
Digital Attendance Using Student Identification Cards with Fuzzy
Method at Khoirul Huda Islamic Boarding School 3
Mohamad Ridwan
a
, Fidia Astuti Hapsari
and Aries Pratiarso
Department of Electrical Engineering, Politeknik Elektronika Negeri Surabaya, Sukolilo, Surabaya, Indonesia
Keywords: Digital Attendance, Student Identification Cards, Web Based Programming, Fuzzy Method.
Abstract: The Khoirul Huda 3 Islamic Boarding School also conducts attendance recording every month as a student
discipline report, with manual recording it takes quite a long time. From this problem, the author offers a final
project in the form of "Digital Attendance Using Santri Identification Cards with the Fuzzy Method at the
Khoirul Huda Islamic Boarding School 3". The result of this research is an attendance system using a student
identification card equipped with a barcode, attendance can be done lightly and recorded in real time on the
website. To determine the punishment for students who violate the recitation, the fuzzy method is used to
determine the punishment in accordance with the criteria for student violations. To avoid cheating or leaving
an absence, before being absent using a student identification card, the student must identify the owner of the
card by attaching a fingerprint to the Finger Print first. From the tests carried out, it was found that the
percentage of successful barcode reading from a distance of 1 cm to 10 cm was 66.11% and the accuracy level
of the fuzzy method implemented in the system was 99%.
1 INTRODUCTION
The growing number of Muslims on this earth has
encouraged the growth of facilities and infrastructure
that are also needed for Muslims. Khoirul Huda
Student Islamic Boarding School is one of the Islamic
boarding schools intended for students who are
pursuing higher education in the city of Surabaya,
which is located in the Medokan Semampir village,
Sukolilo. This Islamic boarding school has a
recitation schedule in which three hours a day are
allocated for recitation activities. This three-hour time
is then divided into two times, namely at night and at
dawn where one hour is used to recite the Koran after
dawn (05.00 to 06.00) and two hours after the Isha
prayer (19.30 to 21.30) is used to recite the Koran at
night. This lodge focuses on the activities of studying
the interpretation of the Qur'an and Al-Hadith, where
the book of hadith studied is the book of Hadith. This
study includes interpretation and practice in everyday
life (Warsito, 2022).
Attendance is a list of attendance of
employees/students/teachers that contains the hours
of arrival and departure times as well as the reasons
a
https://orcid.org/0000-0003-3046-0115
or information for their attendance. Attendance data
retrieval is currently still done manually so it has
many shortcomings, such as invalid data due to errors
in the attendance data input process by the admin
manager and missing or damaged attendance forms
because the form must be brought and then stored
back (Maulani, Julian, Hakim, 2018). The Khoirul
Huda 3 Islamic Boarding School has an attendance
system as a parameter for monitoring student
discipline in attending recitations. However, the
attendance system at the Khoirul Huda 3 Islamic
Boarding School is still manual so it is still
experiencing problems as mentioned above.
From these problems, this project aims to create a
digital attendance system. In which the attendance
system can be done lightly by simply sticking the
student's identity card on the reader or barcode
scanner so that the results can be known quickly
because the output will be displayed directly on the
website. In addition, data will not be lost or scattered
because all data will be inputted into the database and
periodically upgraded as needed. To avoid cheating
or leaving an absence, before being absent using a
student identification card, the student must identify
the card owner by attaching a fingerprint to the Finger
Ridwan, M., Hapsari, F. and Pratiarso, A.
Digital Attendance Using Student Identification Cards with Fuzzy Method at Khoirul Huda Islamic Boarding School 3.
DOI: 10.5220/0011967200003575
In Proceedings of the 5th International Conference on Applied Science and Technology on Engineering Science (iCAST-ES 2022), pages 951-958
ISBN: 978-989-758-619-4; ISSN: 2975-8246
Copyright © 2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
951
Print first and then bringing the student identification
card closer to the Barcode Scanner.
2 RELATED WORK
Attendance using a barcode is one solution to the
problem of manual attendance. In the study, the
researcher made a presence presence where the output
of the system design was an automatic attendance
program based on an information system with a
barcode scanner for tutors at the Pesma KH Mas
Mansyur International Islamic Boarding School. This
attendance was developed with a waterfall model as
well as a MySQL Database in the PHP programming
language. The purpose of this digital presence is to
report to his superiors which will influence decision
making to improve pesma's academic section (Fahmi,
2018).
