
Stream Data Access Control Model: The Need for Data Semantics
Theppatorn Rhujittawiwat
1
, Ahmed Saaudi
2
and Csilla Farkas
1
1
University of South Carolina, Columbia, South Carolina, U.S.A.
2
University of Al-Muthanna, Samawh, Iraq
Keywords:
Stream Data, Ontologies, Dynamic Access Control, Semantics-based Authorization.
Abstract:
In this paper, we propose a semantics-based authorization model for stream data. We demonstrate that current
authorization models are insufficient to provide dynamic access control for emerging technologies, such as
the Internet of Things. We propose an authorization model using ontologies and rules to express security
requirements for stream data. Our model supports secure interoperation and it is independent from the data
syntax. We propose security object patterns to express access control needs. These patterns are associated
with ontological concepts. Data instances inherit the security protection needs via stream pattern mapping.
Security object patterns can incorporate domain, context, and temporal security restrictions. We show that our
model is resistant to attacks that aim to bypass security restrictions by reconstructing stream data.
1 INTRODUCTION
Stream data management is an important require-
ment for emerging computing environments, such
as the Internet of Things (IoT). Initiatives, such
as IoT-Lite (Bermudez-Edo et al., 2015)(Bermudez-
Edo et al., 2016) and Stream Annotation Ontology
(SOA) (Kolozali et al., 2014), aim to support intel-
ligent interoperation. Along with the development of
IoT applications, concerns about cybersecurity threats
emerged. In this paper, we address the specific cyber-
security needs of stream data in the IoT environment.
We argue that current stream data security models do
not support dynamic security, thus, insufficient to sup-
port IoT applications.
During the last decade, several researchers ad-
dressed the need to provide data security for stream
data. Most of these models address confiden-
tiality protection for stream data. The proposed
solutions range from encryption-based end-to-end
communication security (Penrig et al., 2000)(Puthal
et al., 2015)(Puthal et al., 2017)(Veltri et al.,
2013)(Zhu et al., 2006) to proposing generic secu-
rity models (Carminati et al., 2015)(Manogaran et al.,
2017)(Mengke et al., 2016)(Nehme et al., 2008).
Communication security for stream data is widely
provided by end-to-end encryption during transmis-
sion. To further improve the performance of this
method, many researchers introduced efficient end-to-
end encryption techniques such as the dynamic key
length based approach (Puthal et al., 2015) and ap-
proaches for grouping and sharing keys (Penrig et al.,
2000)(Puthal et al., 2017)(Veltri et al., 2013)(Zhu
et al., 2006). However, end-to-end encryption tech-
niques provide confidentiality over the entire data
stream and are unable to provide fine granularity au-
thorization. These techniques are cumbersome to en-
force advanced security requirements, such as role-
based access control, context-aware security, and dy-
namic security policies.
Several researchers proposed access control pol-
icy models for stream data (Cao et al., 2009)(Carmi-
nati et al., 2010)(Carminati et al., 2007a)(Carminati
et al., 2007b)(Thoma et al., 2019). These approaches
adopt access control concepts of traditional database
management systems (DBMSs) to stream data. How-
ever, these efforts do not sufficiently address the
specific needs of data stream management systems
(DSMSs). For example, a DSMS can access only
incoming data while a DBMS can access the com-
plete data. The operator scheduling in a DSMS
significantly impacts system performance. Operator
scheduling strategies have been proposed by Carmiati
et al. (Carminati et al., 2010) and by Thoma et
al. (Thoma et al., 2019).
An enforcement of security requirements over the
stream data instance has been proposed by Nehme et
al. (Nehme et al., 2008). The security requirements
are assigned to each attribute by their positions in the
stream tuple. Their technique, called security punc-
tuation, provides efficient access control for stream
data. However, since the security punctuation is based
on the syntax of the stream data, this approach pro-
vides limited interoperability. Moreover, modifica-
Rhujittawiwat, T., Saaudi, A. and Farkas, C.
Stream Data Access Control Model: The Need for Data Semantics.
DOI: 10.5220/0011528600003335
In Proceedings of the 14th International Joint Conference on Knowledge Discovery, Knowledge Engineering and Knowledge Management (IC3K 2022) - Volume 3: KMIS, pages 19-30
ISBN: 978-989-758-614-9; ISSN: 2184-3228
Copyright
c
2022 by SCITEPRESS – Science and Technology Publications, Lda. All rights reserved
19

tion of the stream syntax may allow the attacker to
bypass the access control restrictions.
Malicious corruption of the integrity of stream
data was addressed by Guo et al. (Guo et al., 2007).
The authors proposed a watermarking method to de-
tect malicious modification of the stream data. The
authors introduced the concept of data stream com-
pleteness. While their methods are able to detect
modification of the data stream, they do not provide
a model to express protection requirements.
In this paper, we present a security model to
express security needs for stream data. Our work
is based on the intersection of stream data se-
mantics modeling and semantics-based authorization
models. Data semantics is widely used to sup-
port stream data integration and data analytics (Le-
Phuoc et al., 2011)(Whitehouse et al., 2006). Our
solution was also influenced by work to support
semantics-based authorization models (Sabelfeld and
Myers, 2003)(Choi et al., 2014) and context-based
decision support (Celdr
´
an et al., 2014)(Chen et al.,
2003)(Montanari et al., 2005).
The main contributions of our work are to 1) ex-
press security requirements via stream data semantics
and 2) support dynamic and flexible policy manage-
ment. Our focus is on the concept of protected object
patterns. These patterns represent (partial) stream tu-
ples and their combinations. Values for the tuple at-
tributes may be variables or constants, thus allowing
for the expression of security needs over varying lev-
els of granularity. We model the mapping from the
protection objects to the data instances via the cor-
responding ontologies. A protection object may be
applicable to multiple ontology concepts and a con-
cept may have multiple protection objects mapped to
it. Stream data instances inherit the security require-
ments from the security object patterns. We show that
our security label assignment provides strong confi-
dentiality protection. Syntactically different but se-
mantically same data items will have the same secu-
rity protection assignment. In this paper, we present
our functional model. We also give proof of formal
properties of our security label assignment.
The organization of the paper is as follows: Sec-
tion 3.2 discusses the motivating situations and prob-
lems which drive the direction of the solution. Section
4 defines the stream data model and security assign-
ment. Section 5.1 describes the concept of stream data
ontology. Section 5.2 illustrates logical reasoning and
how to incorporate it into security policy. Section 6
presents an example of security policy implementa-
tion using ontology. We conclude in Section 7.
2 RELATED WORK
In this section, we give an overview of current re-
search on stream data security, dynamic access con-
trol, and the limitations of these works.
2.1 Stream Data Security
Current work on stream data security focuses on con-
fidentiality (Carminati et al., 2015)(Manogaran et al.,
2017)(Mengke et al., 2016). The first priority of
stream data design is performance. To provide se-
curity capabilities with the least effect on perfor-
mance, the major methods of providing confiden-
tiality are based on end-to-end cryptography (Pen-
rig et al., 2000)(Puthal et al., 2015)(Puthal et al.,
2017)(Veltri et al., 2013)(Zhu et al., 2006). However,
end-to-end encryption techniques provide confiden-
tiality over only the whole package. They are unable
to provide fine granularity authorization, and cannot
enforce advanced security requirements, such as role-
based, lattice-based access control, or dynamic se-
curity policies. Therefore, such requirements must
be enforced by the receiving applications. Many re-
searchers introduce syntax-based security techniques
for streaming data. The security requirements are
assigned to each attribute by their positions in the
stream tuple. Nehme et al. (Nehme et al., 2008) pro-
posed a technique called security punctuation to pro-
vide efficient access control for stream data. A secu-
rity punctuation technique focuses on providing pri-
vacy control for the data source side. The current se-
curity policy is sent from the data source and specifies
the security labels of attributes in the data tuple. This
approach allows the data source side to decide the se-
curity needs which are suitable for privacy sensitive
data domains such as medical information.
