
A Decentralised Real Estate Transfer Verification based on
Self-Sovereign Identity and Smart Contracts
Abubakar-Sadiq Shehu
1,2 a
, Ant
´
onio Pinto
3 b
and Manuel E. Correia
1,3 c
1
Department of Computer Science, Faculty of Science, University of Porto, Porto, Portugal
2
Department of Information Technology, FCSIT, Bayero University Kano, Kano, Nigeria
3
CRACS & INESC TEC, Porto, Portugal
Keywords:
Self Sovereign Identity (SSI), Smart Contracts, Identity Management, Real Estate and Digital Deeds
Validation.
Abstract:
Since its first introduction in late 90s, the use of marketplaces has continued to grow, today virtually every-
thing from physical assets to services can be purchased on digital marketplaces, real estate is not an exception.
Some marketplaces allow acclaimed asset owners to advertise their products, to which the services gets com-
mission/percentage from proceeds of sale/lease. Despite the success recorded in the use of the marketplaces,
they are not without limitations which include identity and property fraud, impersonation and the use of cen-
tralised technology with trusted parties that are prone to single point of failures (SPOF). Being one of the most
valuable assets, real estate has been a target for marketplace fraud as impersonators take pictures of properties
they do not own, upload them on marketplace with promising prices that lures innocent or naive buyers. This
paper addresses these issues by proposing a self sovereign identity (SSI) and smart contract based framework
for identity verification and verified transaction management on secure digital marketplaces. First, the use of
SSI technology enable methods for acquiring verified credential (VC) that are verifiable on a decentralised
blockchain registry to identify both real estate owner(s) and real estate property. Second, the smart contracts
are used to negotiate the secure transfer of real estate property deeds on the marketplace. To assess the viability
of our proposal we define an application scenario and compare our work with other approaches.
1 INTRODUCTION
Web 2.0 is one of the many advancements that the
Internet has witnessed since its creation. It has seen
significant growth, primarily in marketplace and elec-
tronic transactions where practically anything, includ-
ing real estate, can be offered for rent, lease, or sale
on marketplaces and blogs (Facebook, Airbnb, Uni-
places and others) for residential, commercial or in-
dustrial usage. Globally, real estates are considered
one of the most valuable assets (commonly used as
collateral for obtaining loans from both formal fi-
nancial institution such as banks and informal credit
providers) (Yadav and Kushwaha, 2021), contributing
a significant share to Governments GDP. For exam-
ple in 2020 it accounted for about 7.5% of the Chi-
nese economy (Pain and Rusticelli, 2022) and 17.5%
in the USA for fixed investment and total housing
spending in 2019, real estate commercial properties
a
https://orcid.org/0000-0002-2894-6434
b
https://orcid.org/0000-0002-5583-5772
c
https://orcid.org/0000-0002-2348-8075
contributed 3.1% (EUR 452 billion) to the European
economy, a value comparable to the combined con-
tribution of the automotive and telecommunications
industries. (EPRA, 2020).More so, real estate is the
primary component of agriculture and, as a result, it is
inextricably related to food security. While properties
are easily available for buyers choice, determining
the authenticity and correctness in real estate market-
places can be a daunting challenge. Typically, inter-
actions with individuals in real estate transaction re-
quires proper identification, often with a large amount
of paperwork issued by different institutions, which
takes a lot of time to confirm from the issuers. More
so, these services are centralised and siloed, therefore,
any failure on the process can completely undermine
the progress of an entire transaction.
To curb the aforementioned issues, Governments,
businesses and researchers have been working on im-
proving the security of digital commercial transac-
tions and associated treatments of personal data. This
led to the idea of Web 3.0 (Ragnedda and Destefa-
nis, 2019) which introduces fairer and more secure
communication and data exchange methods, enabling
Shehu, A., Pinto, A. and Correia, M.
A Decentralised Real Estate Transfer Verification based on Self-Sovereign Identity and Smart Contracts.
DOI: 10.5220/0011384700003283
In Proceedings of the 19th International Conference on Security and Cryptography (SECRYPT 2022), pages 469-476
ISBN: 978-989-758-590-6; ISSN: 2184-7711
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
469

users to be sovereign on their own identity, through
decentralisation and the use of blockchains.
Self-sovereign identity and smart contract are
among the recent advances in secure data exchange
and verification. Blockchain can be used to store and
verify secure transaction, while smart contract pro-
vides an ecosystem for secure transaction negotiation,
both without the need to rely on any third party that
verifies their identity. This paper proposes an SSI and
smart contract based real estate verification frame-
work, whose aim is to prevent fraud in transfer pro-
cesses, ensure secured identity verification and miti-
gate tax evasion in transactions.
Contribution. A good number of research works
some of which are discussed in Section 2, aimed to
address these issues have focused on decentralising
the real estate registration process, while some other
works focused on identity, fraud and verification is-
sues. Therefore, we present a framework that en-
sures the secure creation, verification of VC and a
transfer process that manages real estate transaction
based on smart contracts (Szabo, 2018).This works
was inspired by our previous works (Shehu et al.,
2018)(Shehu et al., 2019) and is guided by GDPR
principles in (Voigt and Von dem Bussche, 2017).
To our knowledge no work has combined SSI, smart
contracts and IPFS peer-to-peer distributed file sys-
tem (Benet, 2014), to address real estate verification,
property transfer and associated secure data storage
issues.
The contributions of this paper are as follows:
1. Review Study: We did an extensive survey of re-
lated state of the art works on dematerialised real
estate management that uses blockchain and other
SSI components. We identified some limitations
that we address on the framework for securing real
estate transactions that we are proposing in this
paper.
2. System Framework: We propose an SSI and
smart contract framework for verifying real estate
transfer processes. The SSI layer of the frame-
work is used to define methods and the process
of acquiring VCs (electronic equivalence of our
physical documents/credentials e.g national cards
and others) (Consortium et al., 2019) for actors
(real estate, owner, buyer and marketplace) that
are linked and verifiable on a distributed ledger.