So that there is no mistake in filling in attendance
data, it is necessary to monitor attendance in real time
through the website. In the study, the researcher
created a Web-based attendance system using a
Barcode that can be used for every conference
activity. The development of attendance systems uses
the Spiral method which allows systematic and
iterative development of the system for each of its
features. The result of this study is an attendance
system that can be used to take absences in each
presentation session in a conference activity. The
system can also display attendance reports for each
presentation session and also the presentation
sessions that are most in demand (Rotikan, 2016).
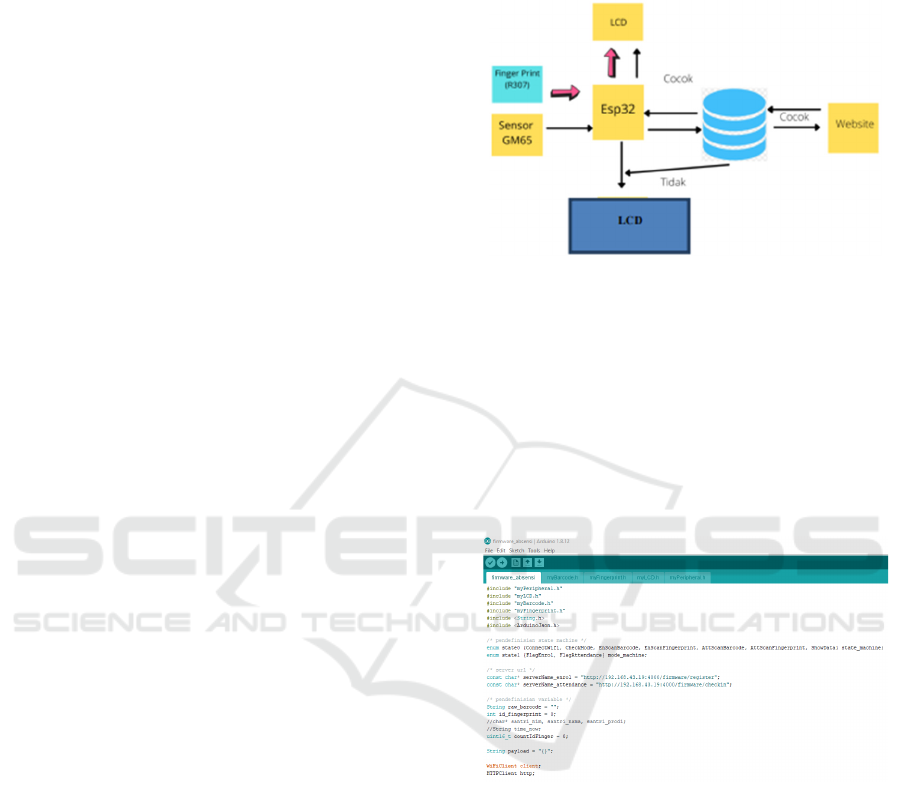
3 PROPOSED SYSTEM
An initial design of the system as a whole is required,
which will later be processed as an individual system
before finally being integrated after all processes have
been successfully carried out. In general, several steps
to achieve the desired results. These steps will be
applied starting from data retrieval to activity
classification. The following is a flow chart for the
system to be designed.
3.1 Hardware Design
First step in making a digital attendance system is
hardware design. In this hardware design, all the
components needed are designed in such a way that
the system can run properly. The components used
are Esp32, Fingerprint R307, GM65 Barcode
Scanner, Buzzer and Lcd. Everything is designed in
advance on the Kicad application before assembly is
carried out.
Figure 1: Design hardware.
3.2 Hardware Programming on
Arduino IDE
After designing the hardware, the next step is to
program the Arduino IDE. The program is made
according to the components used and the ports and
pins used. It is in programming that determines
whether these components can run according to the
desired system or not.
Figure 2: Programming on Arduino IDE.
3.3 Sensor Data Retrieval
Fingerprint Data Retrieval Fingerprints. Fingerprints
are the result of reproduction of fingerprints, whether
intentionally taken, stamped with ink, or marks left
on objects because they have been touched by the skin
of the palms of the hands or feet. Fingerprint is
biomedical authentication that differs from one
person to another, because one is different from
another, fingerprints are usually used as data security.
In this fingerprint data collection process, each
student attaches or leaves his/her fingerprint to the
Fingerprint sensor R307 in enrol mode which will
then be stored in the database.
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
952

Figure 3: Fingerprint data retrieval.
3.4 Barcode Data Retrieval
Barcode (Bar Code / Cross Code / Bar Code) is an
optical data techzeroogy that has a line or strip
machine readable. These different codes serve to
distinguish one product type from other products.