The growing field of IoT has led to increasing
number of stream data applications. Many of these
applications also collect sensitive user data. To pro-
tect confidentiality and privacy of users, researchers
propose access control for IoT stream data in differ-
ent context. For example, Shafagh et al. (Shafagh
et al., 2020) proposed a decentralized access control
based on blockchain technology. Their approach pro-
vides an extra layer of anonymity for users but has
a limited security granularity. Nambiar et al. (Nam-
biar et al., 2020) extended Apache Storm to protect
privacy of the data in distributed systems. Their ap-
proach supports a variety of access control models,
such as Discretionary Access Control (DAC), Manda-
tory Access Control (MAC), and Role-Based Access
Control (RBAC).
Semantic approaches have been used in stream
KMIS 2022 - 14th International Conference on Knowledge Management and Information Systems
20

data since the field was established. However, their
main focus is on how to interpret data and use it
for data analytics (Le-Phuoc et al., 2011)(Whitehouse
et al., 2006)(Sejdiu et al., 2021). The security com-
munity has demonstrated the benefit of semantics-
based security, such as Sabelfeld et al. (Sabelfeld
and Myers, 2003)(Choi et al., 2014)(Celdr
´
an et al.,
2014)(Chen et al., 2003)(Montanari et al., 2005).
However, the potential of these approaches for sup-
porting stream data security and privacy has not been
fully investigated.
Moreover, stream data requires dynamic security
policies because it is time sensitive. The same at-
tribute in stream data may require different security
levels at different times such as healthcare informa-
tion in emergencies. Lu et al. (Lu et al., 2012)
proposed a framework to provide privacy on mo-
bile health monitoring devices. This approach uses
mathematical models on monitored information to
detect emergency situations and to release informa-
tion to qualified helpers. Other mathematical models
to express emergency situations were also proposed
by many researchers (Jeong et al., 2014)(Lee et al.,
2013)(Yu et al., 2017).
2.2 Dynamic Security Policy
Privacy is the major security concern related to com-
mercial IoT devices. Recent research shows that cur-
rent IoT devices focus on having secure connections
between devices and the server (Alharbi and Aspinall,
2018)(Janes et al., 2020)(Ren et al., 2019). However,
they lack a good access control policy to protect sen-
sitive information. The information can be exposed to
the third-party that operates the service such as Ama-
zon Web Services (AWS) (Ren et al., 2019). End
users, such as smart home users, are often left with
little or no control over device security. Moreover,
security policies may be dependent on the context.
Semantics-based approaches can be used to express
the context and situations, and adjust the security pol-
icy accordingly.
Carmiati at al. (Carminati et al., 2015) propose
an approach to provide privacy while working around
the current static model, such as using statistic mod-
els to detect anomalies in data and granting access to
all data if they are requested during the presence of an
anomaly. Semantics-based security policies can pro-
vide needed dynamic capabilities to protect privacy
without hindering emergency management. An ar-
chitecture that incorporates semantics-based security
policy into a stream data model has the potential to
provide a dynamic security policy that provides func-
tionalities in emergencies without sacrificing privacy.
2.3 Vulnerabilities of Stream Access
Control Enforcement via Syntactic
Policy Enforcement
Nehme et al. (Nehme et al., 2013)(Nehme et al., 2008)
proposed a security policy for stream data called se-
curity punctuation (sp). The security punctuations
are inserted by the source of the stream to indicate
the protection needs of the stream data. A security
punctuation contains the following: punctuation type
(pt), data description part (ddp), security restriction
part(srp), sign, timestamp (ts), and enforcement (et).
The security punctuation technique focuses on pro-
viding privacy control for the data source side. The
current security policy is sent from the data source
and specifies the security labels of attributes in the
data tuple. This approach allows the data source side
to decide the security needs which are suitable for pri-
vacy sensitive data domains, such as medical informa-
tion.
Example 1: Security Punctuation Policy Examples.
1 . D at a S e c u r i t y P u n c t u a t i o n
< dsp|S
1
|R
1
|+|1 : 00 : 00PM|I >
Only q u e r i e s r e g i s t e r e d by r o l e R
1
can q u e r y
t h e s t r e a m S
1
.
< dsp|A
1
, A
2
|R
2
|+|1 : 00 : 00PM|D >
Only q u e r i e s r e g i s t e r e d by r o l e R
2
can q u e r y
t h e a t t r i b u t e s A
1
an d A
2
a f t e r 1PM.
2 . Qu ery S e c u r i t y P u n c t u a t i o n
< qsp|null|R
3
|+|1 : 00 : 00PM|I >
Qu ery a c q u i r e s a r o l e R
3
.
< qsp|S
2
|R
4
|+|1 : 00 : 00PM|D >
Qu ery a c q u i r e s a r o l e R
4
a f t e r 1PM a nd t h e r o l e
R
4
i s p e r m i t t e d t o o n l y a c c e s s s t r e a m S
2
.
The security punctuation is subject to attacks that
can destroy or delay the sp. This is a common vul-
nerability of syntax-based security policies. Mali-
cious attackers can potentially disclose unauthorized
data by changing the position of the target tuple or
attribute, thus making the system interpret the secu-
rity level incorrectly. For example, due to the na-
ture of DSMS, the data can be accessed without au-
thorization if the security policy is not updated with
the correct time. The new sp can apply to only tu-
ples which are still in the sliding window and tuples
which arrive after sp. However, it cannot apply to tu-
ples which are finished querying and not in the sliding
window anymore. In the case that sp is destroyed dur-
ing transmission, the policy will not be updated. This
gives opportunities for attackers to access the unau-
thorized data with the outdated policy. In the case
that sp is delayed during transmission, attackers can
access the unauthorized data with the outdated policy
until sp arrives. Moreover, if the data items are shuf-
fled, the security punctuation that refers to the data
Stream Data Access Control Model: The Need for Data Semantics
21
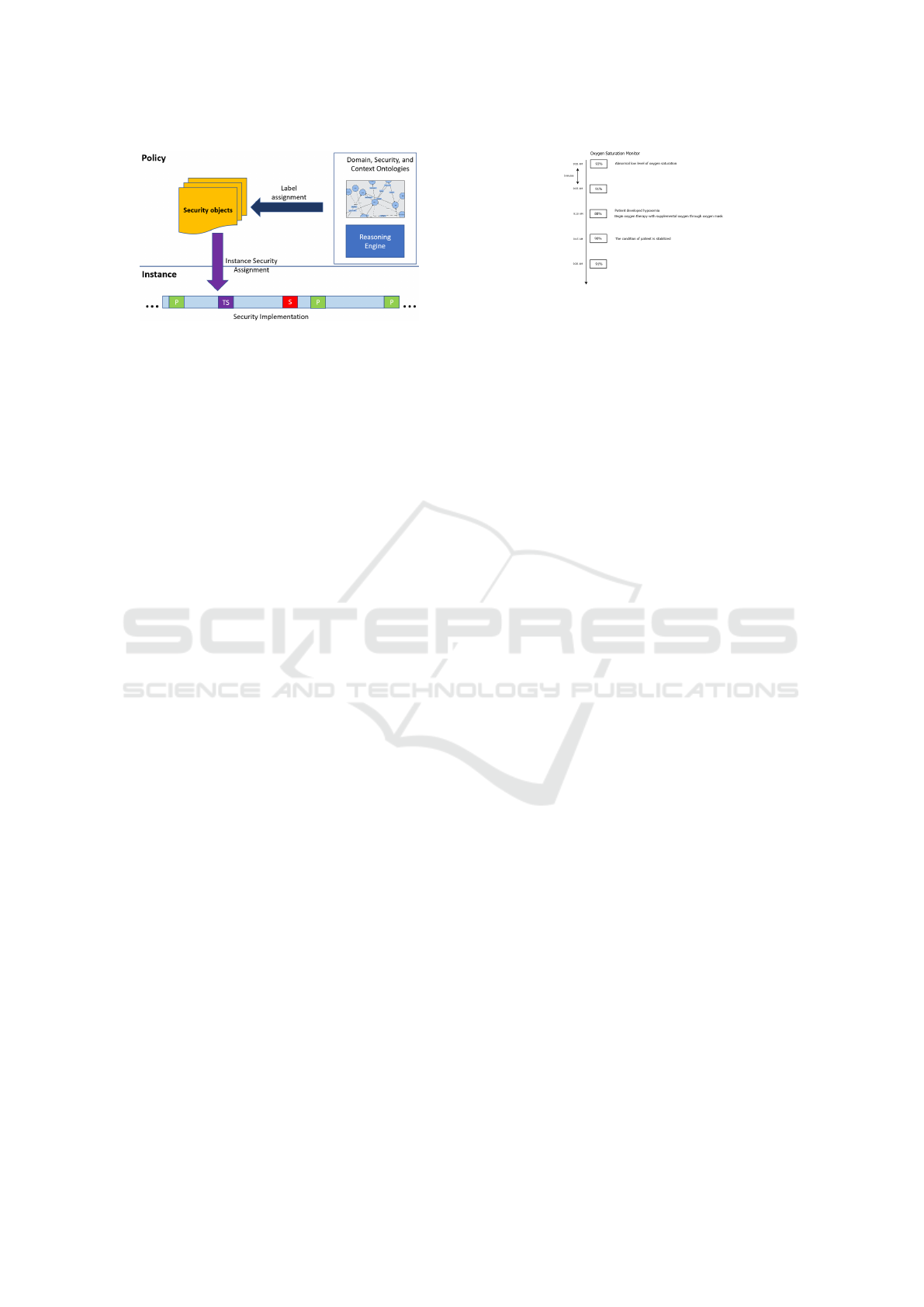
Figure 1: Architecture.