While smart contracts are used to implement the
negotiation, the real estate owner remains in con-
trol and can deploy those smart contracts at will
on a marketplace, for intending buyers to engage
with. We enhance our framework with the IPFS,
a secure distributed storage system that we use to
store a hash and an encrypted copy of the com-
plete real estate description.
3. Demonstration Pilot: To conceptualise the pro-
posed framework, we present an application sce-
nario for verification of real estate transfer, and
analyse the characteristics of each component.
4. Evaluation: From a functional point of view we
elaborated the strengths and possible weaknesses
of our proposal and propose future work.
Outline. This paper is structured as follows: Sec-
tion 3 provides a background study and associated
technologies. We discuss related works of the pro-
posed framework in Section 2. In Section 4 we pro-
vide an overview of our proposed solution and dis-
cuss it components and actors. Section 5 discusses
application scenario of the proposed framework for
use of SSI and smart contract transfer method. We
discuss security characteristics and robustness of the
proposed work and the three main components in Sec-
tion 6. We conclude the paper in Section 7 and discuss
future work.
2 RELATED WORKS
While emphasising the need for adopting blockchain
solution in real estate to enable and facilitate low-cost
P2P commercial interactions, the authors in (Norta
et al., 2018) proposed a B2B crowdfunding platform
for commercial real estate leveraging the Evareium
digital real estate fund token system, with quality
goals such as overall system security, seamless infor-
mation flow between platform sub-infrastructures. In
a bid to address fraud in buying, selling and temper-
ing with real estate records, and eliminate the use of
centralised land registry method in Saudi Arabia, the
authors in (Ali et al., 2020) proposed a blockchain
based framework using a permissioned hyperledger
fabric blockchain, in which users can utilize smart
contracts to buy, sell, and update property records.
The system keeps track of all prior purchasers and
sellers of a property, which can be validated on the
network. The work in (Gupta et al., 2020) proposed
a real estate investment solution introducing liquid-
ity using blockchain and a tokenised special purpose
vehicle for investors to purchase ERC 777 standard
security tokens at their leisure. Drawbacks of the
method include complete reliance on third-parties for
identity verification of investors, likewise the paper
work can be time consuming and prone to forgery.
The authors in (Kothari et al., 2020) proposed a trans-
parency tamper proof platform for real estate. The
SECRYPT 2022 - 19th International Conference on Security and Cryptography
470
system is composed of an owner, buyer and validator.
A major drawback of this system is the over reliance
on third party and authenticity of advertised proper-
ties are not verified. To prevent fraud in traditional
real estate transactions, the work in (Yadav and Kush-
waha, 2021) proposed a blockchain-based system for
digitising real estate transactions to reduce the risks
of fabricating documents and other fraudulent behav-
iors. In their claim, the work employs a consensus
mechanism that minimises multi casting node over-
head transmissions by 50 %. The work in (Mendi
et al., 2020) proposed a blockchain framework to re-
duce the tax evasion in real estate transactions within
Turkey, using framework used hyperledger and incor-
porating all parties involved in the transfer of own-
ership; land registry office to monitor the sale, bank
for payment of funds, municipality for tax on buyer
and seller. The authors in (Bhanushali et al., 2020)
proposed a system to address lost or damaged deeds
of real estate using a smart contract. To sell or buy
in real estate, a user fulfills the smart contract’s re-
quirements and receive a digital deed, which is then
uploaded as a new block in a blockchain. A major
drawback of this method is the non verification of the
property with a users identity. Any user who is able to
present proof of a real estate fulfills the smart contract
requirement.
3 PRELIMINARIES
Self Sovereign Identity: Self-sovereign identity
(SSI) and smart contract are among the the advances
of Web 3.0 and data decentralisation. SSI provides
a decentralised data structure, where the data owner
can be self-reliant from services, free to create their
VC (which are digital equivalence of physical doc-
uments) and revoke or delegate them at will. De-
centralised identifiers, VCs, and immutable registers
(blockchain) have been major drivers of SSI. In SSI, a
blockchain registry is a distributed ledger that is glob-
ally accepted by SSI actors as a source of truth, where
they can easily confirm the validity and authenticity
of a credential without revealing its content. Since its
introduction, SSI methods have been implemented in
a couple of areas to address trust, privacy, and secu-
rity issues in IoTs, ehealth, finance, real estate among
others. With SSI, users are able to limit the practice
of data extraction and personal information collection
by services without their consent.