Included in the student identification card at the
Khoirul Huda Islamic Boarding School 3 also uses
barcode to store student ID number data. In the
barcode data collection process, each student must:
attach the student identification card to the GM65
Barcode Scanner. What later from the data
collection will be processed by the microcontroller
to perform attendance and also stored into the
database.
Figure 4: Data retrieval on barcode sensors.
3.5 Database Design
Database or database is a collection of data that is
managed in such a way based on certain conditions
interconnected so that it is easy to manage. Through
this management, users can obtain relief in seeking
information, storing information and disposing of
information. Including to manage fingerprint and
barcode data on this system, a database is used. That
is data that has been detected by the sensor is entered
into the database, it is useful if the sensor detects the
incoming data and matches the database stored, then
the process on the system can run and students can do
attendance. But if the data detected on the sensor does
not match the stored database, the process on the
system will not work.
Figure 5: Database design.
3.6 Website Creation
Website is a collection of pages in a domain that
contains various information so that it can be
accessed read and viewed by internet users through a
search engine. Information that can be contained in a
Websites generally contain image, illustration, video,
and text content for various purposes. The website on
this system is used as attendance monitoring that has
been carried out by sensors and microcontrollers, then
the data obtained is placed in the database and the
website can access the database by doing the
following: the connection between the database and
the API that has been created. In the web there are 2
sides, namely the user side and the admin side. On the
user side will only display some information such as
student data and attendance. While on the admin side
need to log in first, and also admins can add
information, edit and enter data required Website will
be fully controlled by the Attendance Team as admin.
Figure 6: User website design.
Digital Attendance Using Student Identification Cards with Fuzzy Method at Khoirul Huda Islamic Boarding School 3
953
3.7 Fuzzy Design
The design of fuzzy logic in research is used to
determine the punishment for students who commit
crimes violations in the form of neglecting recitation
and late recitation. The Fuzzy Inference System (FIS)
used is Fuzzy Sugeno. The stages of fuzzy design are:
3.7.1 Fuzzy Variable
In decision making, 2 input variables and 1 output
variable are made, namely the missed recitation and