position in the tuple, may indicate the incorrect secu-
rity requirements. Our work, that describes security
for stream tuples based on data semantics, is indepen-
dent of the actual stream syntax and can avoid these
attacks. Moreover, our approach can be used with the
security punctuation-based implementation to verify
that the security has not been compromised.
3 ACCESS CONTROL
ARCHITECTURE AND
MOTIVATING EXAMPLE
The main focus of this work is to represent syntax-
independent access control requirement for stream
data. In this section, we present the system architec-
ture for our stream data access control and a motivat-
ing example demonstrating the need for a semantics-
based security model.
3.1 Architecture
We propose the use of ontologies to model domain
and context semantics. Security requirements are ex-
pressed over the ontologies and dynamically updated
according to context changes. Figure 1 shows the
overview of our system architecture. The policy part
of architecture contains domain and context ontolo-
gies, the reasoning engine, and the list of security ob-
jects. The policies will be applied on data instances of
the stream. The reasoning engine will derive security
labels from ontologies and assign them to security ob-
jects. The instances matching the security object de-
scriptions will be assigned by security labels of those
security objects.
3.2 Motivating Example
In this section, we present motivating examples to
demonstrate the shortcomings of current stream data
authorization models.
Figure 2: Oxygen saturation monitoring results on a patient
in an emergency ward.
In stream data, only a part of the data can be pro-
cessed at any given time via continuous queries. The
data will be processed with the same queries over
and over again. A different order of the same stream
tuples may result in different computational results.
Similarly, missing tuples will impact the results of
the continuous queries. Incorrect ordering can be de-
tected in case the timestamps are correct. However,
malicious users may modify the timestamp to achieve
a desired evaluation schedule. Moreover, the com-
pleteness of the stream may be difficult to detect if
there is no predetermined schedule for the arrival of
the stream tuples. Next, we present a hypothetical
scenario that may occur in the presence of malicious
users.
Incorrect Oxygen Saturation Measurement.
Health monitoring sensors broadcast vital signs,
such as body temperature, pulse rate, respiration
rate, blood pressure, and pulse oximetry. These
vital signs are frequently observed by medical staffs
during hospital admission. The frequency can vary
depending on the condition of patients. For example,
pulse oximetry measures the oxygen saturation in the
blood. The normal value is between 95-100%. An
oxygen saturation value below 90% is referred to as
hypoxemia. Patients generally show signs of mental
impairment at oxygen saturation below 85% and
completely lose consciousness at below 75%(Powell
et al., 1996). The presence of hypoxemia is generally
caused by underlying conditions of the heart or lungs,
which may require emergency care. The lack of
oxygen from hypoxemia can lead to a wide range of
complications from minor headaches to respiratory
failure, which can lead to death or permanent brain
damage in a matter of minutes without an immediate
response. The oxygen saturation level is generally
observed every 4 hours in admitted patient care but
constantly observed in critically ill patient cases.
Figure 2 shows an example of oxygen saturation
monitoring results. In this example, as soon as hy-
poxemia was detected, treatment was initiated. The
timely treatment prevented long-term complications
for the patient.
KMIS 2022 - 14th International Conference on Knowledge Management and Information Systems
22

Figure 3: Incorrect order of monitoring results.
Figure 3 shows an example of the same situation
as Figure 2 with an incorrect ordering. The medical
staff missed the early low oxygen saturation sign at
9:10 AM and didn’t initiate the emergency procedure.
To avoid penalty, they switched the timestamp of the
measurements, claiming that the readings were incon-
clusive. The patient did not receive appropriate treat-
ment in time which lead to long-term complications.
4 STREAM DATA MODEL
In addition to traditional data security requirements,
stream data requires security capabilities to provide
semantics-based dynamic security policy. Incomplete
data and incorrect order may affect the integrity and
security of the stream data. They also cannot be ad-
dressed with relational database security approaches.
A semantics-based dynamic security policy is needed
to provide fast and situation-responsive availability.
It can also counter attribute shuffle attacks which are
unique to the stream data model due to the lack of
metadata in tuples.
In this section, we present our framework to
address the above requirements.
Definition 1. Data Schema
A data schema D is a set of attribute names denoted by
D(A
1
, ..., A
n
), where D is the name of the data schema
and A
i
|i ∈ {1, ..., n} is an attribute name.
Definition 2. Data Instance on Data Schema D
A data instance d on data schema D(A
1
, ..., A
n
) is de-
noted as d =< a
1
, ..., a
n
>, where a
i
|i ∈ {1, ..., n} is
the value of attribute A
i
such that a
i
is in the domain
of attribute A
i
, i.e., a
i
∈ Dom(A
i
).
We also denote data instance d as d =< A
1
=
a
1
, ..., A
n
= a
n
> to explicitly identify the attribute val-
ues.
Definition 3. Stream Tuple
A stream tuple t from source l is denoted as t =
(l, d, ts), where ts is a timestamp representing the time
when t was generated.
Example 2: A stream tuple t
1
from source sensor
1
at
1:00AM
t
1
= ( sensor
1
, < A
1
= 10, A
2
= 20, A
1
= 30 > , 1 : 0 0 : 0 0AM)
The above stream tuple t
1
was generated by source
sensor
1
at 1:00:00AM. It contains a data instance
d =< A
1
= 10, A
2
= 20, A
1
= 30 > which specify the
value of attribute A
1
is 10, the value of attribute A
2
is
20, and the value of attribute A
3
is 30.
Definition 4. Data Stream
A data stream S from source l during a time period
from ts
j
to ts
k
is denoted as S
l
=< t
j
, ..., t
k
>, where
t
i
= (l
i
, d
i
,ts
i
) such that l
i
= l and < ts
j
, ..., ts
k
> is a
sequence of timestamps during a time period from ts
j
to ts
k
.