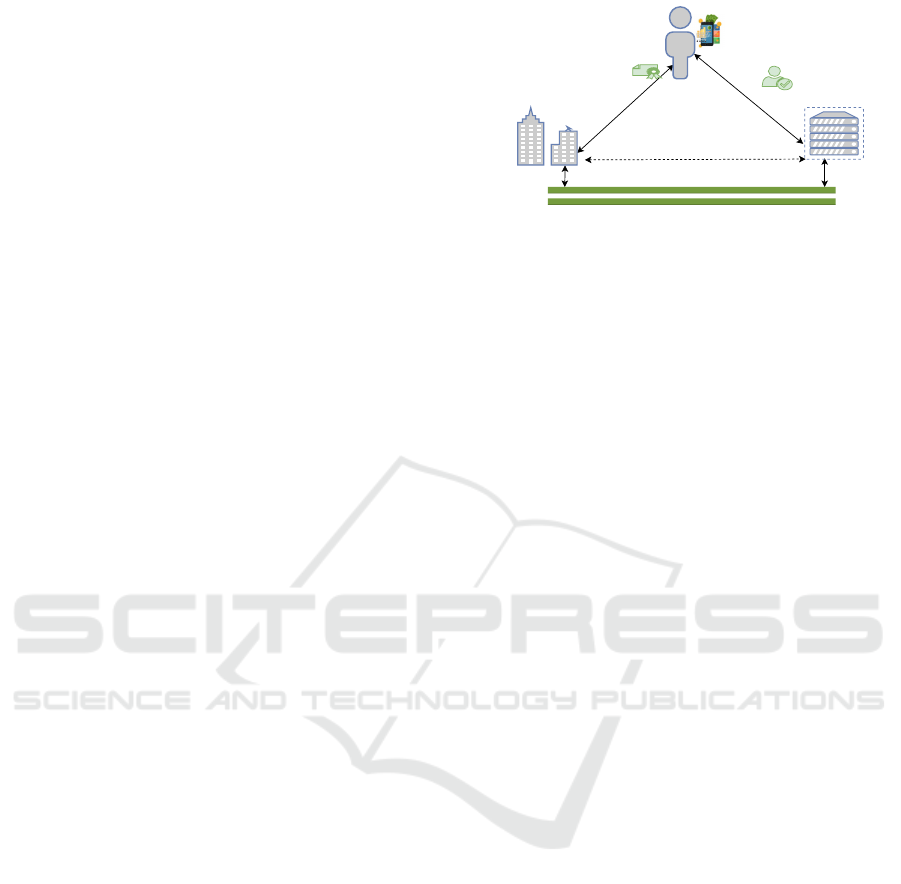
The SSI leverages on a trust triangle consisting
of three actors (issuer, holder and verifier). Issuer
is an entity that is able to verify identity attributes
of a holder and issue a VC. A holder is an identifi-
Presents credentials or
creates proofs
Credential issuer
Verifiable Data Registry
Issues credential
to holder
Digital wallet
Verifier
Trust
stores credential
in wallet
Identity owner
Figure 1: Self-Sovereign identity trust triangle.
able entity that receives credentials from issuers, then
presents them as proof of claim to a verifier. Veri-
fiers are service provider (SP), that sets access policy
for holders and provide their services based on the
policies. The relationship between these actors is de-
picted in Figure 1.
Blockchain: In 2009, blockchain attracted the
world’s attention through the first known real-world
application of bitcoin cryptocurrency (Nakamoto,
2008), as a distributed and decentralised system con-
sisting of an immutable public database, that are cryp-
tographically hashed in peer-to-peer public transac-
tions. A block is made up of a series of transactions
that are not managed by a single centralised organisa-
tion, but are instead publicly available and trustwor-
thy to all network users. Traditionally, blockchains
are classified either as public and private (Soltani
et al., 2021), or as permissioned and permissionless.
Blockchain shares a consensus algorithm that al-
lows immutable transactions to be completed and syn-
chronised, it also generates an ordered list of stored
and associated information through a chain of blocks
that usually contain the previous hash block, data
content, participant signature and timestamp. The
previous hash block causes the information in the
blockchain to remain immutable.
Smart Contract: The first published work on smart
contract was by Nick Szabo in 1994 (Szabo, 2018).
Smart contracts are digital contracts that are stored
on blockchain they are akin to physical contracts.
They inherit the properties of blockchain such as im-
mutability, distributed and trustless network. Typi-
cally smart contracts are used to automate the execu-
tion of an agreement that is triggered through proto-
cols and conditions, so that all participants are imme-
diately certain of the outcome, without the involve-
ment of an intermediary or the loss of time.
Interplanetary File System (IPFS): IPFS is an
open-source set of protocols (Benet, 2014) which in-
A Decentralised Real Estate Transfer Verification based on Self-Sovereign Identity and Smart Contracts
471
SSI
layer
Transparent
information,
communication and
modalities for the
exercise of the rights of
the data subject
Secured data
correlation
Cryptography
Blockchain
Zero
knowledge
proof
Proxy
re-ecnrytpion
Fuzzy
extractor
Pseudonymisation
& minimisation
Transparency
awareness, secure
transmission and
storage
IPFS
Access
control
Blockchain
RAIAP:
Pseudonimity
and data [104]
Interoperable
GDPR data
sharing [52]
Risk
minimisation
in sharing
data [121]
1. Securing rights of
data subject [119]
2. Enabling trust in
healthcare data
exchange with
Federated blockchain
[71]
3. GDPR data
complaint [30]
4. BCFL, data forensic
evidence [19]
1. Transparent
logging [118]
2. Trust, secure data
sharing and storage
[109]
3. Medsba: a novel
and secure scheme to
share medical data
based on blockchain
technology and
attribute-based
encryption [46]
Certificate
validation and
revocation
Revocation
management
Validation
efficiency and
distribution
Blockchain
Cryptography
Blockchain
Cryptography
Pseudonymisation
Assymetric
accumulators
Zero
knowledge
proof
Offline
certificate
management
[6]
1. Verification,
revocation and re-
issuance [131][34]
2. Cross domain
authentication
and revocation
[50]
3. Certificate
status validation
[141]
4. Certificate and
Revocation
transparency
[135]
Revoked
certificate
distribution
[100]
Certificate
management
[20]
Lightweight
automated
certificate
revocation
[54]
1. Trust
management [117]
2. Secured
revocation and
filtering [58][125] [7]
Revoked
certificate
distribution
[48][47]
PKI
Authentication
Right to
restriction of
processing
personal data
Data consent,
privacy and
intergrity
Content
filtering
Blockchain
Access
control
1. DNS-IdM secure
data sharing [12]
2. GDPR IoT
compliance [21]