late variables. And there is also an output in the form
of action_punishment.
3.7.2 Linguistic Values
After determining the 3 variables, in each variable its
linguistic value is determined, namely:
a. The alpha variable is divided into 4 inputs:
Light, Medium, Heavy, Very Heavy.
b. The late variable is divided into 4 inputs: Small,
Medium, Large, Very Large.
c. Action_punishment variable is divided into 4
inputs: Light, Medium, Heavy, Very Heavy.
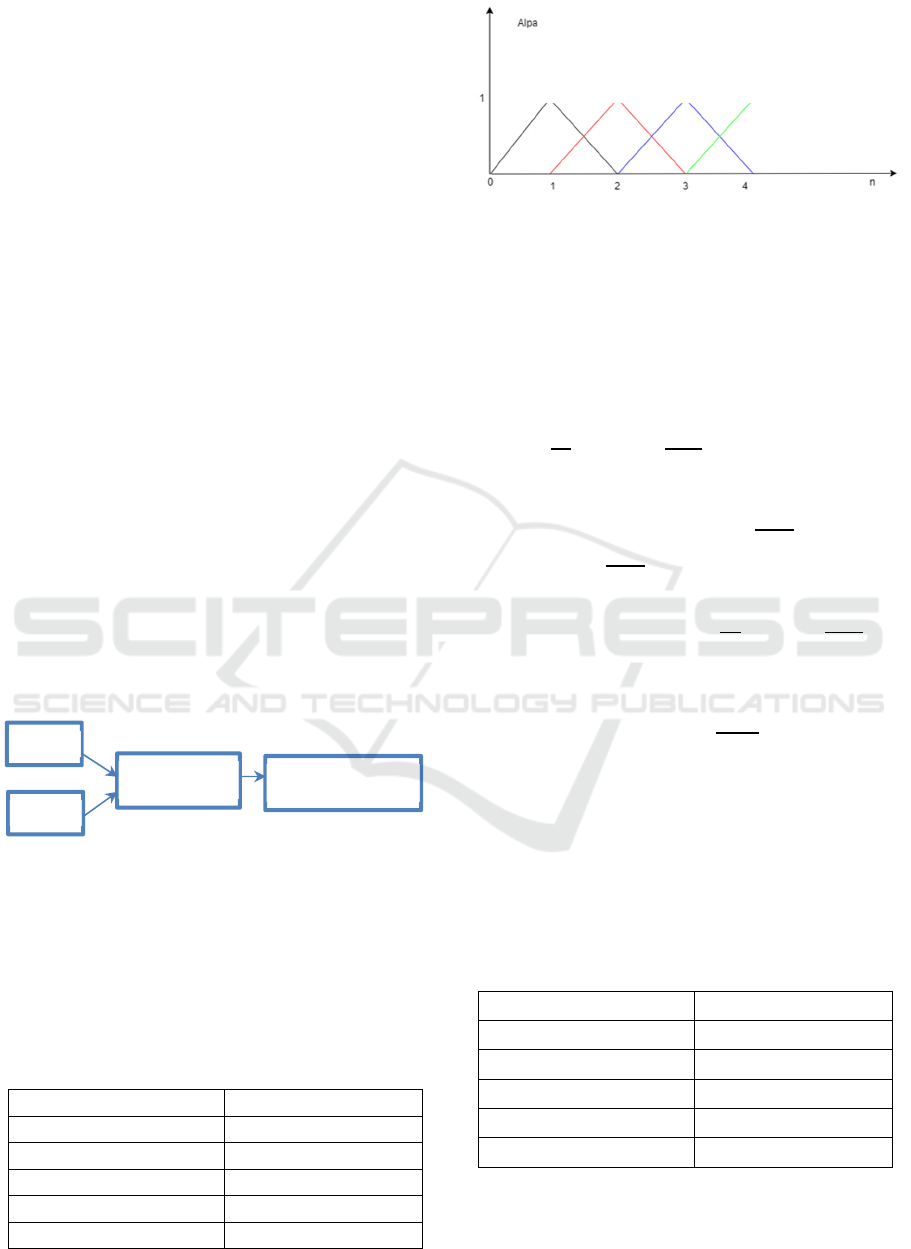
3.7.3 Fuzzyfication
Fuzzyfication is a mapping of crisp values into fuzzy
sets and determines the degree of membership in the
fuzzy set. In general, the mapping is as shown below:
Figure 7: Fuzzy design.
Based on the FIS above, the mapping is as follows:
a. The alpha variable has a range of values
between a minimum of 0 and a maximum of n.
The alpha variable is divided into five inputs,
namely zero, light, medium, heavy and Very
Heavy. each with a range of values as follows:
Table 1: Alpa variabel.
Linguistic values Range
Zero 0
Light 0-2
Medium 1-3
Heavy 2-4
Very Heavy
3-
Figure 8: Input graphic variabel alpa.
Calculation of the five variables obtained four
different functions, namely the three functions and
the trapezoid function. After this is the calculation of
the four functions, namely:
|
|
=1;=0 (1)
First Triangle Curve: Light
|
|
=0;1
1
0
10
;01
2
21
;1 2
(2)
Second Triangle Curve: Medium
|
|
= 0; 1 3
1
21
;1
2
;23
(3)
Third Triangle Curve: Heavy
|| = 0; 2 4
;23
;3
4
(4)
First Trapezoidal Curve: Very heavy
|
|
= 0; 3
3
43
;3 41;
4
(5)
The late variable has a range of values between a
minimum of 0 and a maximum of n. The alpha
variable is divided into five inputs, namely zero,
small, medium, large and very large. each with a
range of values as follows:
Table 2: Alpa Variable.
Nilai Linguistic Range
Zero 0
Little 0-6
Medium 3-9
Big 6-12
Very big 9-n
Alpa
Late
Fuzzy Logic
(FIS
f(u)
action punishme
Light Medium Heavy
Very Heavy
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
954

Figure 9: Input graphic variabel late.
Calculation of five variables obtained four different
functions, namely 3 triangular functions and one
trapezoidal function. After this is the calculation of
the four functions, namely:
|
|
=1;=0 (6)
First Triangle Curve : Little
|
|
=
0; 0 3
0
30
;0 3
6
63
;3 6
(7)
Second Triangle Curve: Medium
|
|
= 0; 3 9
3
63
;3
6
;69
(8)
Third Triangle Curve : Big
|| = 0; 6 12
;69
;9
12
(9)
First trapezoidal curve: Very big
|
|
=
0; 9
; 9 121; 12
(10)
b. Action_punishment variable is divided into 4
outputs, namely Light Punishment, Moderate
Punishment, Hard Punishment and Very Hard
Punishment. Fuzzy Rules or fuzzy rules set
amounted to 25 rules. The rule determines how
heavy the penalty is.