We also denote a data stream S from source
l during time interval from ts
j
to ts
k
as
S
l
[ts
j
,ts
k
] =< t
j
, ..., t
k
> or S
l
[ts
j
,ts
k
] =<
(l, d
j
,ts
j
), ..., (l, d
k
,ts
k
) >.
Definition 5. Stream Bundle
Let ts denotes a timestamp and l
1
, ..., l
n
denote stream
data sources. A stream bundle at the time ts, denoted
as
B
ts
= {(l
1
, d
1
,ts), ..., (l
n
, d
n
,ts)}, is the set of stream
tuples generated by the sources l
1
, ..., l
n
at time ts.
Note, at this point we do not address the issue of in-
compatible time stamps due to different levels of pre-
cision of the sources or due to the lack of synchroniza-
tion.
Definition 6. Atomic Protected Object Pattern
An atomic protected object pattern, also referred to
as an atomic protected object, is a triple consisting of
3 elements; a source description, a data description,
and a timestamp description. A protected object o is
denoted as
o = ((l, exp
l
), (d, exp
d
), (ts, exp
ts
))
where each element is as follows. Let v denotes a
variable, c denotes a constant, A
i
an attribute name
in d, and op denotes the operation = or <. Note,
we require that all attributes of the expressions are
bounded, i.e., they must appear in the corresponding
element l, d or ts.
1. A source description (l, exp
l
) where
(a) l is a data source c, such that c is a valid source,
or v;
(b) exp
l
is a Boolean expression of the form
Component
1
AND ... AND Component
n
, where
Component
i
(i = 1, . . . , n) is T RUE or (v op c).
We also denote a source description (v, T RUE),
representing any source, as (∗).
Stream Data Access Control Model: The Need for Data Semantics
23

Figure 4: Examples of different kinds of protected objects;
1. Atomic Protected Object:A tuple, 2. Stream Bundle:
Tuples from multiple sources which arrive at the same time
period, 3. Data Stream: Multiple tuples which continuous
arrive from a single source
2. A data description (d, exp
d
) where
(a) d is a data instance on data schema D, denoted
as d =< A
1
= k
1
, ..., A
n
= k
n
>, where k
i
(i =
1, . . . , n) is c, such that c ∈ Dom(A
i
) or v;
(b) exp
d
is a Boolean expression of the form
Component
1
AND ... AND Component
n
, where
Component
i
(i = 1, . . . , n) is T RUE, (v
i
op c),
(v
i
op v
j
), (A
i
op c), (A
i
op v
i
), or (A
i
op A
j
).
We also denote a data description (< A
1
=
v
1
, ..., A
n
= v
n
>, T RUE), representing any data
instance on data schema D, as (∗).
3. A timestamp description (ts, exp
ts
) where
(a) ts is a timestamp, such that ts is c or v;
(b) exp
ts
is a Boolean expression of the form
Component
1
AND ... AND Component
n
, where
Component
i
is T RUE or (v op c).
We also denote a timestamp description
(v, T RUE), representing any timestamp, as
(∗).
Definition 7. Simple Object Valuation
Let ν be a symbol mapping, such that;
1. ν maps a constant c to itself, i.e., ν : c −→ c.
2. ν preserves equality of variables, i.e., ν : v −→ c
1
and ν : v −→ c
2
then c
1
= c
2
.
3. ν maps special symbols to themselves, i.e.,
ν :=−→=, ν :<−→<.
4. ν maps an expression ν(x op y) = ν(x) op ν(y),
where x, y are any of the symbols above.
Definition 8. Stream Pattern Mapping
Let o = ((l, exp
l
), (d =< A
1
= k
1
, ..., A
n
= k
n
>
, exp
d
),
(ts, exp
ts
)) be an atomic protection object, and ν a
symbol mapping. A stream pattern mapping N is de-
fined as;
1. N(l, exp
l
) is defined as
N(l, exp
l
) = (ν(l), ν(exp
l
)).
2. N(< A
1
= k
1
, ..., A
n
= k
n
>, exp
d
) is defined as
N(< A
1
= k
1
, ..., A
n
= k
n
>, exp
d
)) = (< ν(A
1
) =
ν(k
1
), ..., ν(A
n
) = ν(k
n
) >, ν(exp
d
))
and N(A
i
) = N(k
i
) = ν(k
i
).
3. N(ts, exp
ts
) is defined as
N(ts, exp
ts
) = (ν(ts), ν(exp
ts
)).
Definition 9. Stream Pattern Mapping Satisfiability
Let o be an atomic protected object. We say that the
stream tuple t satisfies o iff there is a pattern mapping
N from o to t denoted as N(o) = t, such that N(exp
l
)
= T RUE, N(exp
d
) = TRUE, and N(exp
ts
) = TRUE.
Note, from now on, we only consider satisfied map-
ping when we use the phrase “pattern mapping”.
Example 3: Protected Object Mapping.
Giv en p r o t e c t e d o b j e c t o
1
an d t u p l e s t
1
, t
2
o
1
= ( ( sensor
1
,TRUE ) , ( < A
1
= v
1
, A
2
= 20 > ,v
1
< 20
AND 10 < v
1
) , ( v
2
,TRUE ) )
t
1
= ( sensor
1
, < A
1
= 15, A
2
= 20 > , 2 : 0 0 : 0 0AM)
t
2
= ( sensor
1
, < A
1
= 10, A
2
= 20 > , 2 : 0 5 : 0 0AM)
Mapping o
1
t o t u p l e t
1
1 . The v a l u a t i o n fro m s o u r c e d e s c r i p t i o n (l, exp
l
)
t o s o u r c e l
k
ν(sensor
1
) = sensor
1
ν(exp
l
) = TRUE
C o n d i t i o n s i n 1 . a r e s a t i s f i e d .
2 . The v a l u a t i o n fro m d a t a d e s c r i p t i o n (d, exp
d
) t o
d a t a i n s t a n c e d
k
ν(v
1
) = 15
ν(20) = 20
ν(exp
d
) = ν(v
1
)<20 AND 10<ν(v
1
) → 15<20 AND 10<15
ν(exp
d
) = TRUE
C o n d i t i o n s i n 2 . a r e s a t i s f i e d .
3 . The v a l u a t i o n fro m t u p l e d e s c r i p t i o n
(ts, exp
ts
) t o t i m e s t a m p ts
k
ν(v
2
) = 2 : 0 0 : 0 0AM
ν(exp
ts
) = TRUE
C o n d i t i o n s i n 3 . a r e s a t i s f i e d .
A l l v a l u a t i o n s a r e s a t i s f i e d . t
1
i s a member o f o
1
.
Mapping o
1
t o t u p l e t
2
1 . The v a l u a t i o n fro m s o u r c e d e s c r i p t i o n (l, exp
l
)
t o s o u r c e l
k
ν(sensor
1
) = sensor
1
ν(exp
l
) = TRUE
C o n d i t i o n s i n 1 . a r e s a t i s f i e d .
2 . The v a l u a t i o n fro m d a t a d e s c r i p t i o n (d, exp
d
) t o
d a t a i n s t a n c e d
k
ν(v
1
) = 10
ν(20) = 20
ν(exp
d
) = ν(v
1
)<20 AND 10<ν(v
1
) → 10<20 AND 10<10
ν(exp
d
) = FALSE
C o n d i t i o n i n 2 . i s n o t s a t i s f i e d .
3 . The v a l u a t i o n fro m t u p l e d e s c r i p t i o n
(ts, exp
ts
) t o t i m e s t a m p ts
k
ν(v
2
) = 2 : 0 5 : 0 0AM
ν(exp
ts
) = TRUE
C o n d i t i o n s i n 3 . a r e s a t i s f i e d .
V a l u a t i o n 2 . i s n o t s a t i s f i e d . t
2
i s n o t a member o f o
1
.
