
Utilization of Social Media as Literature Media about Cybercrime
Anticipation: Descriptive Study on ”Malamtanpakata” Account
Fauziah and Anisa Pratiwi
Universitas 17 Agustus 1945 Jakarta, Indonesia
Keywords: Twitter, Thread, Tinder Swindler, Cybercrime.
Abstract: Social media Twitter is a social media that is currently popular again after it was previously popular in 2011.
With the presence of Twitter, an issue can become a viral phenomenon when it gets a lot of attention from
Twitter social media users. Through a thread on Twitter, the user could tell the story of the event and the
chronology in detail. One of them is the chronology of crimes that happen in the virtub bb cxal world, namely
lovescam which is currently called tinder swindler inspired by the Netflix series called "The Tinder Swindler".
Crimes in the world like tinder swindlers must also be exposed through social media, one of which is Twitter
with the feature it has, namely threads. The purpose of this research is to know how the user interacts with
Twitter in the thread of fraud by tinder swindlers on malamtanpakata account. Analyzing the data that the
researcher did is with the observation of each dialog for Twitter users that happened in the thread on
malamtanpakata account. From the analysis done on the case thread fraud tinder swindler generate traffic
information user twitter that is the basic pattern of communication conversation.
1 INTRODUCTION
The presence of the internet as a new media provides
an interactive communication channel and gives
freedom to its users. The internet also provides
advantages that can display text, audio, video to help
users think practically. The basic arrangement of the
internet and its users leads to the effect of social
division, but on the other hand unites in a different
way (Slevin, 2000 in McQuail, 2011:154). Online
media is a means to simplify and speed up conveying
messages in the communication process. Where the
communication process is the process of delivering
messages from the communicator to the
communicant through the media and giving rise to
feedback.
Online media facilitates interactive social
interactions from what was previously a monologue
media (one to many audiences) to social media
dialogue (many audiences to many audiences). One
form of online media is social media. Social media is
a convergence between personal communication in
which there are sharing activities between individuals
(to be shared one-to-one) and public media to share
with anyone without any individual limitations and
specificities (Meike and Yong, 2012). In the
development of the internet and online media, the
biggest change that can be found is the patterns of
communication interaction. This has changed the
order of communication between people, which
previously relied more on face-to-face interactions,
has now shifted towards the use of media, especially
the internet and cell phones.
The development of the internet and the media
gave rise to a new crime motive or what is commonly
called cybercrime. Various crimes can be committed
using communication technology including
defamation through the internet, gambling, terrorism,
credit card fraud, pornography and other forms of
crimes. According to Symantec's security in the
Internet Security Threat Report volume 17, Indonesia
itself is ranked 10th as the country with the most
cyber crimes throughout 2011. The increase in
cybercrime cases cannot be separated from the
increasing use of the internet and social media.
Criminals are increasingly using the internet and
social media to find victims.
There are many types of social media in
Indonesia, one of which is Twitter. Twitter itself is a
popular application that is widely used in Indonesia,
recorded by statista.com Indonesia occupies the fifth
position of the country with the most Twitter users,
following the graph reported from the statista.com
Fauziah, . and Pratiwi, A.
Utilization of Social Media as Literature Media about Cybercrime Anticipation: Descriptive Study on â
˘
A
˙
IMalamtanpakataâ
˘
A
˙
I Account.
DOI: 10.5220/0011976800003582
In Proceedings of the 3rd International Seminar and Call for Paper (ISCP) UTA â
˘
A
´
Z45 Jakarta (ISCP UTA’45 Jakarta 2022), pages 109-115
ISBN: 978-989-758-654-5; ISSN: 2828-853X
Copyright
c
2023 by SCITEPRESS – Science and Technology Publications, Lda. Under CC license (CC BY-NC-ND 4.0)
109

web page. Twitter is a microblogging application that
is very easy to use, Twitter provides a tweet feature
for its users so that they can share their moments
through writing with a maximum limit of 140
characters. This allows users to freely express their
opinions and write their thoughts through their
accounts and are free to be accessed by anyone. One
of the trends among Twitter users is the trend of
creating threads. (Nasrullah R, 2015:43)
A Twitter thread is a collection of serialized
tweets that are often used to share information
consisting of long paragraphs. Twitter itself provides
a limit of tweets with a maximum of 280 characters.