Table 3: Fuzzy rules.
No
Input Output
Alpa Late Action_Punishment
1 Zero Zero No Punishment
2 Zero Little Light Punishment
3 Zero Medium Light punishment
4 Zero Big Medium punishment
5 Zero Very big Heavy punishment
6 Light Zero Light punishment
7 Light Little Light punishment
8 Light Medium Light punishment
9 Light Big Medium punishment
10 Light Very big Punishment Medium
11 Medium Zero Light punishment
12 Medium Little Light punishment
13 Medium Medium Medium punishment
14 Medium Big Medium punishment
15 Medium Very big Medium punishment
16 Heavy Zero Medium punishment
17 Heavy Little Heavy punishment
18 Heavy Medium Heavy punishment
19 Heavy Big Heavy punishment
20 Heavy Very big Heavy punishment
21
Very
heavy
Zero Heavy punishment
22
Very
heavy
Little Heavy punishment
23
Very
heavy
Medium
Very heavy
punishment
24
Very
heavy
Big
Very heavy
punishment
25
Very
heavy
Very big
Very heavy
punishment
c. Implications and Defuzzification. The Fuzzy
Sugeno method uses the minimum implication
function (MIN). For defuzzification using the
weight average method.
∗=
∑
∑
(11)
To make it easier to read the value of the punishment
according to the weight of the violations committed
by the students, it can be seen in the table below.
Table 4: Range violation.
Linguistic Value Range
No Punishment
01
Light Punishment
12
Medium Punishment
23
Heavy Punishment
34
Very Heavy Punishment
4
4 RESULT AND ANALYSIS
After the digital attendance system is realized, it is
necessary to carry out various tests to find out how
the device works and analyze the level of reliability,
Little Medium
Late
Big
Very Big
Digital Attendance Using Student Identification Cards with Fuzzy Method at Khoirul Huda Islamic Boarding School 3
955
weaknesses and limitations of the functional
specifications of the system that has been created. In
addition, this test is also carried out to find out about