NOVIDChain
Privacy health
data [5]
Privacy
management in
Banking [134]
1. Privacy protection for
GDPR [31]
2.MedSBA seucre
medical data Sharing
[109]
3. PrivySharing
Pivacy-preserving data
sharing [81]
4.GDPR data
management
complaint [129]
Decentralised
key
PKI
IdM with VC
and FIDO
[26]
Cryptography
Blockchain
Anonymisation
Hashing
IPFS
Delegation
management
Control and
transparent
delegation
Access
control
Access
control
Blockchain
Cryptography
Scalable delegation
system [78]
1. Assured and
varifiable
delegation[105]
2. IoT delegation
[101]
3. Unauthorised
permission
delegation [123]
1. Access and
delegation control
[94]
2. User-managed
access delegation
[75]
3. Distributed
account
management [144]
Guardianship &
delegation
Data portability
[115]
Delegated content
erasure [108]
Transparent
information,
communication and
modalities for the
exercise of the rights of
the data subject
Right to restriction of
processing personal
data
Guardianship &
delegation
Rights of data subject
Certificate validation
and revocation
Final Edition
1
2
4
5
3
6
7
On chain
data
processing
Off chain
processing
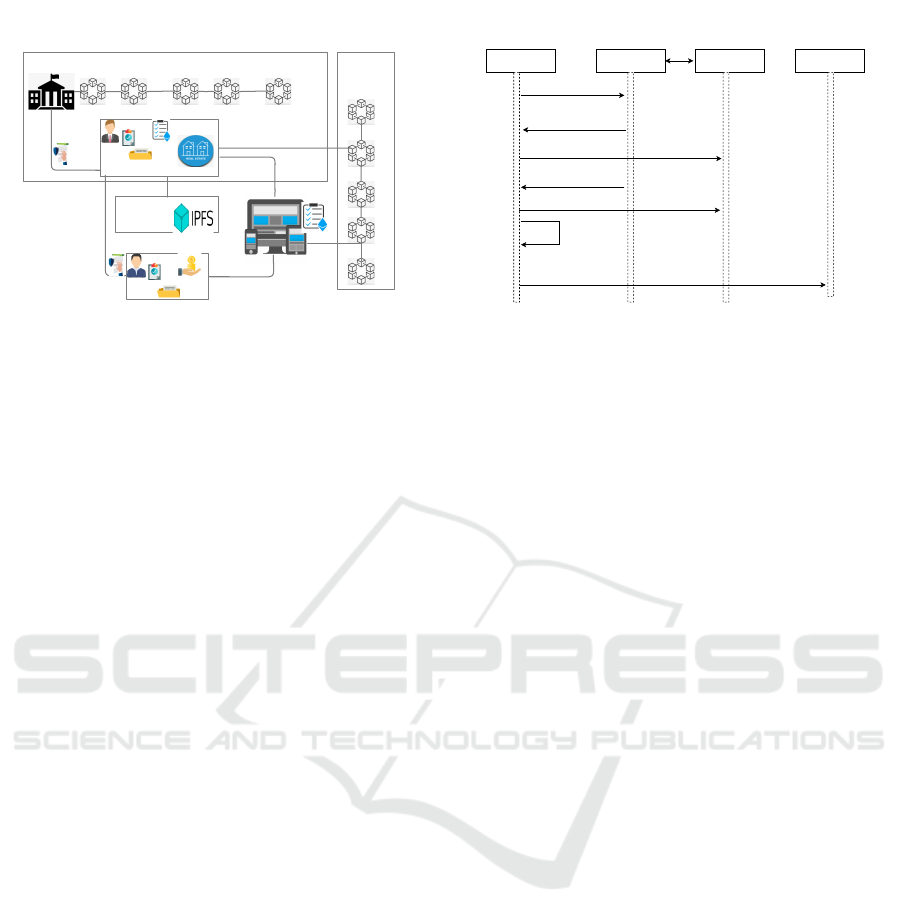
Figure 2: A high-level architecture of proposed system.
tegrates various existing concepts including peer-to-
peer (P2P) networking, Linked Data, and other do-
mains to allow participants share file fragments. Con-
tent on IPFS is uniquely labeled and addressed using a
multihash, which is a self-describing datatype that in-
corporates features from git’s versioning model, cryp-
tographic hashing, and Merkle Trees to make file re-
trieval easier. Contents are identified and accessible
using names rather than location.
4 A SOLUTION FOR VERIFIED
REAL ESTATE TRANSACTION
BASED ON SSI AND SMART
CONTRACTS
In this section we analyse the our proposal as follows:
firstly, the overall architecture is described with all ac-
tors, then, identity management and verification pro-
cess is analysed, lastly, the ownership transfer pro-
cess and data storage procedures are discussed. The
generic overview of the proposed framework is de-
picted in Figure 2. It is divided into three nodes; iden-
tity management node, on-chain data processing and
off-chain external data storage. The identity manage-
ment node which follows an SSI method.
On chain data processing node consist of two
Ethereum based smart contracts for negotiating the
transfer of real estate. While the off chain external
storage layer stores a comprehensive digital informa-
tion of the real estate (description, pictures, videos)
and ownership transfer history.
4.1 Identity Management Process
Securely verifying the real estate and users (market
place, owner and buyer) in a decentralised manner
forms the core of this work.
User
Verified Credential
Issuer
Issuer domain
Distributed external
storage
physical presentation and
proof of physical document
Pub
kuser
, Pri
kuser
)
Pass phrase
0
Pass phrase
0
1. local generation and
storage of passphrase
2. Generate hash
value for key pair and
passphrase
3. Generate a verified
certificate hash conmbination
Pub
kuser
, Pri
kuser
),
nPri
kuser
Figure 3: Owner registration process.
User Identification: Considering the fact that the
asset at hand is a physical property, we initiate the
identification process with a pre-requisite physical
identification of the owner as well as the real estate.
In the course of this work we assume the credential
issuer to be a Government/state office which owns a
distributed and verifiable data registry that stores dig-
ital information of residents and businesses. At the
state office, a user presents physical documents con-
taining personal attributes (e.g name, date of birth,
address and others) for identification on which due
diligence is conducted. For subsequent processes, an
owner may initiate a registration on the registry’s mo-
bile or web domain by creating a user name and pri-
vate key. Either way two postal mails are sent to the
user’s registered address, first mail contains a public
and temporary private key that has to be changed. A
user would then have to access the Government’s do-
main to register the credentials received and change
associated key. Once done, the system automatically
triggers the request for the second mail which con-
tains a unique and changeable mnemonic passphrase.