Then came the Twitter trend that provided a thread or
thread feature that could connect several tweets into a
single piece of information.
(https://www.idntimes.com/tech/trend/fajrina-
annisa-putri/cara-buat-thread-di-twitter, accessed on
15 June 2022 at 20:22)
As in the real world, social media that is accessed
using the internet also invites criminals to act, both
seeking material gain or just a form of fun from
someone. This gives rise to a phenomenon called
cyber crime or cybercrime. As in the case that
happened for some time experienced by the wordless
night account. On March 16, 2022 a twitter account
with the account name Malamtanpakata created a
thread about the case he was experiencing with the
thread headline 'HEART HATI TINDER
SWINDLER INDONESIA'. "Tinder Swindler"
which in Indonesian, translates as "swindler on
Tinder"
Current technological advances not only help
human activities but also become new opportunities
for cybercriminals to carry out their evil actions. In
cyberspace security issues. The high level of crime in
cyberspace and the weak legal handling of criminal
cases in cyberspace have led to rampant crimes that
occur in cyberspace. In addition to this, it will be
difficult to catch cybercriminals with technological
advances. Based on the description above, the author
is interested in conducting research on Twitter user
information traffic in the Tinder Swindler case
Thread.
2 LITERATURE REVIEW
Dennis McQuail in his book Mass Communication
Theory (2000: 136) said that new media is a different
set of communication technologies that have special
and up-to-date features. These features are made by
digitizing with various variations available for
someone to use as a communication tool.
McQuail said that the use of the internet in New
Zealand has provided entertainment and information
that has spread throughout the world and can connect
individuals from other parts of the world to be able to
communicate and interact socially without being
hindered by time and distance. McQuail (2000: 143)
also classifies new media into five categories,
namely:
a. Interpersonal communication media.
b. Interactive media, especially in the form of
computer-based games and video games
coupled with virtual reality devices.
c. Information search media in the form of search
engines.
d. Collective participating media, this category
specifically includes the use of the internet to
share and exchange information, ideas and
experiences as well as develop active personal
relationships whose medium is the computer.
In the internet there are also many social
networks whose users range from purely
instrumental to affective and emotional.
e. Substitute broadcast media, the main reference
is the use of media to receive or download
content where in the past the media type was
broadcast or with a similar distribution
method. Watching movie and television
programs, listening to radio and music, etc. are
examples of the main activities.
McQuail (2000: 141) sees that the main problem
in theory about new media, which is of course
different from the theory about (old) media that has
existed so far, revolves around three things. First,
power and inequality, it is very difficult to place new
media in terms of ownership and power where the
content and flow of information are controlled.
Second, social integration and identity, new media is
considered as a force to disintegrate social
cohesiveness in society because it is considered too
individualistic and can penetrate the boundaries of
space and time as well as culture. Third, social
change, new media is considered an agent of social
change as well as a planned agent of economic change
where there is no control over messages from both the
sender and the recipient of the message which is very
likely to occur.
Winston as the author of communication
innovation (McQuail, 2000:155) admits that most
new technologies have innovative potential, but their
actual implementation will always depend on two
factors. The first factor is the “social necessity”
operation which dictates the degree and form of
development of many new inventions. The second is
the “law of suppression of radical potentials” which
ISCP UTA’45 Jakarta 2022 - International Seminar and Call for Paper Universitas 17 Agustus 1945 Jakarta
110

acts as a brake on innovation to protect the social and
corporate status quo. many theories of “culture”
rather than technological determination. Carey (1998)
takes a similar position regarding “new media”,
arguing that “globalization, the Internet and computer
communications are not all industry or history
determined. The final determination of all these new
forms is prepared by politics.