Definition 10. Object Dominance
Let o
1
and o
2
protected objects. We say that o
1
dom-
inates o
2
if for every tuple t, there is a valuation
ν(o
2
) = t, there must be a valuation ν(o
1
) such that
ν(o
1
) = t. We denote o
1
dominates o
2
as o
1
⊇
d
o
2
.
Object dominance is reflective, transitive, and asym-
metric, i.e., if o
1
⊇
d
o
2
and o
2
⊇
d
o
3
then o
1
⊇
d
o
3
.
5 SECURITY MODEL
We assign the default security labels for each entity
on ontologies. Those default security labels represent
KMIS 2022 - 14th International Conference on Knowledge Management and Information Systems
24

Figure 5: Ontology with Security Labels.
Figure 6: Stream Ontology.
security labels in the normal situation. We use a con-
text reasoner to decide what is the current situation
and assign an appropriate security label according to
that situation. In this section, we give a brief overview
of the ontologies and context reasoner.
5.1 Stream Data and Security Ontology
We expand the stream data ontology introduced by
Kolozali et al. (Kolozali et al., 2014), adding data se-
curity. Traditional access control models consider se-
curity to be a passive property of data quality. How-
ever, security is a complex entity associated with
many parts of the stream data, e.g., security capabili-
ties that devices can provide, security associated role
of users, and security property of data. We built an
ontology containing six main modules: Stream Data,
Device, Quality, User, Event, and Security.
Stream ontology is generalized so it can represent
the stream data environment. We extend the stream
ontology to represent the context of the stream data.
The transmitted data may have different meanings
in different contexts. We develop additional specific
context ontologies for the data domain of each indi-
vidual system. We further extend the stream ontology
with the context ontology.
We present an extensible context ontology for
modeling context in stream data environments. We
follow the context model from CONON (Wang et al.,
Figure 7: Context Ontology (Preuveneers et al., 2004) (Qin
et al., 2007) (Wang et al., 2004).
2004) and divide our context ontology into upper on-
tology and specific ontology. Our upper ontology
contains all basic contextual entities from CONON
with additional entities from CoDAMoS (Preuveneers
et al., 2004) and Smart Space (Qin et al., 2007). The
upper ontology describes 6 basic concepts: Com-
pEntity, Location, Person, Activity, Environment, and
Time. The specific ontology represents the details of
general concepts in each sub-domain.
5.2 Context Reasoning
To illustrate the logical reasoning mechanism, we
present a scenario in which the data generated from
sensors can have different levels of security poli-
cies depending on the current situation. For exam-
ple, when people are sleeping, their oxygen satura-
tion levels will naturally decrease because their body
needs less oxygen. Their bodies will reduce the res-
piration rate and heart rate during sleep. While the
oxygen saturation will also decrease during exercise,
this happens due to the body consuming more oxy-
gen. Despite having low oxygen saturation, the res-
piration rate and heart rate will increase during exer-
cise. An oxygen saturation value during rest that is
below 90% is considered a medical condition called
hypoxemia. However, an oxygen saturation value of
88% can be considered normal during intense exer-
cise. In this case, the oxygen saturation alone cannot
determine the condition of hypoxemia; the respiration
rate and heart rate must also be considered. We want
to provide a dynamic security policy to protect pa-
tient A’s privacy by limiting access during normal sit-
uations but allowing access during emergencies. By
using the context and ontology rules, we can derive
that the current oxygen saturation is normal or is indi-
cating an emergency situation. The security label as-
signments can be defined as λ(o
1
) = TopSecret and
λ(o
2
) = Public where o
1
is an oxygen saturation dur-
ing a normal situation and o
2
is an oxygen saturation
during an emergency situation. The protected objects
Stream Data Access Control Model: The Need for Data Semantics
25

can be separated into 2 cases; rest and exercise and be
defined as the following example;
Example 4: Protected Objects in Different Situations.
A p r o t e c t e d o b j e c t o
1a
r e p r e s e n t i n g a nor m a l
s i t u a t i o n d u r i n g r e s t i n g
o
1a
= ( ( s o u r c e = patient
A
,TRUE) , ( < oxygenSaturation = v
1
,
respirationRate = v
2
, heartRate = v
3
> , 90 < v
1
) ,
*
)
A p r o t e c t e d o b j e c t o
1b
r e p r e s e n t i n g a nor m a l
s i t u a t i o n d u r i n g e x e r c i s i n g
o
1b
= ( ( s o u r c e = patient
A
,TRUE) , ( < oxygenSaturation = v
1
,
respirationRate = v
2
, heartRate = v
3
> , 88 < v
1
AND 40 < v
2
AND
150 < v
3
) ,
*
)
A p r o t e c t e d o b j e c t o
2a
r e p r e s e n t i n g an e m e rgenc y
s i t u a t i o n d u r i n g r e s t i n g
o
2a
= ( ( s o u r c e = patient
A
,TRUE) , ( < oxygenSaturation = v
1
,
respirationRate = v
2
, heartRate = v
3
> , v
1
< 90 AND v
2
< 40 AND
v
3
< 150 ) ,
*
)
A p r o t e c t e d o b j e c t o
2b
r e p r e s e n t i n g an e m e rgenc y
s i t u a t i o n d u r i n g e x e r c i s i n g
o
2b
= ( ( s o u r c e = patient
A
,TRUE) , ( < oxygenSaturation = v
1
,
respirationRate = v
2
, heartRate = v
3
> , v
1
< 88 AND 40 < v
2
AND
150 < v
3
) ,
*
)
Definition 11. Ontology Mapping
Let O denote the ontology entity, and o =
((l, exp
l
), (d, exp
d
), (ts, exp
ts
)) be an atomic protec-
tion object, and ν a symbol mapping. An ontology
mapping N is defined as;
1. If O is a CompEntity concept entity, N(O) = o =
((l, exp
l
), (d, TRU E), (ts, T RUE) where (l, exp
l
)
is the source corresponding to compEntity O
with its associated location concept, and both
(d, T RUE), (ts, T RU E) can be any given data de-
scription and timestamp description.
2. If O is either person, activity, or en-
vironment concept entity, N(O) =
o = ((l, T RUE), (d, exp
d
), (ts, T RUE) where
(d, exp
d
) is the attributes corresponding to either
person, activity, or environment concept asso-
ciated with O, and both (l, T RU E), (ts, T RUE)
can be any given source description and data
description.
3. If O is a time concept entity, N(O) =
o = ((l, T RUE), (d, T RUE), (ts, exp
ts
)) where
(ts, exp
ts
) is the timestamp corresponding to
time concept O, and both (l, T RU E), (d, T RU E)
can be any given source description and data
description.
4. If O is an ontology entity associated
with more than one concept, N(O) =
o = ((l, exp
l
), (d, exp
d
), (ts, exp
ts
)) where
(l, exp
l
), (d, exp
d
), (ts, exp
ts
) are the source,
attributes, and timestamp corresponding to
ontology entity O.
Definition 12. Protection Object Security Label As-
signment
Let O
Dom
denote the domain ontology, and Λ the
mapping of security labels to the concepts in O
Dom
.
We denote Λ(O
Dom
) the assignment of security la-
bels to all the concepts in the ontology, and λ(ct
i
)
to denote the security label of the concept ct
i
. We
require that λ(ct
i
) ≥ λ(ct
j
) if ct
i
is a descendent
of ct
j
). The set of Core Security Objects (CSO)
is the set of all object patterns corresponding to
the ontological concepts. That is, for CSO =
(ct
s
, T RU E), (ct
d
, T RU E), (ct
ts
, T RU E), Λ(CSO) =
LUB(λ(ct
s
), λ(ct
d
), λ(ct
ts
)).
