f di of the
network protocol pri on the packet Pi is
dependent on one field f dh in another protocol
prh of another packet Px in the same flow Fx,
which is independent from all the other flows
in its network traffic NT , then
⇒ Fx = {P1, P2, ..., Pi
′
, P j
′
, ..., Px
′
}, where
Px
′
= {pr1, pr2, ..., pri
′
, ..., prn} and
P j
′
= {pr1, pr2, ..., prh
′
, ..., prn}
5. Function Composition: Two operators f and g
produces a new operator h such that h(Px) =
g ◦ f (Px) = g( f (Px)). In this operation, the op-
erators g is applied to the result of applying the
function f to Px. Operator composition is not nec-
essarily commutative. Successive transformations
applying and composing to the right agrees with
the left-to-right reading sequence.
4.6 Mutation of a Flow of Packets
Let R be a mutant operator, with context γ applied to
a network traffic NT , such that the image of γ(NT )
is equal to Fi = {P1, P2, ..., Pi, ..., Px}, where Fi ⊆
NT = {F1, F2, ..., Fi, F j, ..., Fy}, there are the fol-
lowing list of mutation operators applicable to Fi:
1. Drop: Drop all the packets contained in a flow
of packets.
σ = F_DROP(Fi)
⇒ NT = {F1, F2, ..., F j, ..., Fy}
2. Duplicate: Duplicate all the packets in a flow of
packets.
σ = F_DUPLICAT E(Fi)
⇒ NT = {F1, F2, ..., Fi, Fi, F j, ..., Fy}
3. Permute: Swap two flow of packets.
σ = F_PERMUT E(Fx, Fi)
⇒ NT = {F1, F2, ..., Fy, F j, ..., Fi}
4. Modify Field Value: Change the value of field
f di, in the protocol pri, in all the the packets Pi
of the flow Fx, for the value valuei
′
. As a result
we get a mutation of Pi, that we call Pi
′
.
σ = F_MODIFY(Fi, Pi, pri, f di, valuei
′
)
(a) Independent Flows: Fi is an independent flow
of packets from all the other flows in network
traffic NT .
⇒ NT = {F1, F2, ..., Fi
′
, F j, ..., Fy}, where
Fi
′
= {P1, P2, ..., Pi
′
, ..., Px}
(b) Dependent Flows: Fi is dependent on the flow
F j in the network traffic NT .
⇒ NT = {F1, F2, ..., Fi
′
, F j
′
, ..., Fy}, where
Fi
′
= {P1, P2, ..., Pi
′
, ..., Px} and
F j
′
= {P1, P2, ..., Ph
′
, ..., Px}
Furthermore, all mutation operators for flow pack-
ets can be seen as a composition of operators of single
packets. For example:
F_DROP(Fx) = P_DROP(P1) ◦ P_DROP(P2) ◦ ... ◦
P_DROP(Px) = {}
4.7 Mutation of a Network Traffic
The formalization described in Section 4.6 can be
generalized to be applied to the entire network traf-
fic input.
4.8 Theorems
From our formalism definitions the following theo-
rems can be deduced. These theorems allow opti-
mization of the mutation process by reducing the pos-
sible number of mutants, and they are easily provable
through mathematical manipulations.
1. PERMUTATION is commutative operation: The
arguments of the PERMUTATION operation can
be exchanged without altering the result
2. DUPLICATE and MODIFY are commutative:
Both mutant operators can be exchanged without
altering the result
3. Composition with DROP operator is always equal
to an empty flow: Any operator composition in-
cluding the DROP operator will be equal to an
empty flow
4.9 Generating Complex Attacks
The proposed formalism envisage the possibility of
combining mutation operators, in order to enable
fuzzing testing and the generation of complex attacks,
according to the definition proposed in Section 2.3.
As a first approach, we proposed the combination of
these operators to be performed randomly. Although
inefficient in terms of the number of mutations that
A Formal Approach for Complex Attacks Generation based on Mutation of 5G Network Traffic
239

we could generate, this first approach has allowed us
to find vulnerabilities in the 5G core (see Section 5).
Furthermore, thanks to the theorems proposed in Sec-
tion 4.8, the number of possible mutants can be re-
duced.