Social media has the character of a social network.
Social media is formed from social structures that are
formed in networks or the internet (Nasrullah Rulli,
2015:17). Social media forms a network among its
users. It doesn't matter whether the real world
(offline) of these users know each other or not. The
network forms a community of people who
consciously or unconsciously raises values in society
as the characteristics of society in social theories. One
of the social media is Twitter. the presence of Twitter,
a web 2.0 service with the type of micro-blog where
users are limited to writing as many as 140 characters.
Twitter can be freely accessed from both users and
non-users. The advantage of this twitter is a speed in
informing an information and of course fast in
acceptance.
3 METHODS
Qualitative research is based on the philosophy of
positivism, because to examine natural subject
conditions where the researcher is the key instrument,
sampling of data sources is carried out purposively
and snowball, collection techniques are triangulation
(combined), data analysis is inductive/qualitative, and
qualitative research results emphasizes meaning
rather than generalization (Sugiyono, 2011).
3.1 Research Target
Subjects and objects of research are targets to obtain
certain goals regarding an issue which will then be
proven objectively. Understanding the subject and
object of research according to Sugiyono (2013: 32)
is as follows: "The subject of research is an attribute
or nature or value of people, objects or activities that
have certain variables that are set to be studied and
drawn conclusions."
So the research subject is considered very
important in a study, this relates to the title of the
study and the data that will be needed. In addition to
the research subject, the object in the study is no less
important because the object of research is used to
obtain data according to a particular purpose. The
subject of this research is Twitter users in the thread
of the Tinder Swindler case and the subject of the
research is the interaction pattern of Twitter users on
the thread of the Tinder Swindler case.
3.2 Place and Time of Research
This research was conducted in North Jakarta, with
the main focus being the owner of the Malam without
a word account who uses Twitter as a medium for
posting threads of the fraud case by Tinder Swindler
that he experienced. The time of the study was carried
out for three months from May to July.
3.3 Research Focus
The focus of this research is intended to limit
qualitative studies while at the same time limiting
research in order to choose which data are relevant
and which are irrelevant (Moleong, 2010). The
limitations in this qualitative research are based on
the level of importance/urgency of the problems
encountered in this research. This research will focus
on “Information Traffic in the Twindler Swindler
Fraud Case Thread on Twitter Social Media” whose
main object is Twitter users in the Twindler Swindler
fraud thread by the “malamtanpakata” account.
3.4 Data Collection Technique
In this study, primary data was obtained directly from
the conversations of Twitter users on threads created
by the Malam without words account. The secondary
data used in this study is the online news
MetroPalembangNews, Detikcom, HarianKompas
and wowkeren. In this observation, the researcher
aims to record or describe the behavior of the object
and understand it. Observations will be made on the
thread of the Swindler Tinder case on the "wordless
night" account on the Twitter application.
The research that will be conducted by researchers
uses descriptive research methods with a qualitative
approach. According to Sugiyono (2016:9)
qualitative descriptive method is a research method
based on post-positivism philosophy used to examine
the condition of natural objects (as opposed to
experiments) where the researcher is the key
instrument of data collection techniques carried out
by trigulation (combined), analysis the data are
inductive or qualitative, and the results of qualitative
research emphasize meaning rather than
generalizations. (Heckman, Pinto and Savelyev,
1967)
Utilization of Social Media as Literature Media about Cybercrime Anticipation: Descriptive Study on â
˘
A
˙
IMalamtanpakataâ
˘
A
˙
I Account
111

4 RESULT AND DISCUSSION
Twitter is a web microblogging service that can be
used to update (update) in the form of a text with a
maximum length of 280 characters, or commonly
called a tweet. Updates that we make can be seen by
other people who are our followers if the Twitter
account is not locked. Broadly speaking, the function
of Twitter is to write down the current activity;
sharing links, videos, songs, and pictures; make new
friends in cyberspace; as an advertising medium; as a
medium of real-time information; and even as a
medium for political support activities or campaigns
(Juju & Studio, 2009).