Additional security restrictions due to context-
aware or temporal needs, may be expressed over
more specific protection objects. Let o
1
⊇
d
o
2
, then
Λ(o
1
) ≤ Λ(o
2
).
Note, that emergency scenarios may require mod-
ification of core security object classifications and, in
our current model, can only be handled by reassigning
labels to the ontological concepts.
Definition 13. Instance Label Assignment
Let t be a data stream tuple and N(o
1
), ..., N(o
k
)
be satisfiable pattern mapping from protected objects
o
1
, ..., o
k
to t, where
λ(o
1
), ..., λ(o
k
) are the security labels of o
i
|i ∈
{1, ..., k}. We say that the security label of t
is LUB(λ(o
i
))|i ∈ {1, ..., k} where LUB(λ(o
i
)) is
the lowest upper bound of the security labels
λ(o
1
), ..., λ(o
k
).
Algorithm 1: Assign security label to stream tuple.
Require: Stream tuple t, and security labels of all
protected objects λ(o
1
), ..., λ(o
n
)
Ensure: Label assignment to a stream tuple
1: Initialization
2: Find all pattern mappings N
1
, ..., N
k
from O (all
protected objects) that are satisfied by t
3: Let {o
i
, ..., o
k
} ∈ O be the protected objects that
can be mapped by N
1
, ..., N
k
to t
4: Let λ(t) = LUB(λ(o
i
), ..., λ(o
k
))
Example 5: Security Label Assignment to Stream Tu-
ple.
S e c u r i t y L a b e l s : T o p S e c r e t ( TS ) > S e c r e t ( S ) > P u b l i c ( P )
t
1
= ( ( sensor
1
, TRUE) , < A
1
= 20, A
2
= 20 > , 2 : 0 0 : 0 0AM)
CASE 1 :
o
1
= ( ( sensor
1
,TRUE ) , ( < A
1
= v
1
, A
2
= 20 > ,v
1
< 50 ) ,
( v
2
,TRUE ) )
o
2
= ( ( sensor
1
,TRUE ) , ( < A
1
= v
1
, A
2
= 20 > ,v
1
< 10 ) ,
( v
2
,TRUE ) )
λ(o
1
) = Secret
λ(o
2
) = To pSecret
A s s i g n s e c u r i t y l a b e l t o t
1
KMIS 2022 - 14th International Conference on Knowledge Management and Information Systems
26

t
1
i s mapped t o o
1
.
L a b e l o f t
1
= λ(o
1
) = S e c r e t .
CASE 2 :
o
1
= ( ( sensor
1
,TRUE ) , ( < A
1
= v
1
, A
2
= 20 > ,v
1
< 50 ) ,
( v
2
,TRUE ) )
o
2
= ( ( sensor
1
,TRUE ) , ( < A
1
= v
1
, A
2
= 20 > ,v
1
< 30 ) ,
( v
2
,TRUE ) )
λ(o
1
) = Secret
λ(o
2
) = To pSecret
A s s i g n s e c u r i t y l a b e l t o t
1
t
1
i s mapped t o b o t h o
1
an d o
2
.
LUB(λ(o
1
), λ(o
2
)) = λ(o
2
)
L a b e l o f t
1
= λ(o
2
) = Top S e c r e t .
Next, we propose the concept of a complex pro-
tected object. This allows to express protection needs
over aggregates of stream tuples, while allowing max-
imum availability of the individual tuples.
Definition 14. Complex Protected Object
Let o
1
, ..., o
n
be the atomic protected objects. We say
that data stream S =< o
1
, ..., o
n
> or stream bundle
B = {o
1
, ..., o
n
} is a complex protected object O
c
iff
λ(O
c
) = λ(S) > LUB(λ(o
i
))|i ∈ {1, ..., n} or λ(O
c
) =
λ(B) > LU B(λ(o
i
))|i ∈ {1, ..., n}.
O
c
is minimal, that is for any o
i
,
¯
O
c
= O
c
- o
i
then
λ(
¯
O
c
) ≯ LUB(λ(o
j
))| j ∈ ({1, ..., n}−{i}). And there
are no two objects o
i
and o
j
such that o
i
⊇
d
o
j
Theorem 1. Given a stream tuple t and security la-
bels of all protected objects λ(o
1
), ..., λ(o
n
). Algo-
rithm 1 correctly assigns a security label to a stream
tuple t such that the assigned label l is the LUB of all
labels of security objects that can be mapped to t.
Proof. By contradiction;
Let λ(o
k
) be a security label assigned to a stream tu-
ple t. Assume that λ(o
k
) does not satisfy the security
requirement of t.
Case 1: o
k
cannot be mapped to t
1. From algorithm 1, o
k
must be a protected object
that can be mapped to t.
2. So t must be a member of o
k
. This contradicts the
supposition that t is not a member of o
k
.
Case 2: Security label λ(o
k
) is lower than the security
requirement of t
1. There must exist a o
t
such that ν(o
t
) > ν(o
k
) and
there is a pattern mapping from o
t
to t, ν(o
t
) = t.
2. But the algorithm 1, λ(t) is assigned by
LUB(λ(o
i
), ..., λ(o
t
), ..., λ(o
j
)) where {o
i
, ..., o
j
}
be the protected objects that can be mapped to t.
3. So λ(o
k
) must be LU B(λ(o
i
), ..., λ(o
j
)) which is
the highest security labels of protected objects
mapped to t. This contradicts the supposition that
λ(o
k
) is lower than the security requirement of t
Case 3: Security label λ(o
k
) is higher than the secu-
rity requirements of t
1. From algorithm 1, λ(t) is assigned by
LUB(λ(o
i
), ..., λ(o
j
)) where {o
i
, ..., o
j
} be
the protected objects that can be mapped to t.
2. So λ(o
k
) must be LU B(λ(o
i
), ..., λ(o
j
)) which is
the highest security labels of protected objects
mapped to t. This contradicts the supposition that
λ(o
k
) is higher than the security requirement of t
6 IMPLEMENTATION
In our previous work (Rhujittawiwat et al., 2021),
we implemented our context-aware security policy
engine. We implemented our framework using
Prot
´
eg
´
e (Stanford, 2022) and Semantic Web Rule
Language (SWRL) on an open-source home automa-
tion called Home Assistant (Home Assistant, 2021).
Figure 8 shows a simplified ontology containing
StreamTuple and ProtectedObject and figure 9 shows
a protected object with simple elements describing the
source, data instance, timestamp, and security label.