how to condition the system so that it can be used
optimally.
4.1 Reader Testing on Digital
Attendance Systems
4.1.1 Testing the Time Lag Required in
Reading Barcode Scanner Tags
Table 5: Testing the time lag required in reading barcode
scanner tags.
Sample
1
second
2
second
3
second
4
second
5
second
card
Card 1
Card 2
Card 3
Card 4
Card 5
Card 6
Card 7
Card 8
Card 9
Card 10
Card 11
Card 12
Card 13
Card 14
Card 15
Card 16
Card 17
Card 18
Card 19
Card 20
Card 21
Card 22
From the tests that have been carried out, it is
found that, the lag time required for reading Barcode
Scanner tag is a time range of 1 second to 3 seconds.
As for cards 19 to 22 can't be read because the
barcode on the card doesn't have a good print or can
be said to be damaged, so Barcode Scanner cannot
read.
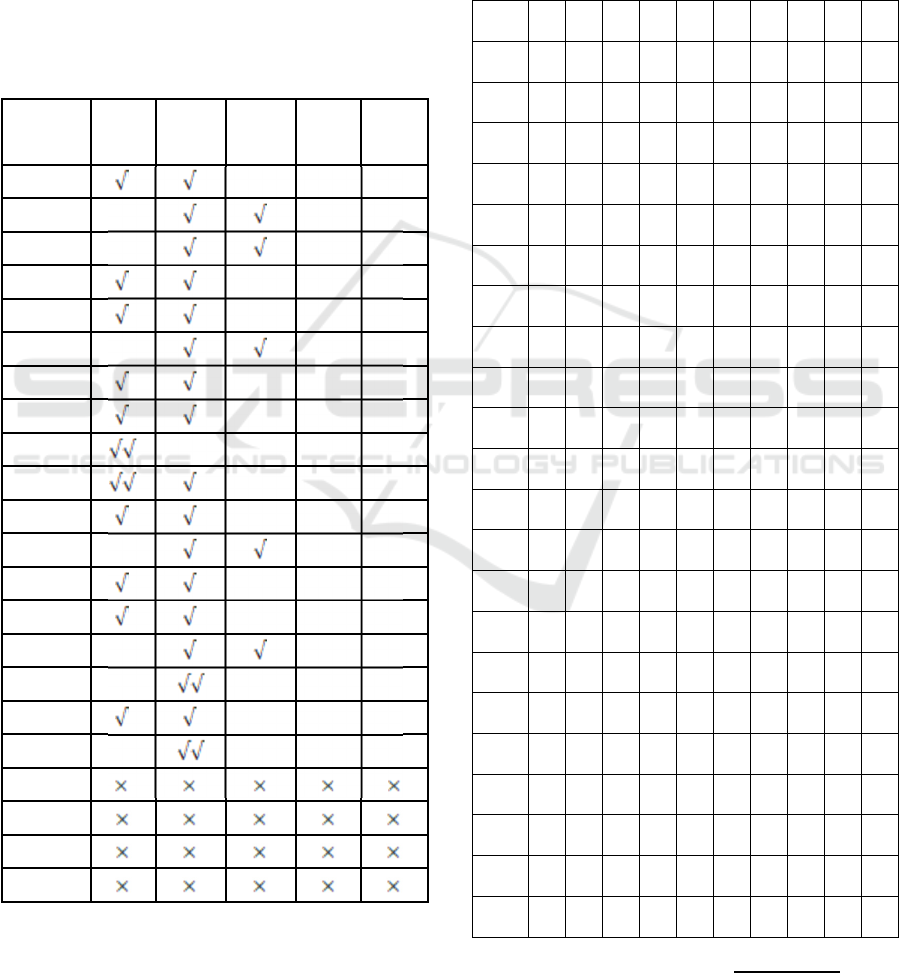
4.1.2 Testing the Distance Required by the
Barcode Scanner Sensor in Reading
the Barcode on the Card Student Sign
Table 6: Barcode scanner sensor distance test in barcode
reading.
Sample
Card
1
cm
2
cm
3
cm
4
cm
5
cm
6
cm
7
cm
8
cm
9
cm
10
cm
card 1
✔
✔
✔
✔
✔
✔
✔
card 2
✔
✔
✔
✔
✔
✔
✔
card 3
✔
✔
✔
✔
✔
✔
✔
card 4
✔
✔
✔
✔
✔
✔
card 5
✔
✔
✔
✔
✔
✔
✔
card 6
✔
✔
✔
✔
✔
✔
✔
card 7
✔
✔
✔
✔
✔
✔
✔
card 8
✔
✔
✔
✔
✔
✔
✔
card 9
✔
✔
✔
✔
✔
✔
card 10
✔
✔
✔
✔
✔
✔
✔
card 11
✔
✔
✔
✔
✔
✔
✔
card 12
✔
✔
✔
✔
✔
✔
card 13
✔
✔
✔
✔
✔
✔
✔
card 14
✔
✔
✔
✔
✔
✔
✔
card 15
✔
✔
✔
✔
✔
✔
card 16
✔
✔
✔
✔
✔
✔
card 17
✔
✔
✔
✔
✔
✔
card 18
✔
✔
✔
✔
✔
✔
card 19
card 20
card 21
card 22
=
(12)
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
956
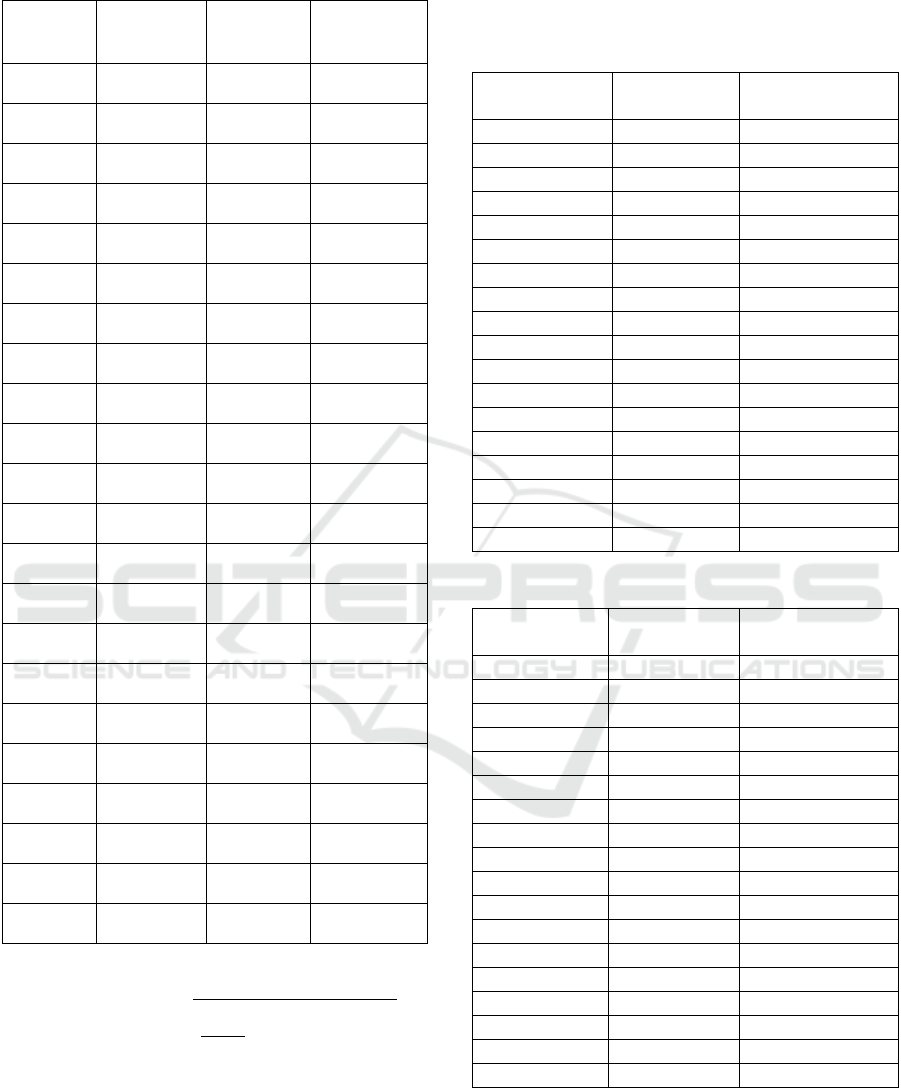
Table 7: Success percentage.
Sample
Card
Many
Successes
Number
Of Trials
Success
Percentage
card 1 7 10 70%
card 2 7 10 70%
card 3 7 10 70%
card 4 6 10 60%
card 5 7 10 70%
card 6 7 10 70%
card 7 7 10 70%
card 8 7 10 70%
card 9 6 10 60%
card 10 7 10 70%
card 11 7 10 70%
card 12 6 10 60%
card 13 7 10 70%
card 14 7 10 70%
card 15 6 10 60%
card 16 6 10 60%