4.1 Tinder Swindler in Cybercrime
The development of technology at this time is like a
sharp sword, meaning that today's information
technology contributes a lot to social change,
progress, and human civilization. However,
information technology can also be used as a means
to be able to commit acts against the law. This fact
triggers a new phenomenon known as cybercrime. At
this time, the more social media that is accessed by
the public, the higher the threat of crime that can arise.
This is of course common, especially in online dating
sites. Romance scams are usually carried out in a
fraudulent mode where the fraudster takes advantage
of someone who is indeed looking for a partner,
usually through an online dating application by
pretending to be a potential partner. Where these
fraudsters play with the feelings of their victims so
that they can easily give money or anything to them.
This type of fraud committed by romance scammers
can be done based on two things. First, the scammer
will seduce until the victim is deceived and seeks
profit from the victim in the form of money. Second,
the scammer will persuade the victim to send a private
photo, which will then be used to threaten the victim
with the threat of spreading the photo.
4.2 Communication Archetype
Analysis
New media or also called new media is a series of
communication technologies that have several new
features, through digitization and are widely available
to personal users as a complete set of communication
tools. The speed of new media is also supported by
the rapid development of communication technology
which is increasingly advanced, proving that
communication media has a dynamic nature that is
not fixed all the time. McQuail (2000:141) argues that
the main problem in the theory of new media, which
is of course different from the old media theory,
which has three main things, namely power and
inequality, social integration and identity and social
change. Power and Inquality, namely constraints on
the placement of new media in relation to ownership
and power in which the content and flow of
communication for the exchange of information must
be controlled.
4.3 Conversation Analysis
Conversation talks about conversation, individuals
interact with other individuals by choosing partners,
topics of conversation, time and place of
communication according to their wishes. This sub-
discussion will describe the basic pattern of
conversational communication regarding cases of
fraud that occurred in online dating applications by
nightless twitter users. In this description, the
researcher will describe the beginning of the fraud
experienced by the wordless night until the arrest of
the perpetrator of the fraud. Overall, postings from
twitter users in the thread created by night without
words foster the attitude of twitter users willing to
help night without words as victims of voluntarily
uncovering cases of fraud.
The thread created by night without words is
crowded with posts by twitter users who provide
information related to the fraud case. In this basic
pattern of conversational communication, it will be
seen how twitter users interact with each other with
topics of conversation regarding fraud cases that
occur in online dating applications, with the time and
place of communication according to the wishes of
twitter users.
From the interaction of twitter users, most of the
posts in the thread contain support and progress
reports from twitter users in an effort to reveal this
tinder swindler case. Interactions that occur in the
forum, twitter users provide reports on the progress of
arrests made by providing information and gathering
evidence related to the tinder swindler case. With the
cohesiveness and well-established interaction
between twitter users in collecting information and
evidence of disclosure of this fraud case, it is hoped
that the case can be resolved soon and there will be
no more tinder swindler cases that afflict online
dating application users.
4.4 Allocution Analysis
In this pattern, we will describe the basic pattern of
allocution communication in fraud cases that
ISCP UTA’45 Jakarta 2022 - International Seminar and Call for Paper Universitas 17 Agustus 1945 Jakarta
112
occurred in the online dating application by James
Daniel Sinaga and the owner of the Malam without a
word account. Allocution is information that is
distributed from the center simultaneously with
limited opportunities to get feedback. Allocution
communication template to see how information
about fraud cases in threads by wordless night
accounts is distributed simultaneously.
After reading all threads related to fraud cases that
occurred on Twitter social media by paying attention
to posts from twitter users, the researcher concluded
that this fraud case was known by twitter users when
a twitter user with the account name Malam without
words created a thread entitled "HEART HATI HATI
TINDER SWINDLER VERSI INDONESIA". In this
basic pattern of communication, it will be seen that
information is distributed from the center
simultaneously which the researcher will describe as
follows.