Owner’s account is still under verification until the
passphrase is received and changed. Once completed
owner is able to request for physical and equivalent
VC. The VC contains a public key (Pub
kowner
) that is
locally stored on owner’s digital wallet, a private key
(Pri
kowner
) that unlocks owner’s account and a hash hf
of the key pair that serves as the identity of the owner
VC
owner
=( hf (Pub
owner
, Pri
owner
), Pri
owner
, Pub
owner
).
The hash value is deposited in decentralised the reg-
istry of the issuer to uniquely identify owner. On
the decentralised state mobile or Web domain, owner
logs-in with their self generated private key and con-
firms the already provided attributes during the regis-
tration. From the key pair, owner is able to derive new
hash credentials for unique identification that will be
case specific, and even choose from an array of ser-
vices (public/private) provided, with which they want
SECRYPT 2022 - 19th International Conference on Security and Cryptography
472
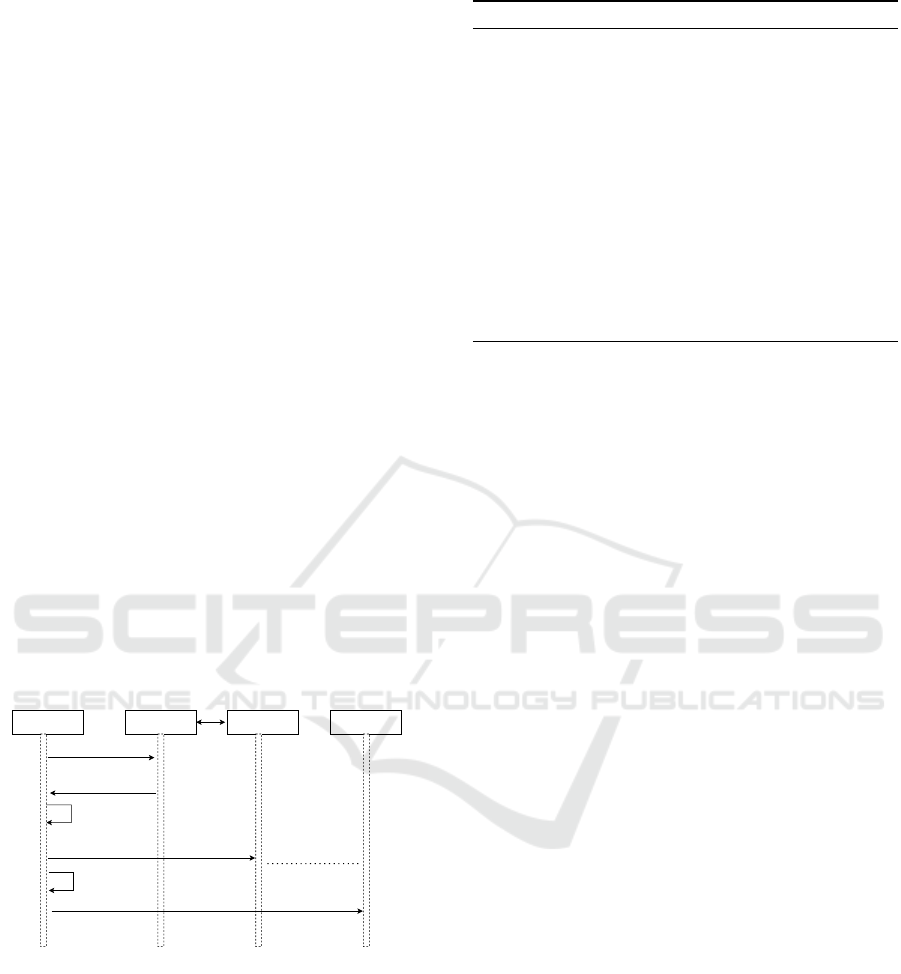
to link their identity to. This process is described
shown in Figure 3.
Real Estate Identification: Been a landed prop-
erty, real estates are owned by private or state entities,
therefore, the identification process follows similar
approach of owner identification. We assume a real
estate is newly acquired, therefore the owner needs
to obtain a VC for it, and bind it to their own VC.
At the registry office, the owner presents their VC
with proof of ownership (such as deed document or
certificate of ownership) that fully describes the prop-
erty, the map location, purchase receipt with preced-
ing owners identities (VC hashes) and a plan for the
property if any. The land registry office dispatches
two address verification mail; first to the preceding
owner of the property and second to the verified ad-
dress of the owner, which contains a key pair gener-
ated from the owner’s public key and a changeable
password for access to land registry domain to com-
plete the registration. Once received, the preceding
owner has to confirm the transfer of property using
owned VC. Thereafter, the owner is able to link the
property’s public key to VC and locate it on the land
registry map (description of this property is greyed
out and saved to a distributed external storage). A
hash is generated from the key pair, property loca-
tion on the map, owner’s VC and property public key
which is then pinned to external distributed storage
that is publicly accessible as shown in Figure 4.
Propery owner Land registry Land registry domain External storage
physical presentation, vc and
cert of ownerhsip
Pub
kproperty
locate property location on
map,
link Vc and
Pub
kproperty
Pin property hash
generate hash=
property location+
pub
k property
+ vc
greyed location as ownwed
Figure 4: Real estate registration process.
4.2 On Chain Data Processing
We assume that a buyer/client and decentralised
marketplace acquire their VCs using same process
with real estate owner. The proposed infrastruc-
ture is composed of two smart contracts that form
the bases for real estate transfer; which are capabil-
ity smart contract SC
capability
and transfer smart con-
tract SC
transfer
. Both contracts are fashioned on an
Ethereum blockchain.
Algorithm 1: SC
capability
creation.