card 17 6 10 60%
card 18 6 10 60%
card 19 0 10 0%
card 20 0 10 0%
card 21 0 10 0%
card 22 0 10 0%
=
=
%
= 66,11% (13)
From the tests carried out, it was found that the
distance between the student identification card and
the Barcode Scanner that could be detected was from
a distance of 3cm to 10 cm. And the average success
of all trials is 66.11%.
4.1.3 Fingerprint Best Condition Test for
Fingerprint Sensor Reading
Table 8: Condition fingerprint dry.
Sample
Fingerprint
Condition
Fingerprint
Time Required
Id 1 Dry Detected
Id 2 Dry Detected
Id 3 Dry Detected
Id 4 Dry Detected
Id 5 Dry Detected
Id 6 Dry Detected
Id 7 Dry Detected
Id 8 Dry Detected
Id 9 Dry Detected
Id 10 Dry Detected
Id 11 Dry Detected
Id 12 Dry Detected
Id 13 Dry Detected
Id 14 Dry Detected
Id 15 Dry Detected
Id 16 Dry Detected
Id 17 Dry Detected
Id 18 Dry Detected
Table 9: Condition fingerprint wet.
Sample
Fingerprint
Condition
Fingerprint
Time Required
Id 1 Wet Not detected
Id 2 Wet Not detected
Id 3 Wet Not detected
Id 4 Wet Not detected
Id 5 Wet Not detected
Id 6 Wet Not detected
Id 7 Wet Not detected
Id 8 Wet Not detected
Id 9 Wet Not detected
Id 10 Wet Not detected
Id 11 Wet Not detected
Id 12 Wet Not detected
Id 13 Wet Not detected
Id 14 Wet Not detected
Id 15 Wet Not detected
Id 16 Wet Not detected
Id 17 Wet Not detected
Id 18 Wet Not detected
From the fingerprint condition testing carried out,
it can be seen that the Fingerprint Sensor only can
only detect fingers or perform fingerprint readings,
when the finger is dry. Whereas when the finger is
Digital Attendance Using Student Identification Cards with Fuzzy Method at Khoirul Huda Islamic Boarding School 3
957

wet the Fingerprint Sensor can't read the fingerprint
either registered or unregistered.
4.1.4 Testing the Time Required in Reading
the Fingerprint Sensor Tag
Table 10: Testing the time required in reading the
fingerprint sensor tag.