A twitter user with a wordless night account
created a thread that tells the chronology of being
tricked by his online dating friend who claims to be
named James Sinaga. Night without a word admitted
that he was close to the perpetrator so he wanted to
send some money to James to an account named
Ramdani who was recognized as his assistant. The
thread created by the twitter user Malam without
words is an Alloculation, namely information that is
conveyed simultaneously because of his concern for
the fraud experienced by the twitter user and himself.
With the thread created by the wordless night twitter
user through the online media Twitter, information is
conveyed simultaneously but with limited feedback.
Besides that, the thread created by the twitter user
Malam without words, in addition to providing
information to other twitter users about the rampant
fraud through online dating applications, but also to
seek information about the whereabouts of the
perpetrator James Sinaga.
Based on the description that has been described
above, the researcher can analyze that the post made
by Malam without words initially had a good
relationship with James Sinaga until his post after the
fraud of a sum of money and the disappearance of
James Sinaga was a form of information that was
conveyed simultaneously as a form of sharing his
experiences so that this would not happen. happened
to other twitter users. The tendency of posts made by
night without words is to lead to efforts to appeal to
other twitter users against James Sinaga.
4.5 Analysis Consultation
The basic pattern of communication consultation
refers to a variety of different communication
situations where an individual seeks information
through the information source he or she wants. In
this fraud case, the collection of information related
to the fraud case with the alleged perpetrator James
Sinaga is not only from the Malam without words
account, but other twitter users can provide
information related to the fraud case. In addition, the
collection of information and evidence by the
kaskuser was also obtained by twitter users from the
community who could provide information about this
case which was then posted in the thread created by
the Malam without a word account.
In this sub-discussion, the researcher will describe
the basic pattern of consultation communication,
which is as follows:
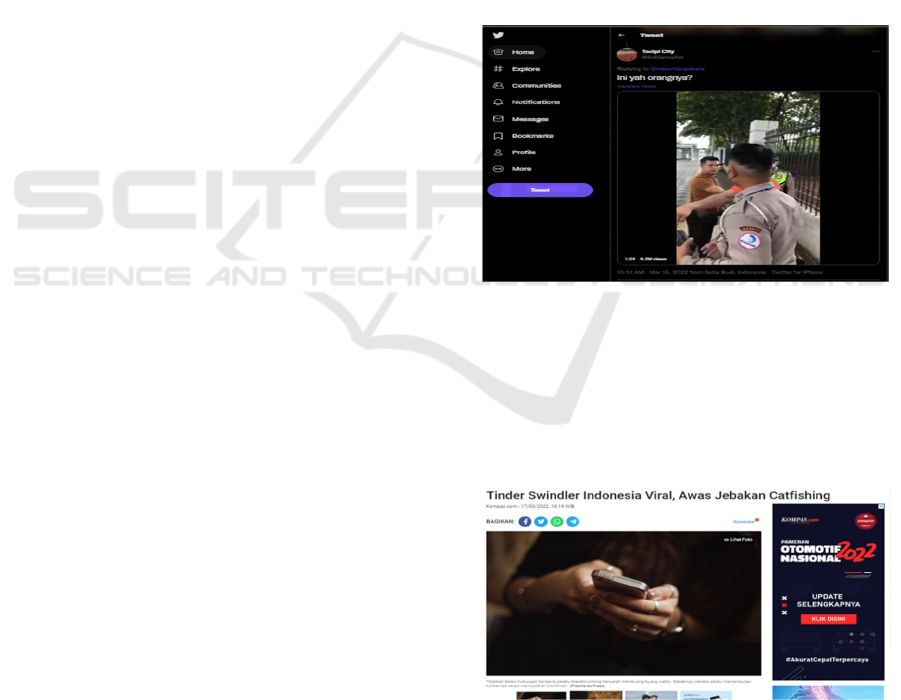
Figure 1: Twitter AsbianSabi.