1: procedure Owner verification and contract creation process
2: Input: acct, AP, B, start, end, minValue, DR, R
0
, VC
property
, IPFS
hash
,
status
3: Read values
4: if Id, R
0
, B, VC
property
= owner then
5: start transfer
6: if li f etime ≥ 1 then
7: Create instance of SC
capability
8: else if li f etime ≤ 0 then
9: Reject creation process
10: else
11: Create acct, AP, value, DR, status
12: while Status = active do
13: Return ← IPFS
hash
14: Return ← SC
capability
SC
capability
: This contract is created and owned by
the real estate owner, it hold’s all necessary informa-
tion that identifies them. To determine method for
proof of identity, we define SC
capability
properties in
relation to it’s attributes and enumerate what action
(access request, delegation, transfer of property and
revocation) the owner can perform with it. To achieve
this we define the access control (AC) state and iden-
tify its variables; AC (A, P, R), where A, is a set of
public keys (Pub
ku
...Pub
ku..
n
), R (set of all attributes
on VC), P (set of all possible permissions). From
these variables an owner is able to derive capability
properties for their smart contract: (AP, R
0
, Pp
0
, DR,
B), where AP ⊆ A × P is access policy, R
0
6⊂ R is a set
of extra context awareness attributes, Pp
0
⊆ P × p
0
is
access scope, DR is the delegation relation and B is
set of binary relations between entities (which could
be real estate in question or other entities).
SC
transfer
: This contract is deployed by verified
market place. Since the market place is providing the
platform for the transfer of real estate property, an ini-
tial authentication and authorisation process is carried
out.
Smart Contract Creation: To create a SC
transfer
,
we assume a marketplace defines access requirements
through scope and policies, which are achieved by
identity verification processes (identification, authen-
tication and authorisation). To initiate these pro-
cesses, an owner contacts the market place and re-
quest access to SC
transfer
services by sending a request
that includes Req
access
→SC
transfer
: acct, hashId and
Pub
Kowner
where acct is the type of contract the owner
wants to deploy (sale, lease agreements, or power of
attorney contract), hashId, is the Id of the owner who
wants to deploy a contract, and Pub
Kowner
is the pub-
lic key. We assume that each call to a market place
A Decentralised Real Estate Transfer Verification based on Self-Sovereign Identity and Smart Contracts
473

get assigned a dedicated function in the smart con-
tract which serves as the controller who is able to
lookup owner’s Id on the distributed storage. To fur-
ther verify the authenticity of the acclaimed property,
owner’s call is responded to with a challenge policy
and requests for a VC linking the owner to the prop-
erty. Once received, owner looks up on their digital
wallet to confirm if verified attributes are sufficient
enough for authentication and covers request poli-
cies, if yes, owner is required to confirm the release
of verified attributes otherwise the process is discon-
tinued with an error message that requires owner to
provide more attributes that are not available. Using
a digital wallet, user manually wraps R
0
and B ,both
properties are signed with owner’s private key so that
marketplace controller may decode it with the shared
public key: Owner →marketplace: Pri
Kowner
(R’, B).
We assume that this exchange takes place over a se-
cured end-to-end communication. Upon receipt, mar-
ketplace controller confirms identity attributes on the
ledger, signed claim, device and location binding to
the owner that made the initial request, that nonce is
meant for the specific transaction and timestamp is
valid. Once this is confirmed real estate owner is able
to create SC
capability
and an IPFS link as shown in al-
gorithm 1, while a controller reviews the contract on
marketplace’s domain and deploys it as SC
transfer
, this
is shown in Figure 5.
Figure 5: Transfer contract.
4.3 Off Chain Data Processing
Despite benefits of blockchain, its not without some
limitations which include high cost of transaction
among others(Hughes et al., 2019), for this reason de-
centralised storage solutions such as IPFS, SWAMP,
BitTorrent, Filecoin among others are used to store
huge data that can be expensive to store on chain in
conjunction with blockchain system to create a decen-
tralised database. Although ownership of real estate
can be transferred or structure modified, it remains till
eternity (atleast the land). The immutability property
of IPFS serves well for real estate data storage.
During the contract creation process, a real es-
tate owner deposits complete identity information/de-
scription of the property off chain on an IPFS net-
work, but shares a hash value of the storage on the
contract. A complete picture of the property is pro-
vided with street view, and map location. To prevent
unwanted re-use of acquired picture, each document
downloaded is watermarked with owner’s name, re-
questors Id and market place that deployed the trans-
fer contract.
5 APPLICATION SCENARIO
Leveraging on data decentralisation and trust less net-
work, we foresee that the proposed framework can
be applied for the transfer of dematerialised property
that posses a VC. However, for clarity we conceptu-
alise our proposal using a real estate transfer contract.
We assume that a buyer wants to acquire a real estate
property through a smart contract that is hosted by a
market place. The process is made up of four compo-
nents; a real estate owner that deploys SC
capability
by
calling the function of a market place, market place
deploys owner’s contract using SC
transfer
on decen-
tralised owned platform, client/buyer a bidder that ex-
presses interest on advertised property and external
IPFS storage. As described in Figure 6, the compo-
nents describe the transfer through initialisation, reg-
istration, offer and finalisation.
Initialisation: This signifies the commencement of
a transfer process where a real estate owner cumulate
already created SC
capability
as shown in Algorithm 1,
and deposits an IPFS link of the property on an IPFS
network. A function for SC
transfer
is then created to
deploy the SC
capability
.
Registration: As described in Algorithm 1, to de-
ploy the functions of SC
capability
, the smart contract
checks five conditions which includes; (1) is the con-
tract deployed by the owner (2) is the property linked
to the owner on distributed storage (3) is the start
time greater than current time (4) the market place
also calculates commission and charges on the trans-
action with government tax and requests for owner’s
approval before it is finally published (5) the owner is
not involved making an offer for transfer process.