5 EXPERIMENTAL EVALUATION
To illustrate our formalism, we have formalized
the experiments we already performed in our previ-
ous work, where we presented our 5Greplay fuzzer
(Salazar et al., 2021).
We performed these scenarios against two 5G
core open-source solutions, free5GC and open5GS. In
both cases we used the RAN simulator UERANSIM.
5.1 Threat 1: NAS Replay Attack
Attackers with access to the NAS traffic (described
in Section 4) in the 5G interface N1, could intercept
a NAS SMC Security Mode command clear message
sent from the AMF to the UE, copy its NAS sequence
number (NAS SQN), and use it to build a NAS SMC
Security Mode complete message that is replayed to
the AMF, or directly intercept a NAS SMC Security
Mode complete message and replay it to the AMF. If
the AMF does not implement a proper integrity pro-
tection against this type of attack, the network will not
drop the replayed packet.
5.1.1 Formalization of Threat 1
To perform the NAS-5G SMC Replay attack, a mali-
cious actor must perform the two following actions:
• Duplicate a NAS SMC packet with a
specific Security Mode Complete field.
(NAS_5G.message_type == 93 means that it
is a SMC packet)
• Change the value of this Security Mode Com-
plete field to a lower level and recompute
the checksum of the packet. (for instance,
NAS_5G.security_type == 4 means that there will
be no encryption)
The formalization of this threat is a follow:
Let NT = {F1, F2, ..., Fi, ..., Fy}, where
Fi = {P1, P2, ..., Pi, ..., Px}, where Pi =
{pr1, pr2, ..., pri, ..., pn}, where pri corre-
sponds to the NAS_5G protocol and pri =
{( f d1, value1), ( f d2, value2), ..., (message_type,93),
..., ( f di, valuei)}. And R = {γ, σ} a mutant operator,
according to which a subset of NT will be filtered,
and mutated.
if γ(NT ) == P.NAS_5G.message_type.93 → Pi
⇒ σ = P_MODIFY (Pi, NAS_5G, security_type, 4) ◦
P_DUPLICAT E(Pi)
⇒ NT = {F1, F2, ..., Fi, ..., Fy},
Fi = {P1, P2, ..., Pi
′
, Pi
′
, ..., Px},
Pi = {pr1, pr2, ..., pri
′
, ..., pn}, and
pri
′
= NAS_5G = {( f d1, value1), ( f d2, value2), ...,
(message_type,4), ..., ( f di, valuei)}.
5.1.2 Experimentation
We implement a mutant operator in 5Greplay with
context: NAS SMC Security Mode complete mes-
sages sent by the UE after its authentication; and ac-
tion: replay it twice to the AMF. Then, we checked
the AMF logs and we monitored the network to ver-
ify that the AMF actually received the same packet
twice.
After the NAS SMC Security Mode Command
message, the AMF received a legitimate NAS SMC
Security Mode complete message, and two NGAP
packets with the same UE NGAP ID as the legitimate
user. The AMF identified this as not belonging to the
same NGAP security context. These two packets cor-
responded to the replayed packets by 5Greplay and
allow us to conclude that the free5Gc AMF is pro-
tected again this type of replay attack.
5.2 Threat 2: Denial of Service by
Sending Malformed NGAP Packets
This threat intends to check the robustness of the
AMF function by sending inconsistent values of
NGAP protocol sent over SCTP protocol. For in-
stance, we can change the SCTP protocol identifier
from 60 to 0 , and put the UE identifier of NGAP to
an arbitrary value.
5.2.1 Formalization of Threat 2
To perform this attack, a malicious actor must per-
form the two following actions:
• Change the value of the SCTP protocol identifier
to 0. (This identifier should be SCTP.protoid ==
60)
• Change the value of the UE identifier
field to a random value. (for instance,
NAS_5G.amf_UE_id == 1234 which is an
random value)
This actions can be done for an authen-
tication response identified by a message type
NAS_5G.message_type == 93. The formalization
of this threat is a follow:
ICSOFT 2022 - 17th International Conference on Software Technologies
240

Let NT = {F1, F2, ..., Fi, ..., Fy}, where
Fi = {P1, P2, ..., Pi, ..., Px}, where Pi =
{pr1, pr2, ..., pri, pr j, ..., pn}, pri corresponds
to the SCT P protocol, and
pri = {( f d1, value1), ( f d2, value2), ..., (proto_id,60)
, ..., ( f di, valuei)}; pr j corresponds to the NAS_5G
protocol, and
pr j = {( f d1, value1), ( f d2, value2), ..., (amf_UE_id,
93), ..., ( f di, valuei)}. And R = {γ, σ} a mutant op-
erator, according to which a subset of NT will be
filtered, and mutated.