Based on the picture above, it was presented by
Twitter user AsbianSabi on March 16, 2022, he
posted a video of someone who looks like the
perpetrator being chased by a security guard and a
man. The post can be seen in the comments session in
the thread posted night without a word.
Figure 2: Kompas.com News.
Utilization of Social Media as Literature Media about Cybercrime Anticipation: Descriptive Study on â
˘
A
˙
IMalamtanpakataâ
˘
A
˙
I Account
113

Figure 3: malamtanpakata Account.
Based on the picture of the fraud case by the
Indonesian version of the Tinder Swindler with the
alleged perpetrator James Sinaga or Daniel Sinaga or
Ramdani on kompas.com online media on March 17,
2022. In the news, a thread from the twitter account
“malamtanpakata” is also attached.
4.6 Registration Analysis
This pattern of information traffic is termed
“registration”, which is a reversed consultation
pattern, where a center “requests” and receives
information from participants at the periphery. In this
study, the basic pattern of wordless night account
registration communication as a thread maker also
requests and receives information from twitter users.
This can be seen from the communication that took
place in the discussion forum on the thread created by
the Malam without a word account. The night account
without words received various information and
evidence in the disclosure of fraud cases that occurred
by the perpetrators from twitter users who posted in
their thread. Various information was received by the
wordless night because of the cooperation and good
communication between the wordless night and the
twitter users. By receiving a lot of information from
various sources provided by twitter users, Malam
without words hopes that this case of fraud by Tinder
Swindler can be uncovered.
Creating a special thread regarding the fraud by
Tinder Swindler, is the goal of Malam without words
to receive information from Twitter users as an effort
to reveal the fraud case they experienced. So that in
this study there is also registration information traffic,
where Malam without words as the central
communicator receives various information related to
the fraud case from Twitter users who obtain
information from various sources and who conduct
direct investigations at the place where the fraud
perpetrator is domiciled.
Based on the basic pattern of communication
consultation in this study refers to a variety of
different communication situations where individuals
seek information through the desired information
source. In this case, the information obtained
regarding the fraud case by Tinder Swindler with the
alleged perpetrator James Sinaga was not only
obtained from twitter users.
The information obtained also comes from other
sources, which in this case is through print media
coverage obtained from Kompas.com and twitter
users who have been looking for information obtained
from other parties as well as direct investigations at
the location of James Sinaga's original domicile. The
information submitted by a twitter user with the id
AbisanAbi is an illustration of the arrest of James
Sinaga who was at the scene of the case to conduct an
investigation. With the information obtained by
AbisanAbi, then the information was posted on the
thread created by Malamtanakata.
While the basic pattern of registration
communication, based on a thread by a wordless night
account, is described that a center "requests" and
receives information from participants at the
periphery. In this study, the night without words
account as a thread creator and a pioneer in disclosing
fraud cases that occurred in online dating applications
received information from twitter users regarding the
disclosure of the fraud case. With the thread created
by night without words, is a special thread used by
twitter users as a discussion forum to provide
information and evidence related to fraud by tinder
swindler, so night without words receive information
from twitter users through the thread that has been
created.
5 CONCLUSIONS
Online media in the realm of buying and selling
online will become the object of cybercrime crime,
for that people in the digital world are required to
understand not only conventional crimes in online
media, but also crimes involving information
technology (cyber crime) in online media. The modes
and motives of cyber crime are increasingly complex
and therefore there is no guarantee of security in
online media.
The thread created by Malam without words
regarding cyber crimes that occur in online dating
applications is a form of concern for helping victims
of fraud from the alleged perpetrator James Sinaga,
ISCP UTA’45 Jakarta 2022 - International Seminar and Call for Paper Universitas 17 Agustus 1945 Jakarta
114

so that it is hoped that there will be no more fraud that
occurs by Tinder Swindler.
Through the thread created by Malam without
words in disclosing the fraud case he experienced
which is supported by twitter users who are willing to
help victims voluntarily give a positive image to
twitter users, if twitter users also have a sense of
caring to help each other even though they don't know
each other and have met before.