Offers: Once all conditions are satisfied and the
marketplace deploys transfer contract, it becomes vis-
ible to the public. An owner also receives a share ID
of the contract which gives them upmost control over
the contract. or make an offer but has upmost con-
trol to start, stop or suspend the process at will. Once
the contract is running, a user who has acquired VC
through the identification process described in Sec-
tion 4.1, uses their verified certificate to request par-
SECRYPT 2022 - 19th International Conference on Security and Cryptography
474
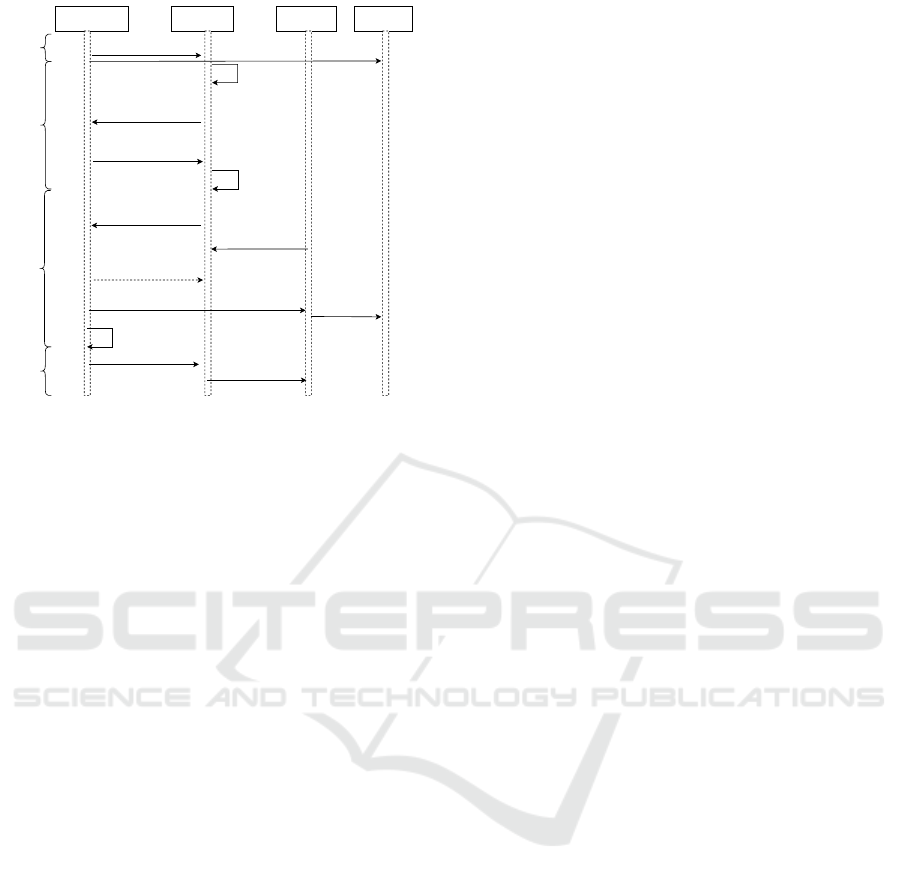
Propery owner Market Place Cleint/buyer External storage
Creates SC
capabality
for sale/lease
Obtain SC
capability,
include state
conditions
tax value and commision
Request owner's
approval for commission
and tax notification
Deploys
SC
capabality bytecodes
Implement
SC
capabality bytecodes
and deploy
SC
transaferShare deployement ID
and lifetime control
Request participation
in offer by
spending ether
owner periodically
checks process
accept or decline offer
invoke transfer process
accept/denytransfer
creates IPFS link
sends a one time
use and user spcific
acess to IPFS location
Initialiasation
Registration
Bidding
Transfer
access property
decsription
Figure 6: Real estate transfer process.
ticipation by making an offer (spending an ether) that
is equal or higher than current value of the property.
Once the offer is made, a user receives a user-specific
access to a full description of the real estate property
such as videos, picture, maintenance mode, setup and
every other information that might be deemed useful
for the transfer process. Generally, buyers are able to
view current offers of other buyers, likewise the mar-
ket place. However, only the owner is able to confirm
the full identity of a buyer.
Transfer: The owner monitors the transfer process
until the lifetime elapses (it can also increase the du-
ration or terminate the entire process when there is a
suspicion of fraud). A decision is then made to ei-
ther accept or reject offers. Buyers who wish to opt
out of the transfer process, before the last minutes are
fined from the cost paid for the transaction. Once an
offer is accepted, a buyer is informed of the process
and is requested to proceed with payment before fur-
ther transfer process is made. To further protect other
buyers a percentage of their offer is used as a gas fee
for the transaction. However, once a winner is cho-
sen, buyers are requested to proof their identity once
again in other to accept a refund for their bids.
6 ANALYSIS
From a functional point of view, we analyse the
strengths and weaknesses of the proposed framework.
We also assess their level of robustness in processing
personal information.
Robustness of Proposed Framework: The pro-
posed SSI and smart contract based real estate verifi-
cation framework follows a complete decentralisation
method. The identification, registration, verification
and identity proofing is free from central storage of
data. Therefore, there is no means for SPOF.
Issuance, identity verification process and use of
VC prevent a malicious attacker from getting hold-on
physical documents to claim ownership or steal prop-
erty. More so, with a trust-less framework, collusion
is made difficult as verifier need not to be aware of
the physical location of an issuer but can verify the
signature of any document it has issued.
Robustness of Identification and Verification:
These methods are used to capture full attributes of
users. Before a real estate VC is issued, user’s VC
need to have been acquired, therefore linking these
documents prevents false claim and other fraud as
user proofs ownership of both documents before any
transaction.
From verified attributes of a VC, user can gener-
ate self acclaimed and context based attributes that are
only linked to the VC and verifiable on the distributed
register. Therefore, to prevent profiling a user can
generate as much context based credentials for trans-
actions without been traced.
Robustness of Data Processing: Data decentralisa-
tion is among the core parts of the proposed work.
Although, one of the drawbacks of blockchain is
the use of varying standards which causes fragmen-
tation in adoption, hence interoperability between
blockchains only occurs among technologies with
same open source implementation or using a trusted
party (Bellavista et al., 2021).