Sample
Fingerprint
1
second
2
second
3
second
4
second
5
second
Id 1
Id 2
Id 3
Id 4
Id 5
Id 6
Id 7
Id 8
Id 9
Id 10
Id 11
Id 12
Id 13
Id 14
Id 15
Id 16
Id 17
Id 18
From testing the time lag for reading the Fingerprint
Sensor tag, it was found that the length of time
Fingerprint Sensor to be able to detect fingerprints is
for 1 second to 2 seconds. At that time The
Fingerprint Sensor can read new fingerprints as well
as registered fingerprints previously.
5 CONCLUSION
To be able to connect between the hardware and the
server must use the same network. which is the time
required for barcode reading ranges from 1 second to
3 seconds. The percentage of successful barcode
reading from a distance of 1cm to 10 cm is 66.11%.
and the distance that can be detected by the barcode
reader in reading the barcode on the student sign card
is at a distance of 5 cm to a distance of 10 cm.
Furthermore, the Fingerprint reader can read on all
registered fingers, be it the thumb, index, medium,
ring, and little fingers. Fingerprint reader can only
read fingerprints in a dry state. and Fingerprint reader
cannot print in wet condition. The time lag required
in reading the Fingerprint Sensor is in the range of 1
second to 2 seconds. The level of accuracy of the
fuzzy method implemented in the system is 99%.
REFERENCES
Warsito, E. (2022). "Studi Kasus Di Pondok Pesantren
Mahasiswa Khoirul Huda Surabaya,". Universitas
Islam Negeri Sunan Ampel, Surabaya.
Maulani, M. R., Julian, A., Hakim, L. L. (2018). "Rancang
Bangun Aplikasi Absensi Perkuliahan Berbasis Clien-
Server Menggunakan Tekzeroogi Rfid (Radio
Frequency Identification),". Jurnal Teknik Informatika.
Vol., X. No., 3. Pp., 12-16.
Fahmi, R. B. (2018). "Information System-Based
Automated Tutor Attendance Using Barcode Scanner
In International Boarding School Pesma Kh Mas
Mansyur,". Universitas Muhammadiyah Surakarta,
Surakarta.
Fadlil, A., Firdausy, K., Hermawan, F. (2008).
"Pengembangan Sistem Basis Data Presensi
Perkuliahan Dengan Card Mahasiswa Ber-Barcode,".
TELKOMNIKA. Vol., VI. No., 1. Pp., 65-72.
Rotikan, R. (2016). "Sistem Informasi Absensi Berbasis
Web Untuk Kegiatan Konferensi,". Jurnal Ilmiah
SISFOTENIKA. Vol., VI. No., 1. Pp., 46-55.
Fahreza, A. T. (2019). "Rancang Bangun Sistem
Autentikasi Penyewa Kamar Kos Menggunakan QR
Code Bebasis Iot,". Politeknik Negeri Medan, Medan.
Amin, F. N. (2016). "Timbangan Berbasis Arduino Dengan
Output Lcd Dan Suara,". Universitas Nergeri
Semarang, Semarang.
Fani, H. A., Sumarno, Jalaluddin, Hartama, D., Gunawan I.
(2022). "Perancangan Alat Monitoring Pendeteksi Suara
Di Ruangan Bayi RS Vita Insani Berbasis Arduino
Menggunakan Buzzer,". Jurnal Media Informatika
BUDIDARMA. Vol., IV. No., 1. Pp. 144-149.
Nugroho, K. (2016). "Model Analisis Prediksi
Menggunakan Metode Fuzzy Time Series,". Infokam.
Vol., I. No., 12. Pp., 46-50.
Suryono, E. (2019). "Perancangan Sistem Absensi
Fingerprint Berbasis Arduino Dengan Notifikasi
Telegram,". Universitas Kristen Satya Wacana,
Salatiga.
Silvia, A. F., Haritman, E., Muladi, Y. (2014). "Rancang
Bangun Akses Kontrol Pintu Gerbang Berbasis
Arduino Dan Android,". Electrans. Vol., XIII. No., 1.
Pp., 1-10. Yuliansyah, H. (2016). "Uji Kinerja
Pengiriman Data Secara Wireless Menggunakan Modul
ESP32 Berbasis Rest Architecture,". Electrician-Jurnal
Rekayasa Dan Teknik Elektro. Vol., X. No., 2. Pp., 68-
77.
iCAST-ES 2022 - International Conference on Applied Science and Technology on Engineering Science
958