The basic pattern of communication of twitter
users in disclosing fraud cases by Tinder Swindler is
known that the most influential communication
interaction patterns are allocution and conversation.
In the basic pattern of allocution communication,
information is distributed from the center
simultaneously by the night without a word as the
thread creator.
The basic pattern of communication is
conversation, where twitter users interact with other
twitter users with the topic of fraud committed by
tinder swindler actors, with the time and place of
communication according to their wishes. With the
basic pattern of communication, it was able to
uncover cases of fraud with the alleged perpetrator,
namely Ramdani, although in the execution of the
arrests, the twitter users left it to the authorities to
follow up
.
REFERENCES
Nasrullah Rulli, (2015) Media Sosial Perspektif
Komunikasi, Budaya dan Sosioteknologi. Simbiosa
Rekatama Media. Bandung.
Nurudin, (2017) Perkembangan Teknologi Komunikasi.
Rajawali Pers. Depok.
Syam Nina W, (2013) Model Model Komunikasi Perspektif
Pohon Komunikasi. Simbiosa Rekatama Media.
Bandung, 2013.
Abdul Wahid, Mohammad Labib. 2010. Kejahatan
Mayantara (Cyber Crime ). Refika aditama. Bandung.
Sugiyono, (2014) Metode Penelitian Pendidikan
Pendekatan Kuantitatif, Kualitatif, dan R&D. Alfabeta,
Bandung.
Anggito Albi&Setiawan Johan, (2019) Metode Penelitian
Kualitatif. Sukabumi CV Jejak.
Francis P. Barclay dkk, Twitter Sentiments: Pattern
Recognition And Poll Prediction, Communication and
Information Technologies Annual, 24 Februari 2016,
143
Prayudani R Desyanti, Penipuan Melalui Aplikasi Biro
Jodoh Pada Tinder (Studi Kasus Terhadap Putusan
Pengadilan Negeri Surabaya Nomor
2412/Pid.B/2020/PN.SBY), Dinamika, Januari 2022,
28: 3869
Judhita Christiany, Pola Komunikasi Dalam Cybercrime
(Kasus Love Scams), Balai Besar Pengkajian dan
Pengembangan Komunikai dan Informatika (BBPPKI),
2015
Fauzianti A Nizda dkk, Catfishing dan Implikasinya
terhadap Romance Scam oleh Simon Leviev dalam
Dokumenter Netflix ‘The Tinder Swindler’ Menurut
Perspektif Undang-Undang Nomor 11 Tahun 2008
tentang Informasi dan Transkasi Elektronik dan Kitab
Undang-Undang Hukum Pidana, Padjadjaran Law
Research & Debate Society, 2022, 10: 1
Hapsari T Dian, Fenomena Caption “Twitter, Please Do
Your Magic!” Membangkitkan Netizen Untuk
Menolong. Journal of Digital Education,
Communication and Arts, Maret 2020, Vol 3 30-3
Internet
https://era.id/megapolitan/45034/modus-kencan-online-
wanita-ini-ditipu-hingga-rp15-8-miliar-kok-bisa
https://www.merdeka.com/jabar/pria-asal-afrika-ini-tipu-
pacar-warga-negara-indonesia-hingga-rp15-m-begini-
kronolog.html
https://ihpi.umich.edu/building-twitter-thread-more-impact
https://www.idntimes.com/tech/trend/fajrina-annisa-
putri/cara-membuat-thread-di-twitter
https://tekno.kompas.com/read/2022/03/18/13450047/apa-
itu-tinder-swindler-yang-ramai-di-twitter-
https://www.statista.com/statistics/242606/number-of-
active-twitter-users-in-selected-countries
https://www.twitter.com/malamtanpakata
Utilization of Social Media as Literature Media about Cybercrime Anticipation: Descriptive Study on â
˘
A
˙
IMalamtanpakataâ
˘
A
˙
I Account
115