if γ(NT ) == P.NAS_5G.message_type.93 → Pi
⇒ σ = P_MODIFY(Pi, NAS_5G, am f _UE_id,
1234) ◦ P_MODIFY (Pi, SCT P, proto_id, 0)
⇒ NT = {F1, F2, ..., Fi, ..., Fy},
Fi = {P1, P2, ..., Pi
′
, ..., Px},
Pi = {pr1, pr2, ..., pri
′
, pr j
′
, ..., pn},
pri = SCT P = {( f d1, value1), ( f d2, value2), ...,
(proto_id,0), ..., ( f di, valuei)}, and
pr j = NAS_5G = {( f d1, value1), ( f d2, value2), ...,
(amf_UE_id,1234), ..., ( f di, valuei)}.
5.2.2 Experimentation
We implement a mutant operator in 5Greplay with
context: NGAP protocol messages sent by the UE
during the authentication exchange; and action: re-
play them to the AMFs with two modification of the
SCTP and NAS_5G fields. Then, we checked the
AMF logs and we monitored the network to verify
that the AMF actually received the same packet twice.
When replaying against free5GC, we got an AMF
warning, but the simulator keep running and allowed
new UE connections. On the other hand, open5GS
was not able to handle this packet and the simulator
crashed, preventing new connections to the AMF.
6 CONCLUSION AND FUTURE
WORK
In this paper we have defined a formal approach for
network mutation that provides a scientific basis for
research work and application of these techniques.
Based on this formalism, we have designed models
of simple and complex attacks that we have applied
to 5G networks. The proposed approach has been
applied to two use cases that represent different at-
tacks against a 5G network. In future work, we plan
to introduce ML/AI techniques in order to improve
the perform a smart fuzzing.
ACKNOWLEDGEMENTS
This research is supported by the H2020 projects
SANCUS N° 952672, INSPIRE-5Gplus N° 871808,
and SPATIAL N° 101021808.
REFERENCES
Brown, G. (2017). Service-based architecture for 5g core
networks. Huawei White Paper, 1.
Dong, G., Sun, P., Shi, W., and Choi, C. (2018). A novel val-
uation pruning optimization fuzzing test model based
on mutation tree for industrial control systems. Ap-
plied Soft Computing, 70:896–902.
Hu, Y., Yang, W., Cui, B., Zhou, X., Mao, Z., and Wang, Y.
(2022). Fuzzing method based on selection mutation
of partition weight table for 5g core network ngap pro-
tocol. In Barolli, L., Yim, K., and Chen, H.-C., editors,
Innovative Mobile and Internet Services in Ubiquitous
Computing, pages 144–155, Cham. Springer Interna-
tional Publishing.
Johansson, W., Svensson, M., Larson, U. E., Almgren, M.,
and Gulisano, V. (2014). T-fuzz: Model-based fuzzing
for robustness testing of telecommunication protocols.
In 2014 IEEE Seventh International Conference on
Software Testing, Verification and Validation, pages
323–332.
Potnuru, S. and Nakarmi, P. K. (2021). Berserker: Asn.1-
based fuzzing of radio resource control protocol for
4g and 5g. In 2021 17th International Conference
on Wireless and Mobile Computing, Networking and
Communications (WiMob), pages 295–300.
Salazar, Z., Nguyen, H. N., Mallouli, W., Cavalli, A. R., and
Montes de Oca, E. (2021). 5greplay: A 5g network
traffic fuzzer - application to attack injection. In The
16th International Conference on Availability, Relia-
bility and Security, ARES 2021, New York, NY, USA.
Association for Computing Machinery.
Salls, C., Machiry, A., Doupe, A., Shoshitaishvili, Y.,
Kruegel, C., and Vigna, G. (2020). Exploring abstrac-
tion functions in fuzzing. In 2020 IEEE Conference on
Communications and Network Security (CNS), pages
1–9.
A Formal Approach for Complex Attacks Generation based on Mutation of 5G Network Traffic
241