SWRL allows us to write reasoning rules to assign se-
curity labels where protected object o = ((source =
l, exp
l
), (d, exp
d
), (timestamp = ts, exp
ts
)) with label
assignment λ(o) = Label in the form as following;
StreamTuple(?t)
∧ hasSource(?t, N(source = l, exp
l
))
∧ hasDataInstance(?t, N(d, exp
d
))
∧ hasTimestamp(?t, N(timestamp = ts, exp
ts
))
→ hasLabel(?t, Label)
(1)
Where N(source = l, exp
l
), N(d, exp
d
), and
N(timestamp = ts, exp
ts
) can be derived from;
(2)
ProtectedOb ject(? o)
∧ source(?o, ?source)
∧ dataInstance(?o, ?data)
∧ timestamp(? o, ?timestamp)
∧ StreamTuple(?t)
∧ hasSource(?t, ?source)
∧ hasDataInstance(?t, ?data)
∧ hasTimestamp(?t, ?timestamp)
We show the SWRL rule to assign a security label
in figure 10 and the result where the label is assigned
to a stream tuple in figure 11
We use XML to facilitate data exchange between
Home Assistant and Prot
´
eg
´
e. This approach makes
it possible to extend data sharing for future applica-
tions. Figure 12 outlines how the data is extracted
Stream Data Access Control Model: The Need for Data Semantics
27
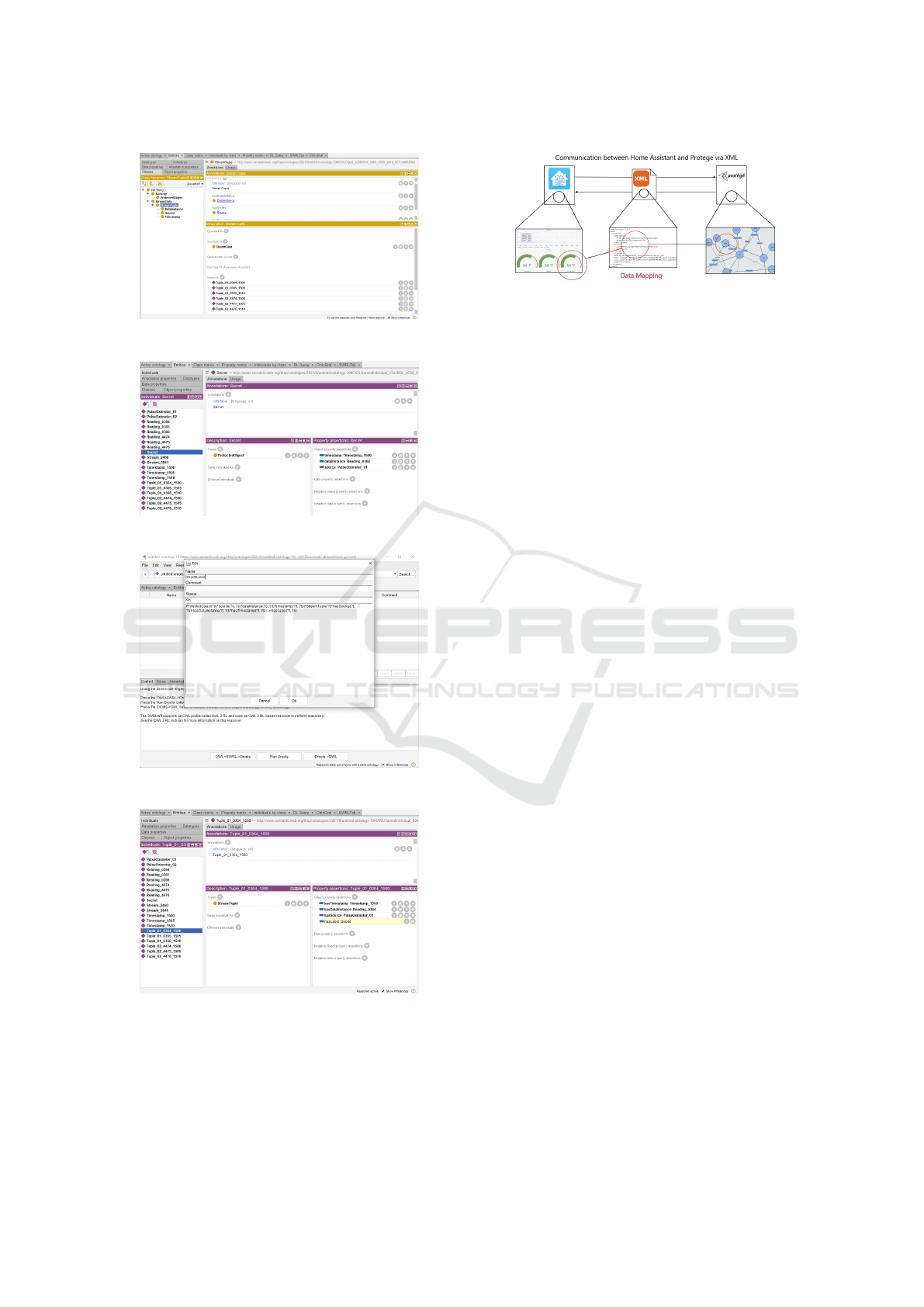
Figure 8: The Stream Ontology in the Prot
´
eg
´
e.
Figure 9: The Protected Object in the Prot
´
eg
´
e.
Figure 10: Label assignment with SWRL in the Prot
´
eg
´
e.
Figure 11: Reasoning result from label assignment.
from the Home Assistant database, converted to the
XML schema, and shared with Prot
´
eg
´
e. Similarly,
the decision reached by Prot
´
eg
´
e is converted to the
XML format, and incorporated into the Home Assis-
tant database.
Figure 12: Communication between Home Assistant and
Prot
´
eg
´
e via XML (Rhujittawiwat et al., 2021)
To get data from Prot
´
eg
´
e into Home Assistant,
we converted the CSV file that was exported from
Prot
´
eg
´
e. We created bash scripts to convert data from
each side to XML and convert XML to respective data
formats for each sides. Our ongoing work addresses
the security label enforcement using security punctu-
ation.
7 CONCLUSION
In this paper, we proposed a semantics-based access
control model for stream data. Our solution elimi-
nates the dependency on stream syntax and provides
1) syntax independent expression of security require-
ments, 2) high assurance of security compliance over
the IoT network, and 3) dynamic and adaptable se-
curity policy representation. We proposed the con-
cept of a stream data protection object that allows a
user-friendly and inter-operable expression of the pro-
tected data. We developed techniques so stream data
instances can inherit security requirements from the
protection object. In our model, we support strong
security by enforcing the most restrictive security re-
quirement that an instance inherits. We also cou-
pled our security model with context-based security.
The security restrictions of the protection objects may
change based on the current context. Our work pro-
vides an approach to support data security for the
rapidly evolving IoT environment. We applied tech-
nologies that are widely used for IoT applications to
support data integration and intelligent analysis, thus
our model is compliant with the technologies already
used by the industry.
REFERENCES
Alharbi, R. and Aspinall, D. (2018). An iot analysis frame-
work: An investigation of iot smart cameras’ vulnera-
bilities. In Living in the Internet of Things: Cyberse-
curity of the IoT - 2018. IET.
KMIS 2022 - 14th International Conference on Knowledge Management and Information Systems
28

Bermudez-Edo, M., Elsaleh, T., Barnaghi, P., and Taylor, K.
(2015). Iot-lite ontology.
Bermudez-Edo, M., Elsaleh, T., Barnaghi, P., and Taylor, K.
(2016). Iot-lite: a lightweight semantic model for the
internet of things. In 2016 INTL IEEE conferences
on ubiquitous intelligence & computing, advanced
and trusted computing, scalable computing and com-
munications, cloud and big data computing, internet
of people, and smart world congress (uic/atc/scal-
com/cbdcom/iop/smartworld), pages 90–97. IEEE.
Cao, J., Carminati, B., Ferrari, E., and Tan, K.-L. (2009).
Acstream: Enforcing access control over data streams.
In 2009 IEEE 25th International Conference on Data
Engineering, pages 1495–1498. IEEE.
Carminati, B., Ferrari, E., Cao, J., and Tan, K. L. (2010).
A framework to enforce access control over data
streams. ACM Transactions on Information and Sys-
tem Security (TISSEC), 13(3):1–31.
Carminati, B., Ferrari, E., and Guglielmi, M. (2015). De-
tection of unspecified emergencies for controlled in-
formation sharing. IEEE Transactions on Dependable
and Secure Computing, 13(6):630–643.
Carminati, B., Ferrari, E., and Tan, K. L. (2007a). Enforcing
access control over data streams. In Proceedings of
the 12th ACM symposium on Access control models
and technologies, pages 21–30.
Carminati, B., Ferrari, E., and Tan, K. L. (2007b). Specify-
ing access control policies on data streams. In Interna-
tional Conference on Database Systems for Advanced
Applications, pages 410–421. Springer.
Celdr
´
an, A. H., Clemente, F. J. G., P
´
erez, M. G., and
P
´
erez, G. M. (2014). Secoman: A semantic-aware
policy framework for developing privacy-preserving
and context-aware smart applications. IEEE Systems
Journal, 10(3):1111–1124.