To ensure that data processed for the transfer
is available, we used the IPFS open source storage
which is independently available on Web desktop and
provides sufficient memory space that lasted for upto
48hrs. Also, we assume that a completed document
signifying the transfer of property is processed off-
chain and deposited on the IPFS network.
7 CONCLUSION
In this paper we presented an SSI and smart contract-
based real estate transfer framework that can be used
to verify the identity of a genuine real estate owner,
real estate property and securely control the entire
transfer process within a digital marketplace. Our so-
lution uses a decentralised and distributed approach
to achieve the seamless verification process with data
A Decentralised Real Estate Transfer Verification based on Self-Sovereign Identity and Smart Contracts
475

integrity and personal data protection. The SSI meth-
ods ensure that only a verified real estate owner is
able to claim ownership of a property using verifiable
credentials.Those are acquired from an identity veri-
fication process and can be validated on a distributed
ledger. The smart contract is used to create the trans-
fer process by the owner and is deployed on a decen-
tralised marketplace. A distributed storage is used to
store a full description of the property which is ac-
cessible using a content identifier. We have also de-
fined an application scenario to test the validity of our
proposal. In addition we also provide a robustness
and security analysis of our framework with respect
to some specific previously identified threats. In the
future we plan to fully implement the remaining as-
pects of the framework, including the issuance of VC,
smart contract management, as well as integration of
policy makers to the framework for the issuance of tax
returns . We also hope to be able to mitigate the non
intended use of sensitive documents obtained via the
IPFS network.
ACKNOWLEDGEMENTS
This work is financed by National Funds through
the Portuguese funding agency, FCT - Fundac¸
˜
ao
para a Ci
ˆ
encia e a Tecnologia, within project
LA/P/0063/2020.
REFERENCES
Ali, T., Nadeem, A., Alzahrani, A., and Jan, S. (2020). A
transparent and trusted property registration system
on permissioned blockchain. In 2019 International
Conference on Advances in the Emerging Computing
Technologies (AECT), pages 1–6. IEEE.
Bellavista, P., Esposito, C., Foschini, L., Giannelli, C.,
Mazzocca, N., and Montanari, R. (2021). Interopera-
ble blockchains for highly-integrated supply chains in
collaborative manufacturing. Sensors, 21(15):4955.
Benet, J. (2014). Ipfs-content addressed, versioned, p2p file
system. arXiv preprint arXiv:1407.3561.
Bhanushali, D., Koul, A., Sharma, S., and Shaikh, B.
(2020). dipika. In 2020 International Conference on
Inventive Computation Technologies (ICICT), pages
705–709. IEEE.
Consortium, W. W. W. et al. (2019). Verifiable credentials
data model 1.0: Expressing verifiable information on
the web. https://www. w3. org/TR/vc-data-model/?#
core-data-model.
EPRA (2020). Real-estate-in-real-estate-economy.
https://www.inrev.org/system/files/2021-04/INREV-
EPRA-Real-Estate-Real-Economy-2020-Report.pdf.
Gupta, A., Rathod, J., Patel, D., Bothra, J., Shanbhag, S.,
and Bhalerao, T. (2020). Tokenization of real estate
using blockchain technology. In International Confer-
ence on Applied Cryptography and Network Security,
pages 77–90. Springer.
Hughes, L., Dwivedi, Y. K., Misra, S. K., Rana, N. P.,
Raghavan, V., and Akella, V. (2019). Blockchain re-
search, practice and policy: Applications, benefits,
limitations, emerging research themes and research
agenda. International Journal of Information Man-
agement, 49:114–129.
Kothari, P., Bharambe, A., Motwani, R., and Rathi,
A. (2020). Smart contract for real estate using
blockchain. In Proceedings of the 3rd International
Conference on Advances in Science & Technology
(ICAST).
Mendi, A. F., Sakaklı, K. K., and C¸ abuk, A. (2020). A
blockchain based land registration system proposal
for turkey. In 2020 4th International Symposium on
Multidisciplinary Studies and Innovative Technolo-
gies (ISMSIT), pages 1–6. IEEE.
Nakamoto, S. (2008). Bitcoin: A peer-to-peer electronic
cash system. Decentralized Business Review, page
21260.
Norta, A., Fernandez, C., and Hickmott, S. (2018). Com-
mercial property tokenizing with smart contracts. In
2018 International Joint Conference on Neural Net-
works (IJCNN), pages 1–8. IEEE.
Pain, N. and Rusticelli, E. (January 14, 2022). A sharp slow-
down in china’s property markets would damp global
growth. A sharp slowdown in China’s property mar-
kets would damp global growth, (3152676):1–4.
Ragnedda, G. and Destefanis, G. (2019). Blockchain and
Web 3.0. London: Routledge, Taylor and Francis
Group.
Shehu, A., Pinto, A., and Correia, M. E. (2019). Pri-
vacy preservation and mandate representation in iden-
tity management systems. In 2019 14th Iberian
Conference on Information Systems and Technologies
(CISTI), pages 1–6.
Shehu, A.-s., Pinto, A., and Correia, M. E. (2018). On the
interoperability of european national identity cards.
In International Symposium on Ambient Intelligence,
pages 338–348. Springer.
Soltani, R., Nguyen, U. T., and An, A. (2021). A survey of
self-sovereign identity ecosystem. Security and Com-
munication Networks, 2021.
Szabo, N. (2018). Formalizing and securing relationships
on public networks. First Monday.
Voigt, P. and Von dem Bussche, A. (2017). The eu gen-
eral data protection regulation (gdpr). A Practical
Guide, 1st Ed., Cham: Springer International Pub-
lishing, 10(3152676):10–5555.
Yadav, A. S. and Kushwaha, D. S. (2021). Blockchain-
based digitization of land record through trust value-
based consensus algorithm. Peer-to-Peer networking
and applications, 14(6):3540–3558.
SECRYPT 2022 - 19th International Conference on Security and Cryptography
476