Chen, H., Finin, T., and Joshi, A. (2003). An ontology
for context-aware pervasive computing environments.
The knowledge engineering review, 18(3):197–207.
Choi, C., Choi, J., and Kim, P. (2014). Ontology-based
access control model for security policy reasoning in
cloud computing. The Journal of Supercomputing,
67(3):711–722.
Guo, H., Li, Y., and Jajodia, S. (2007). Chaining wa-
termarks for detecting malicious modifications to
streaming data. Inf. Sci., 177(1):281–298.
Home Assistant (2021). Open source home automation.
http://www.home-assistant.io/.
Janes, B., Crawford, H., and OConnor, T. (2020). Never
ending story: Authentication and access control de-
sign flaws in shared iot devices. In 2020 IEEE Secu-
rity and Privacy Workshops (SPW), pages 104–109.
IEEE.
Jeong, Y.-S., Lee, S.-H., and Shin, S.-S. (2014). Access
control protocol based on privacy property of patient
in m-healthcare emergency. Wireless personal com-
munications, 79(4):2565–2578.
Kolozali, S., Bermudez-Edo, M., Puschmann, D., Ganz,
F., and Barnaghi, P. (2014). A knowledge-based ap-
proach for real-time iot data stream annotation and
processing. In 2014 IEEE International Conference
on Internet of Things (iThings), and IEEE Green Com-
puting and Communications (GreenCom) and IEEE
Cyber, Physical and Social Computing (CPSCom),
pages 215–222. IEEE.
Le-Phuoc, D., Dao-Tran, M., Parreira, J. X., and Hauswirth,
M. (2011). A native and adaptive approach for unified
processing of linked streams and linked data. In Inter-
national Semantic Web Conference, pages 370–388.
Springer.
Lee, C.-C., Hsu, C.-W., Lai, Y.-M., and Vasilakos, A.
(2013). An enhanced mobile-healthcare emergency
system based on extended chaotic maps. Journal of
medical systems, 37(5):9973.
Lu, R., Lin, X., and Shen, X. (2012). Spoc: A secure and
privacy-preserving opportunistic computing frame-
work for mobile-healthcare emergency. IEEE transac-
tions on parallel and distributed systems, 24(3):614–
624.
Manogaran, G., Thota, C., Lopez, D., and Sundarasekar, R.
(2017). Big data security intelligence for healthcare
industry 4.0. In Cybersecurity for Industry 4.0, pages
103–126. Springer.
Mengke, Y., Xiaoguang, Z., Jianqiu, Z., and Jianjian, X.
(2016). Challenges and solutions of information secu-
rity issues in the age of big data. China Communica-
tions, 13(3):193–202.
Montanari, R., Toninelli, A., and Bradshaw, J. M. (2005).
Context-based security management for multi-agent
systems. In IEEE 2nd Symposium on Multi-Agent Se-
curity and Survivability, 2005., pages 75–84. IEEE.
Nambiar, S., Kalambur, S., and Sitaram, D. (2020). Model-
ing access control on streaming data in apache storm.
Procedia Computer Science, 171:2734–2739.
Nehme, R. V., Lim, H.-S., and Bertino, E. (2013). Fence:
Continuous access control enforcement in dynamic
data stream environments. In Proceedings of the third
ACM conference on Data and application security and
privacy, pages 243–254.
Nehme, R. V., Rundensteiner, E. A., and Bertino, E. (2008).
A security punctuation framework for enforcing ac-
cess control on streaming data. In 2008 IEEE 24th
International Conference on Data Engineering, pages
406–415. IEEE.
Penrig, A., Song, D., and Tygar, D. (2000). Elk, a new
protocol for efficient large-group key distribution. In
Proceedings 2001 IEEE Symposium on Security and
Privacy. S&P 2001, pages 247–262. IEEE.
Powell, J., Menon, D., and Jones, J. (1996). The effects of
hypoxaemia and recommendations for postoperative
oxygen therapy. Anaesthesia, 51(8):769–772.
Preuveneers, D., Van den Bergh, J., Wagelaar, D., Georges,
A., Rigole, P., Clerckx, T., Berbers, Y., Coninx, K.,
Jonckers, V., and De Bosschere, K. (2004). Towards
an extensible context ontology for ambient intelli-
gence. In European Symposium on Ambient Intelli-
gence, pages 148–159. Springer.
Puthal, D., Nepal, S., Ranjan, R., and Chen, J. (2015). A
dynamic key length based approach for real-time se-
curity verification of big sensing data stream. In Inter-
Stream Data Access Control Model: The Need for Data Semantics
29

national conference on web information systems engi-
neering, pages 93–108. Springer.
Puthal, D., Wu, X., Nepal, S., Ranjan, R., and Chen, J.
(2017). Seen: A selective encryption method to en-
sure confidentiality for big sensing data streams. IEEE
Transactions on Big Data.
Qin, W., Shi, Y., and Suo, Y. (2007). Ontology-based
context-aware middleware for smart spaces. Tsinghua
Science and Technology, 12(6):707–713.
Ren, J., Dubois, D. J., Choffnes, D., Mandalari, A. M.,
Kolcun, R., and Haddadi, H. (2019). Information
exposure from consumer iot devices: A multidimen-
sional, network-informed measurement approach. In
Proceedings of the Internet Measurement Conference,
pages 267–279.
Rhujittawiwat, T., Anderson, C., Keen, D., Miles, C.,
Farkas, C., Smiles, S., Wells, N., Roginski, J., Freder-
ick, S., and Banik, S. (2021). Making smart platforms
smarter: adding third party applications to home au-
tomation platforms. Journal of Computing Sciences
in Colleges, 37(5):43–53.
Sabelfeld, A. and Myers, A. C. (2003). Language-based
information-flow security. IEEE Journal on selected
areas in communications, 21(1):5–19.
Sejdiu, B., Ismaili, F., and Ahmedi, L. (2021). Iotsas: an in-
tegrated system for real-time semantic annotation and
interpretation of iot sensor stream data. Computers,
10(10):127.
Shafagh, H., Burkhalter, L., Ratnasamy, S., and Hithnawi,
A. (2020). Droplet: Decentralized authorization and
access control for encrypted data streams. In 29th
USENIX Security Symposium (USENIX Security 20),
pages 2469–2486.
Stanford (2022). Prot
´
eg
´
e.
Thoma, C., Labrinidis, A., and Lee, A. J. (2019). Shoal:
Query optimization and operator placement for access
controlled stream processing systems. In IFIP An-
nual Conference on Data and Applications Security
and Privacy, pages 261–280. Springer.
Veltri, L., Cirani, S., Busanelli, S., and Ferrari, G. (2013).
A novel batch-based group key management protocol
applied to the internet of things. Ad Hoc Networks,
11(8):2724–2737.
Wang, X. H., Zhang, D. Q., Gu, T., and Pung, H. K. (2004).
Ontology based context modeling and reasoning using
owl. In IEEE annual conference on pervasive comput-
ing and communications workshops, 2004. Proceed-
ings of the second, pages 18–22. Ieee.
Whitehouse, K., Zhao, F., and Liu, J. (2006). Semantic
streams: A framework for composable semantic inter-
pretation of sensor data. In European Workshop on
Wireless Sensor Networks, pages 5–20. Springer.
Yu, W., Liu, Z., Chen, C., Yang, B., and Guan, X. (2017).
Privacy-preserving design for emergency response
scheduling system in medical social networks. Peer-
to-Peer Networking and Applications, 10(2):340–356.
Zhu, S., Setia, S., and Jajodia, S. (2006). Leap+ efficient
security mechanisms for large-scale distributed sen-
sor networks. ACM Transactions on Sensor Networks
(TOSN), 2(4):500–528.
KMIS 2022 - 14th International Conference on Knowledge Management and Information Systems
30
